Phones that are switched off, should be off, right? Wrong.
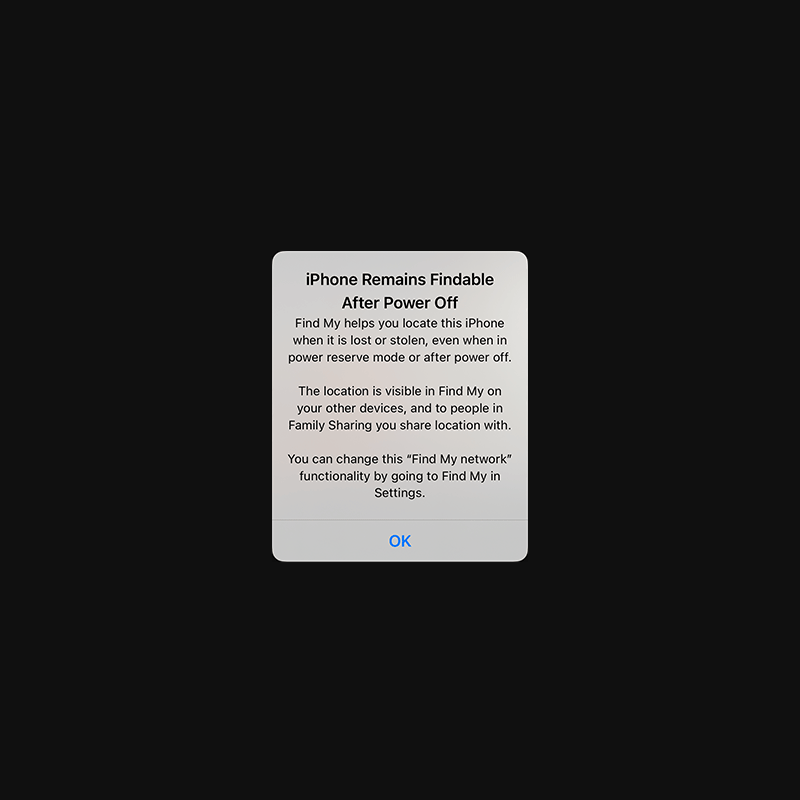
In the modern days of tech and mobile, off doesn't necessarily mean that it's really off. There is a reason for this, and that reason is by design. For example, when an Apple iPhone is switched off, its chips can continue running so it's possible for the owner to locate the phone when its lost or stolen.
Starting iOS 15, Apple has updated its Find My app to make this possible.
The feature keeps Bluetooth, Near Field Communication (NFC) and Ultra-wideband (UWB) technologies on to provide users' information to Apple, even when the device is off.
This is possible because the feature has access to the iPhone’s Secure Element (SE), which stores sensitive information.
The thing is, the feature does not have a mechanism for digitally signing or even encrypting the firmware they run.
According to a team of researchers from Germany’s Technical University of Darmstadt discovered, malicious actors can exploit this "to load malware onto a Bluetooth chip that is executed while the iPhone is off," for example.
In a research paper titled “Evil Never Sleeps: When Wireless Malware Stays On After Turning Off iPhone", the researchers said that:
"For instance, upon user-initiated shutdown, the iPhone remains locatable via the Find My network. If the battery runs low, the iPhone shuts down automatically and enters a power reserve mode. Yet, users can still access credit cards, student passes, and other items in their Wallet. We analyze how Apple implements these standalone wireless features, working while iOS is not running, and determine their security boundaries."
"On recent iPhones, Bluetooth, Near Field Communication (NFC), and Ultra-wideband (UWB) keep running after power off, and all three wireless chips have direct access to the secure element."
"As a practical example what this means to security, we demonstrate the possibility to load malware onto a Bluetooth chip that is executed while the iPhone is off."
This is possible because the three chips can run in a so-called Low-Power Mode (LPM). When in LPM, an iPhone will not react to tapping the screen or shaking. Those sensors are off when an iPhone is turned off.
But since Bluetooth, NFC and UWB that are kept on have minimal security, bad actors can create a malware to break into the iPhone to steal data.
"[Low-Power Mode] is a relevant attack surface that has to be considered by high-value targets such as journalists, or that can be weaponized to build wireless malware operating on shutdown iPhones," the paper reads.

Academics at Germany’s Technical University of Darmstadt figured out how to exploit this weakness by allowing an attacker to track the phone’s location or run new features when the device is turned off.
It’s important to note, though, that the research is at this point is mostly theoretical.
The researchers at Germany’s Technical University of Darmstadt have no evidence that this kind of attack has been used in the wild.
And also, fortunately, the researchers point out in the paper that hackers would need to first hack and jailbreak the iPhone to be able to access the Bluetooth chip and exploit it.
Making it even more difficult, hackers would also need to communicate to the target iPhone's firmware via the operating system, modify the firmware image, or gain code execution on an LPM-enabled chip over-the-air by exploiting flaws such as BrakTooth.
Still, even for hackers who have already taken control of the phone, hacking the Bluetooth chip would give them access to another place to collect data, an especially useful one because it’s available even when the phone is powered off.
LPM is needed to increase the user’s security, safety, and convenience.
For example, powering the aforementioned Find My app.
The researchers also explained that the Bluetooth chip that is kept on under LPM, as well as other wireless chips, like the NFC, is used to power Apple Pay, for example. The UWB and Bluetooth can together work to turn an iPhone into a car key.
While it does work like it should, with the researchers praising Apple.
With the feature, users should be able to locate their phone if its lost or stolen, and can still pay for things, even when their phone runs out of battery.
The thing is, the feature also creates a new threat model.
"The current LPM implementation on Apple iPhones is opaque and adds new threats," the researchers said. "Since LPM support is based on the iPhone’s hardware, it cannot be removed with system updates. Thus, it has a long-lasting effect on the overall iOS security model. To the best of our knowledge, we are the first who looked into undocumented LPM features introduced in iOS 15 and uncover various issues."
"Design of LPM features seems to be mostly driven by functionality, without considering threats outside of the intended applications. Find My after power off turns shutdown iPhones into tracking devices by design, and the implementation within the Bluetooth firmware is not secured against manipulation."