
People store many things on their mobile phones. This fact makes smartphones the target by many cyber criminals who want to get a peek, steal or misuse others' personal data.
According to security researchers at AdaptiveMobile Security, a SMS-based attack method using an old technology has being abused in the real world by a surveillance vendor to track and monitor individuals.
Considered an "escalation in the skillset and abilities of attackers," the researchers' report said that the attack is "a huge jump in complexity and sophistication" compared to attacks previously seen over mobile networks.:
"We believe this vulnerability has been exploited for at least the last 2 years by a highly sophisticated threat actor in multiple countries, primarily for the purposes of surveillance."
The method is simply called 'Simjacker'.
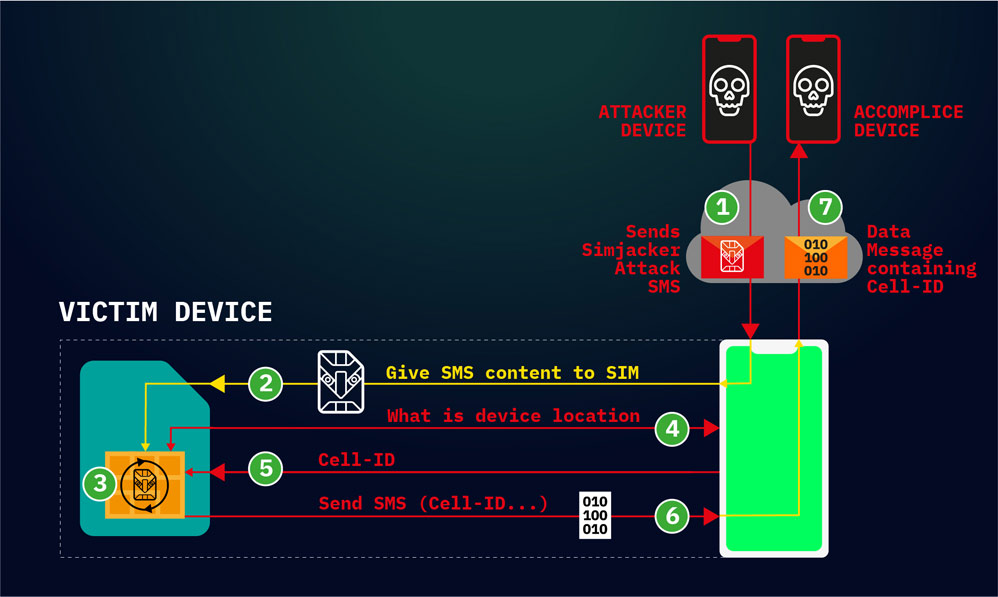
What it does, is exploiting vulnerability present on mobile phones. The attack involves sending an SMS containing specific type of spyware-like code, which instructs the SIM card within the recipient's phone to receive and perform commands from the attacker.
All the attackers need to perform this Simjacking attack, is to own a smartphone, and a GSM modem, or any A2P (application-to-person) service to send an SMS message to a victim's phone number.
According to the research, thousands of devices have their location information delivered to the attacker, all without the phone owners' knowledge.
But since the exploit opens the target's phone for further attacks, the damage can be more than just that.
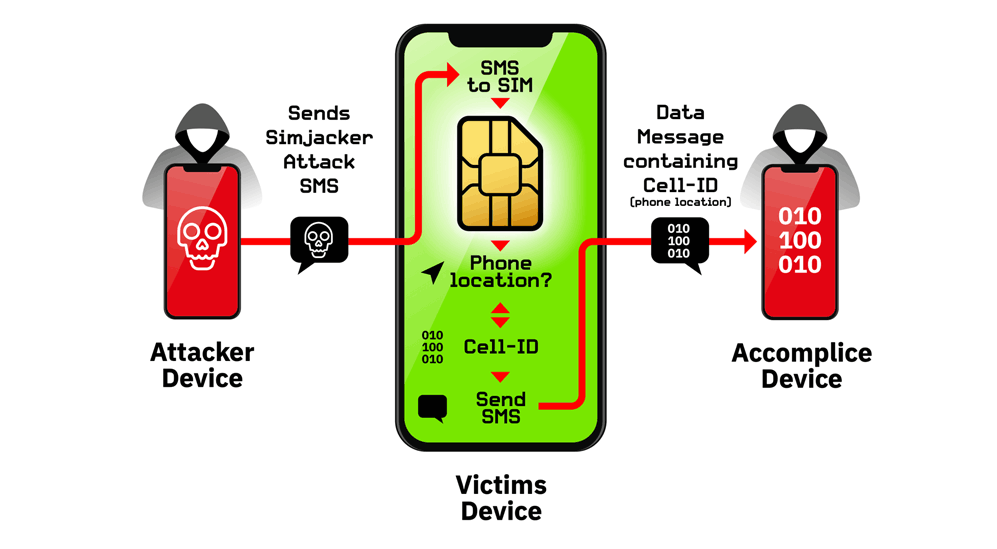
For example, the malicious SMS messages can contain hidden SIM Toolkit (STK), which controls the target device's S@T Browser, an app that resides on the SIM card, rather than the phone.
The STK instruction can command the victim's S@T Browser to trigger actions on the device, such as playing sounds, or showing popups, to even more intrusive attacks, like making calls, power off SIM cards, run AT modem commands, open browsers (with phishing links or on sites with exploit code), and more.
In other words, attackers are leveraging an old technology, the protocols used by many mobile network operators to send promotional offers and billing information, long before the era of smartphones, as explained by the researchers:
Abusing this vulnerability, Simjackers can also instruct victim's phone to hand over its IMEI code.
What makes this attack particularly dangerous and unique is that, it doesn't leave a trace. Simjacking attacks are completely silent. Despite the attackers can communicate with the victim's phone through SMS, the victim won't see any incoming or outgoing SMS messages.
This allows threat actors to continuously bombard victims with SMS messages and keep track of their location as they move through the day, week, or month.
And because this exploit resides inside the SIM card itself and not the phone, the attack can continue regardless of the user's device type or mobile OS.
"We have observed devices from nearly every manufacturer being successfully targeted to retrieve location: Apple, ZTE, Motorola, Samsung, Google, Huawei, and even IoT devices with SIM cards," the researchers said.
AdaptiveMobile said that it has seen the S@T Browser technology active on the network of mobile operators in at least 30 countries around the globe. In these countries, the researchers said, potential targets accumulate to more than a billion people.
Fortunately for most users, this kind of attack is quite difficult to accomplish, and quite easy to counter.
First of all, the attack doesn't rely on regular SMS messages, but a more complex binary code, which may not be familiar with most hackers. Second, STK instructions aren't new, as they have been used by many operators. It's just that threats actor have found a way to weaponize the STK instructions.
What this means, network operators should be able to configure their network to block such data from traversing and reaching their clients' devices.
But nonetheless, attackers who know this exploit have been using the method on a daily basis, in large numbers.
In most cases, victims are tracked a few times a day, for a long period of time, to even years.
The researchers also found a few instances of victims being targeted hundreds of times per day on over a 7-day period, suggesting the the victims are high-value targets.
Reading the attack patterns, the researchers said that Simjacking is designed to track a large number of people for a variety of reasons, with targets and priorities shifting over time. But it doesn't indicate mass surveillance operations.