
Malware comes in many forms, and each can be unique. This makes it very difficult for security products because there is no one approach fits all solution.
Microsoft has what it calls Microsoft Defender Advanced Threat Protection (ATP), which is an enterprise endpoint security platform.
The security solution from Microsoft is designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. And this time, it's having a new detecting capability which makes it even smarter.
Microsoft calls is the endpoint detection and response, or 'EDR in block mode' capability'.
Initially available in public preview, the mode uses behavioral blocking to block and contain malware, malicious attacks, and malicious artifacts following post-breach detection or if they're missed by the main antivirus solution.
In a blog post, senior program manager Shweta Jha said that:
"The ability of this feature to detect and stop threats in real-time, even after they have started running, empowers organizations to thwart cyberattacks, maintain security posture, and reduce the manual steps and time to respond to threats."
The security feature which works with Windows 10 and Windows Server 2016 or later, enables Microsoft Defender ATP to kill all related processes on endpoints where a malicious behavior is triggered.
EDR in block mode works in the background in order to remediate any malicious artifacts detected post-breach.
This works even if Microsoft Defender Antivirus is not chosen by users as their primary antivirus solution.
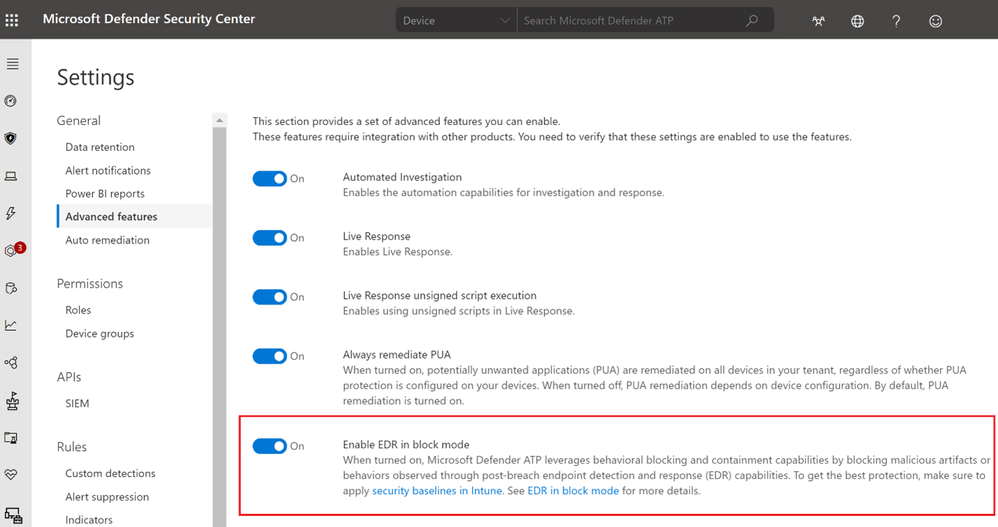
To turn this feature on, users need to sign in into Microsoft Defender Security Center, go into Settings and select Advanced features, to then toggle the 'Enable EDR in block mode' option.
It should be noted that EDR in block mode requires Global Administrator or Security Administrator permissions and cloud-delivered protection to be enabled.
These requirements are needed before users can make use of Microsoft's updated behavioral and device learning models.
And since the feature is initially introduced as a public preview feature, users need to first turn on the preview features in Microsoft Defender Security Center.
Jha also shared an example of how this behavioral-based threat containment feature works in action:
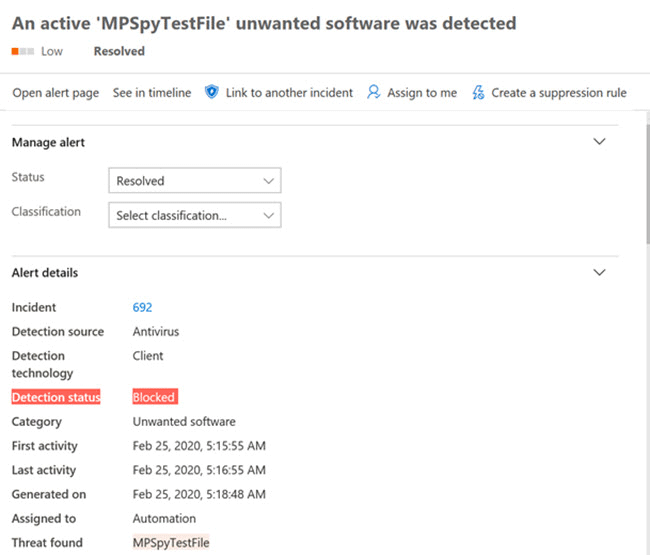
- In April 2020, the EDR in block mode protected and blocked a NanoCore RAT attack that aimed to steal credentials, spy using a device’s camera, and pilfer other information.
The attack started with a spear-phishing email carrying a malicious Excel attachment. The Excel file contained a malicious macro that, when enabled, ran a PowerShell code that in turn downloaded and ran a malicious file.
- The organization’s non-Microsoft antivirus solution didn’t detect the Excel file or its behavior, but Microsoft Defender ATP did.
When EDR in block mode kicked in, stopping the download behavior and blocking the PowerShell code and Excel file. This was reported in the Microsoft Defender Security Center, alerting the security team about the blocked behavior. While the threat was automatically remediated, the alert empowers the security team to perform additional investigation and hunting for similar threats.
Had the attack been allowed to continue, the downloaded malicious file would have run the following PowerShell commands, which would have downloaded the payload, a NanoCore variant.
"EDR in block mode was developed in close collaboration with customers, and is in public preview starting today," Jha added.
"We thank our customers for the partnership and for the invaluable feedback during the limited preview, during which the feature blocked multiple real-world attacks."
