
Malware can have many forms and types, with the next ones more annoying that the ones before. But this one is kind of different.
In a report from security experts from fraud management firm Cleafy Labs, cybercriminals are utilizing a malware to attack Android users. Using the malware, the attackers can steal money from banking accounts.
The malicious software the researchers called the 'BRATA', allows hackers to monitor bank transactions and collect sensitive information.
The malware is thought to only attack Android operating systems at the moment of finding, they explained.
But things don't stop there, as the malware also has another trick under its sleeves.
And that is remote wiping the entire phone when it is done stealing.

BRATA is a banking trojan that has been around since at least 2018, and was first documented in a post from security firm Kaspersky.
At its initial state, it spread primarily through Google Play Store and third-party Android app markets, to infect victims through push notifications on compromised websites, sponsored links on Google, and messages delivered by WhatsApp or SMS.
According to the cybersecurity experts at Cleafy, the BRATA malware was first detected in Brazil, before seen moving out to South America, and beyond to target people in the UK, Poland, and Italy.
Short for "Brazilian Remote Access Tool Android," BRATA evolved from just a simple malware targeting people in specific areas, to then become a capable and feature-backed banking trojan.
Since then, the malware has received even more upgrades and changes.
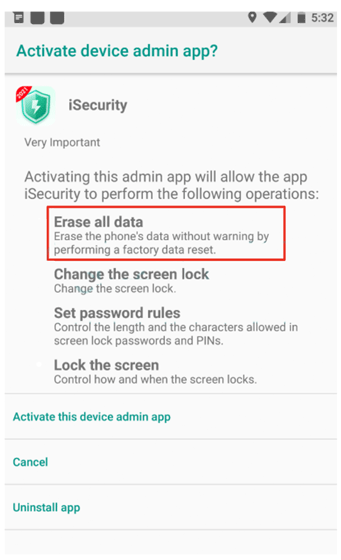
Besides having the abilities to steal money from banking apps and evade detection, the malware has been updated to have a kill switch that performs a factory reset to wipe infected devices clean.
It does this by requiring victims to grant it permission.
This function is executed in two cases:
- A bank fraud has been completed successfully. By performing a factory reset, victims are going to lose even more time before understanding what had happened.
- The application is installed in a virtual environment. BRATA tries to prevent dynamic analysis through the execution of this feature.
While malware having a feature to wipe phones clean is not very common, BRATA is just like any other malware observed in the wild, which abuses Android's permissions obtained during the installation phase to do what it needs to do.
According to the researchers at Cleafy, the malware also include GPS tracking, communication with control servers, the ability to continuously monitor bank apps, and the ability to target the accounts of banks located in additional countries.
"BRATA is trying to reach out to new targets and to develop new features," the researchers said, adding threat actors are "leveraging this banking trojan for performing frauds, typically through unauthorized wire transfer (e.g., SEPA) or through Instant Payments, using a wide network of money mules accounts in multiple European countries," the researchers said.
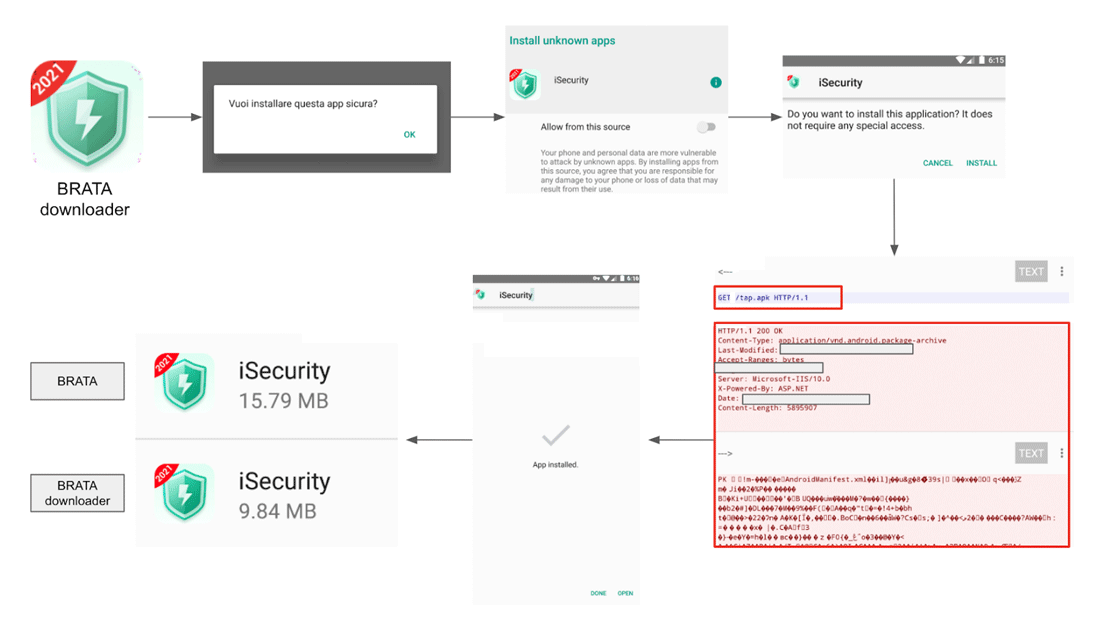
It's worth noting that BRATA is composed of an initial dropper that can be used to download and execute the "real" malicious app later.
"After the victim installs the downloader app, it requires accepting just one permission to download and install the malicious application from an untrusted source," the researchers said.
"When the victim clicks on the install button, the downloader app sends a GET request to the C2 server to download the malicious .apk. At this point, the victim has two malicious apps installed on their device."
BRATA and its updated features underscore the ever-evolving behavior of crimeware apps.
With malware authors becoming smarter and more experienced, Android phone users should remain wary of malicious malware by limiting the number of apps they install, and only grant the permissions that are needed for a trusted app to run.
Android users need to ensure that all apps they download and install come only from trustworthy sources.
Read: This Malware Is A Rare Instance Of 'Rooting Malware' That Exploits Android Weaknesses