
Two of the most popular operating systems for desktop computers, are Microsoft Windows and Apple's macOS.
While it's more common to hear that Windows users are targeted by malware, that doesn't mean users using macOS are safe. There is always a chance that a malware can be made to target different platforms to target different users.
And this time, that's exactly the case.
Researchers have discovered an advanced, never-before-seen macOS malware that spread using exploits that were almost impossible for the victims to detect or stop.
The malware that is dubbed the 'DazzleSpy', uses the watering-hole attack, in which the attackers compromise websites that are likely to be visited by a particular target group, rather than attacking the target group directly.
Once installed, the malware that comes with a full-featured backdoor provides an array of advanced capabilities, granting the attackers the ability to fully monitor and control infected Macs.
It all began back in November 2021, when Google TAG published a blog post about watering-hole attacks leading to exploits for the Safari web browser running on macOS.
ESET researchers that were already investigating this campaign the week before that publication, found that the malware uses a WebKit exploit.
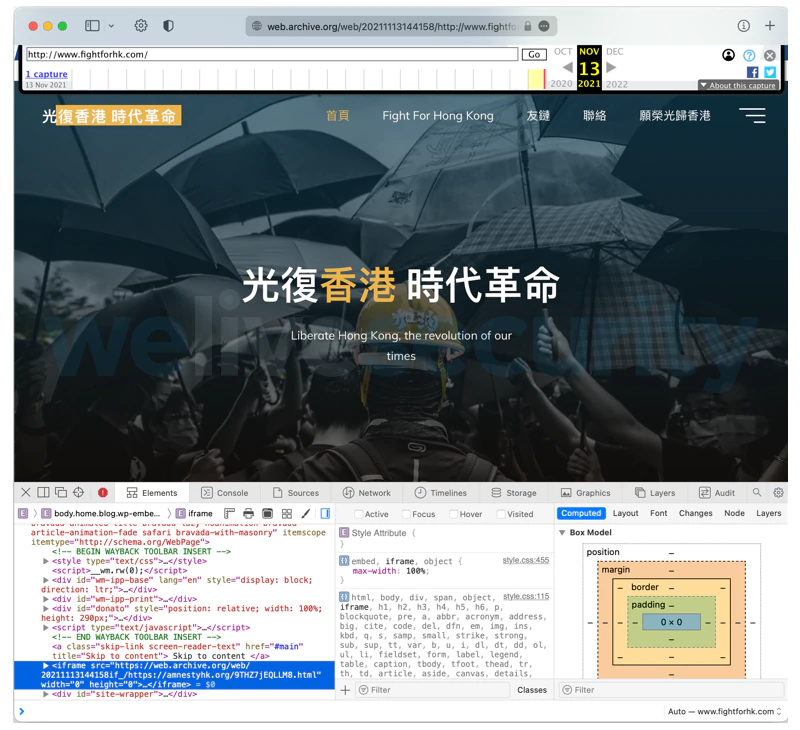
It was first reported in a tweet by Felix Aimé from SEKOIA.IO, that one of the websites used to propagate the exploits was a fake website targeting Hong Kong activists.
Using that cue, ESET researchers scouted to find another website.
Unlike the first one, the website they found is legitimate but compromised. And because the attackers have control of it, the website also distributed the same exploit during the few months prior to the Google TAG publication
According to the researchers, both distribution methods have something in common: they attract visitors from Hong Kong.
Through the watering-hole attacks, the attackers can target only a specific demographic, and in some cases, they can also target people so narrow, even in the range of specific IP addresses.
And in this case, not only that the attackers target people in Hong Kong, but they also target those with pro-democracy sympathies, and in particular, targeting freedom of speech advocates, independence, and political activists in Hong Kong.
When installed, the malware uses the WebKit exploit to gain code execution in the victims' Safari browser.
The exploit implements two primitives to gain memory read and write access.
The first is to leak the address of an object and the second is to create a fake JavaScript object from a given memory address. Using these two functions, the exploit creates two arrays of different types that overlap in memory, allowing the attackers to set a value in one of them that is treated as a pointer when accessed using the other.
As a result, the JavaScript engine in Safari erroneously speculates that the value of the property is cached in an array and is not the result of calling the getter function.
The malware uses malicious iframe that points to a domain that checks the macOS version and redirects to the next stage, which loads the JavaScript code exploit.
The code being used is complex, and had more than 1,000 lines of code that is formatted nicely.
The payload of this DazzleSpy malware, include what's called the MACMA, which is able to that fingerprint victims’ devices, grab screen captures, upload and download files, execute terminal commands, and commit tp spying via audio recording and keylogging.
Based on the researchers' analysis. this DazzleSpy is considered a new malware family targeting macOS users.
Written from scratch, the researchers concluded that the developers behind it may have significant resources and expertise.
The researchers at ESET confirmed that the DazzleSpy is part of the same operation that Google disclosed, which leveraged Chrome and Windows zero-days to hack into both Windows and Android devices.
"We have confirmed that the patch identified by Google TAG does fix the vulnerability," said the researchers at ESET.
"While it is possible this vulnerability was assigned CVE-2021-1789, we couldn’t confirm due to the lack of publicly available technical details. Below we outline our understanding of how the vulnerability affects Safari versions prior to 14.1."