To most people in this world, their only way to browse the web is by using a web browser.
All major operating systems come with their own web browsers. For those users who wish to use other web browsers, can simply download them from the browsers' official website, install them, and have the web under their disposal.
Hackers know this very well.
It's revealed that hackers have been targeting macOS users with a malware called the Atomic macOS Stealer (AMOS), which poses a significant threat to Apple users.
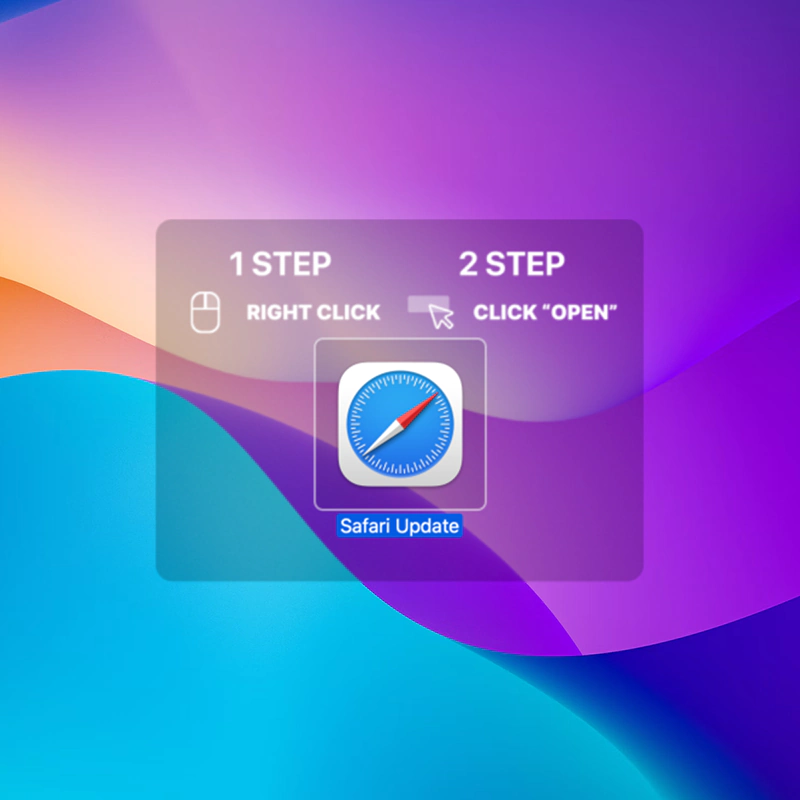
The hackers target macOS users by distributing fake Safari and Chrome browser updates for Mac computers.
When unsuspecting victims failed for the fake updates, AMOS can compromise device security and steal sensitive information.
The malware is being distributed though a campaign dubbed the 'ClearFake'.
At first, the campaign began in July 2023, targeting Microsoft Windows users with a fake Google Chrome update that appears on websites hackers breached through JavaScript injections.
In October, Guardio Labs reported that the campaign has undergone a significant development in its operation.
It was realized that the hackers behind the campaign started leveraging Binance Smart Chain contracts to hide its malicious scripts supporting the infection chain in the blockchain.
Through the method called "EtherHiding," the hackers were found distributing Windows-targeting payloads, including information-stealing malware like RedLine, Amadey, and Lumma.
It was then on November 17, that threat analyst Ankit Anubhav reported that ClearFake had started pushing DMG payloads, meaning that they started targeting macOS users who happen to visit compromised websites.
To target macOS users, according to a report by MalwareBytes, the campaign employs a Safari update bait along with the standard Chrome overlay.

AMOS comes from the term 'Atomic', a malware first discovered in April by Trellix and Cyble.
The malware in question is able to steal passwords, cookies, and credit cards stored in browsers, local files, data from over 50 cryptocurrency extensions, and keychain passwords.
The powerful info-stealing malware sold is sold to cybercriminals through a business model called the Malware-as-a-Service, distributed through Telegram channels for $1,000/month.
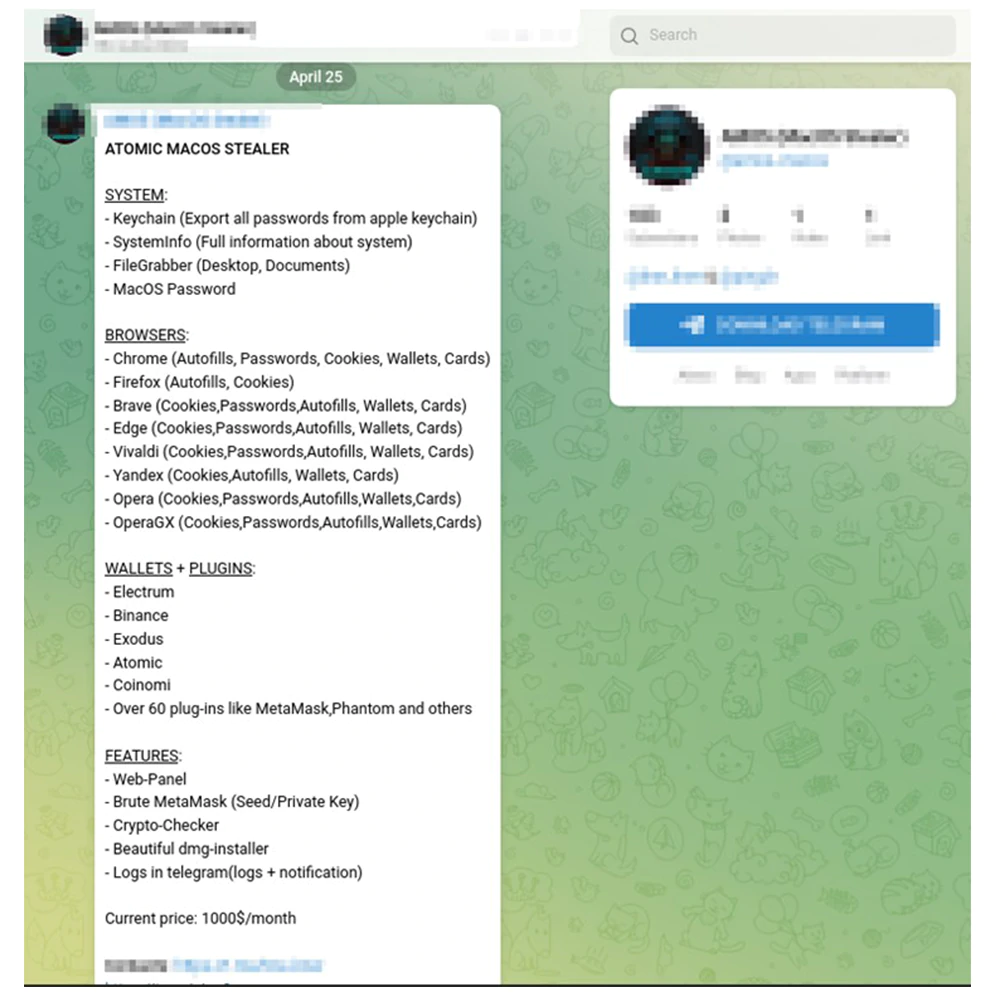
Upon infecting a macOS computer, the malware will start collecting relevant device data, like Mac model name, UUID, CPU, RAM, OS version, and so on. Atomic can obtain a wide variety of information from compromised devices, and can even requests permission to access the Desktop and Documents, from which it can then download victims' files.
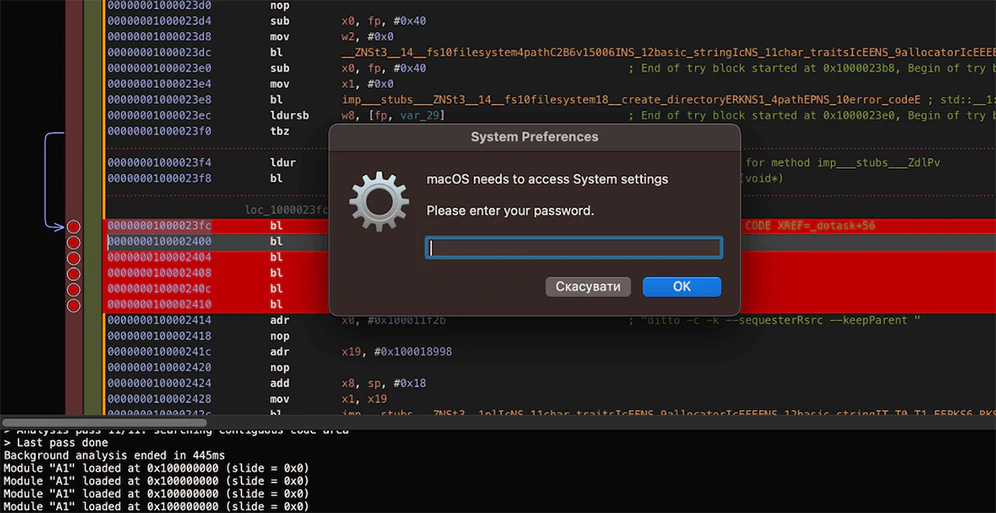
But the most damaging is how it can also ask for victims' Keychain password.
On macOS computers, Keychain is essentially a built-in password manager that holds sensitive information that can include and not limited to: Wi-Fi passwords, website login credentials, credit card data, and other encrypted information.
What this means, once victims typed in their Keychain password, it could translate to the a significant catastrophe.
It's worth noting that the Atomic malware is a sophisticated malware that is able to properly hide itself.
According to reports, even after several months following the discovery and reports on Atomic, the payload is still undetected by roughly 50% of antivirus engines on VirusTotal.
It's worth noting that any update to the Safari browser updates is distributed through macOS's Software Update, or for other browsers, within the browser itself. So prompts that pop up elsewhere should be ignored
Mac users can protect themselves by only downloading updates from official sources, and no where else.
