
Hackers are always on the move, finding weaknesses in systems, and creating exploits to target people and steal data.
And this time, researchers at Intezer Lab and The BlackBerry Research & Intelligence Team have discovered a unique, and "nearly-impossible-to-detect" Linux malware named 'Symbiote' that is being used to target financial institutions across Latin America.
The researchers warned that the malware can steal user credentials and provides threat actors with remote access to Linux systems.
Furthermore, hackers using the malware and managed a successful breach, can allow them to add rootkit functionality to exploit even more of the target's system.
Just like the Marvel's Symbiote, which is often regarded as a "parasite," the Symbiote malware is capable of infecting all of a Linux system's running processes in a parasitic manner, but at the same time, is also able to live in symbiosis with its host.
Infected hosts will behave just like normal, while the malware stays inside, stealing data.
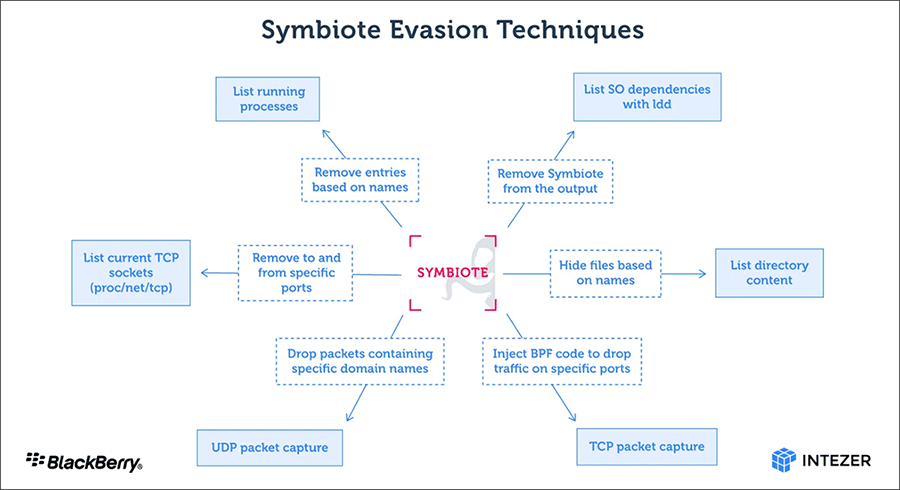
The Symbiote is able to do this using the BPF (Berkeley Packet Filter) to hide its communication channels from security tools, while hooking its functionality to sniff network data packets.
The malware is also able to avoid security measures by not having a typical form of an executable.
Instead, Symbiote uses a shared object (SO) library that gets loaded into running processes using the LD_PRELOAD directive to gain priority against other SOs.
By being the first to load, Symbiote can hook several functions and perform various actions.
These include concealing its presence, hiding its parasitic processes, hiding all files deployed with the malware, and more.
And to also hide its malicious network activity on the compromised machine, Symbiote scrubs connection entries it wants to hide by also removing UDP traffic to domain names in its list.
According to the researchers, Symbiote has been under active development since at least 2021.
According to the researchers from BlackBerry in a blog post:
And according to the researchers at Intezer in their own blog post:
As a properly stealthy malware, Symbiote is being deployed for automated credential harvesting from hacked Linux devices.
The way it works makes it capable of targeting Linux servers in high-value networks, capable of stealing administrator account credentials to further open more ways for an unobstructed movement throughout a compromised system, by granting the hackers unlimited access to the entire system.
This is also possible because the Symbiote also gives its operators remote SHH access to the machine via the PAM service, and provides the hackers root privileges on the system.
"Since the malware operates as a user-land level rootkit, detecting an infection may be difficult," the researchers concluded. "Network telemetry can be used to detect anomalous DNS requests and security tools such as AVs and EDRs should be statically linked to ensure they are not 'infected' by userland rootkits."
When it was found, Symbiote's targets are mostly entities engaging in the financial sector in Latin America.
There, hackers plant Symbiote by impersonating Brazilian banks, the country's Federal police, etc..
