
If compared to its Android counterpart, iOS is considered more polished and more secure.
But just like anything else out there, bugs are essentially weaknesses in systems waiting to be exploited. Bugs are everywhere, and the more advanced a software is, the more prone it is for having bugs. And iOS is no different.
While some bugs are worse than others, the most dangerous would be zero-day bugs.
Between 2019 and December 2022, an extremely dangerous bug was found on iMessage.
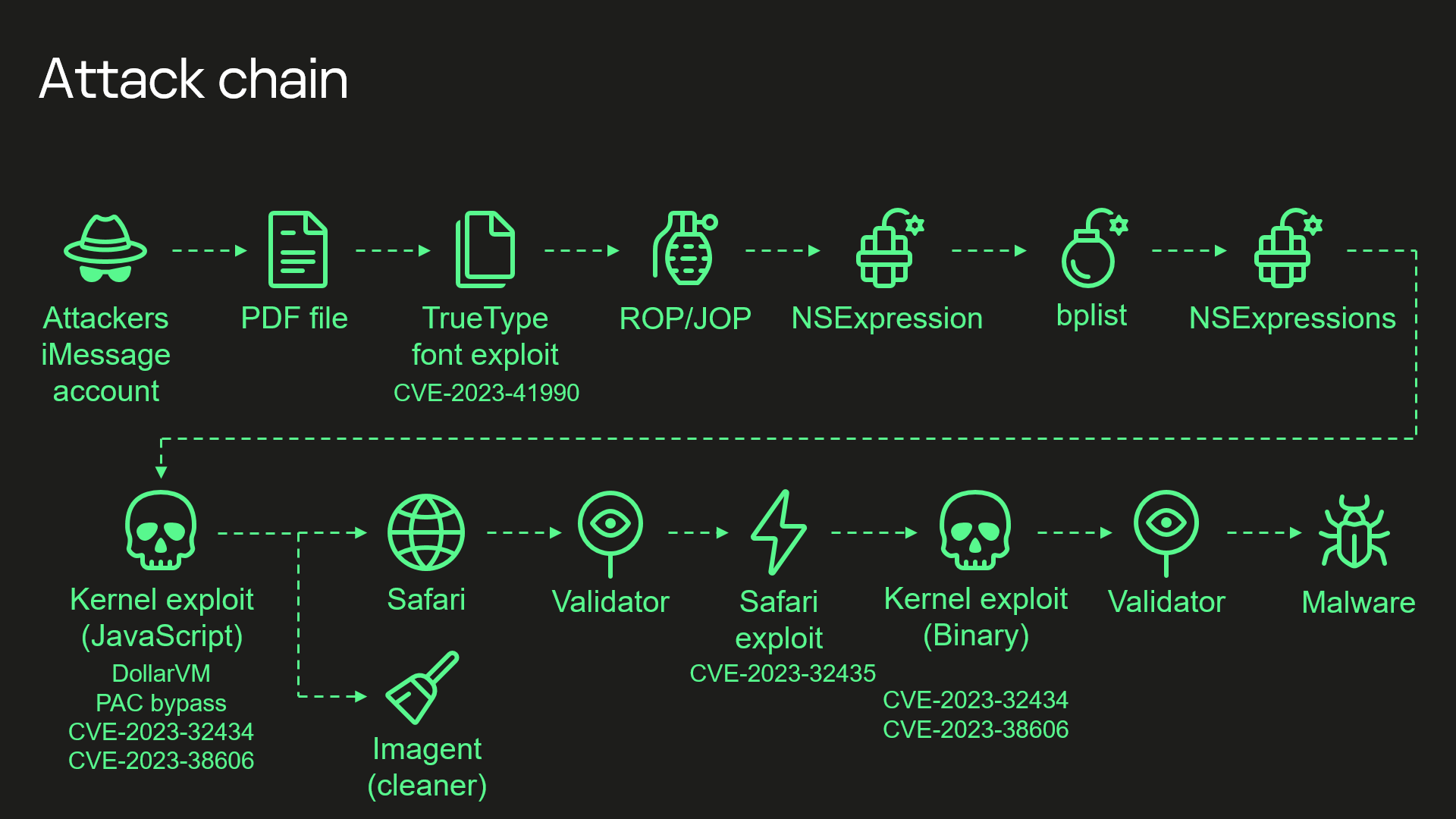
Dubbed the “Operation Triangulation” by security researchers at Kasperksy who discovered it, the zero-day is considered the "most sophisticated attack chain" the researchers have "ever seen."
And this is for a number of reasons.
We presented our #OperationTriangulation at #37С3:
Here is a detailed analysis of the most sophisticated attack our experts have ever seen, presented at 37C3 conference.#ATP #IOS #Applehttps://t.co/Hq8Wme0Usr— Kaspersky (@kaspersky) December 29, 2023
If Israeli's NSO Group's Pegasus is considered "one of the most technically sophisticated exploits," this Operation Triangulation is similarly scary.
This is because the zero-day bug is a chain attack that can exploit iMessage with no click whatsoever. What this means, iOS users have to do nothing for the exploit to run.
According to the researchers at Kaspersky, the most intriguing detail is that Operation Triangulation relies on exploits hidden so deeply that virtually no one outside of Apple could have known about them.
More concerning is that the spyware is "zero-click." It activates when a phone receives a text message with a malicious attachment, without requiring the user to open or read the message.
It bypasses Apple's hardware protections and can access a device's entire physical memory.
Furthermore, the malware remains active even after the message is deleted.
The malware, affecting iOS versions 15.7 and earlier, is able to leak microphone recordings, location data, and more.
Kaspersky found later that iOS versions older than 8.0, released in 2014, are also affected.
About how it works, it activates when a phone receives a text message with a malicious attachment, without requiring the user to open or read the message. It bypasses Apple's hardware protections and can access a device's entire physical memory. Furthermore, the malware remains active even after the message is deleted.
"The attackers leveraged this hardware feature to bypass hardware-based security protections and manipulate the contents of protected memory regions," said the researchers.
Operation Triangulation that make it of four zero-day vulnerabilities affecting iPhones, iPads, Macs, Apple Watches, and Apple TVs, was fixed after Apple released iOS 16.6, iPadOS 16.6, tvOS 16.6, watchOS 9.5.3, and macOS Ventura 13.5.
Recent #iPhone models have additional hardware-based security protection for kernel memory. Our experts disclose how attackers leverage an alternative hardware facet of #Apple SoCs to bypass this security layer.
Full story #OperationTriangulation #iOShttps://t.co/9zLChoHqwv— Kaspersky (@kaspersky) December 29, 2023
The researchers said that they’ve almost reverse-engineered "every aspect of this attack chain," meaning that no similar zero-days should be found in the future.
But still, Larin, Bezvershenko, and Kucherin said that systems "that rely on 'security through obscurity' can never be truly secure."
"This is no ordinary vulnerability," said Boris Larin, Principal Security Researcher at Kaspersky.
"Due to the closed nature of the iOS ecosystem, the discovery process was both challenging and time-consuming, requiring a comprehensive understanding of both hardware and software architectures. What this discovery teaches us once again is that even advanced hardware-based protections can be rendered ineffective in the face of a sophisticated attacker, particularly when there are hardware features allowing to bypass these protections."