People cannot see everything in front of them. That is also true with the "invisible malware".
With the advancements in technology powering anti-malware and Endpoint Detection and Response (EDR), computer protections are becoming generally better. This makes sophisticated attacks able to be predicted and prevented.
But this is where malware developers are moving lower on the stack.
Invisible malware is a breed of malware, when commencing its attacks, renders victims and antivirus/anti-malware software useless. This is because in many cases, invisible malware is fileless, meaning that it lives only inside a system's memory.
Because no files exist, the usual security protections including firewall cannot catch it.
Invisible malware can also exist inside a system's Basic Input/Output System (BIOS), with virtual rootkits to create a virtual machine (VM) where the malware can live without being detected, making it impossible to catch.
Or in other cases, appear as a firmware update where it replaces users' existing firmware with a version that's infected and nearly impossible to find or remove.

Invisible malware here, can also be described as a 'non-malware' or 'zero-footprint malware'. It is developed and designed specifically to evade detection by legacy software.
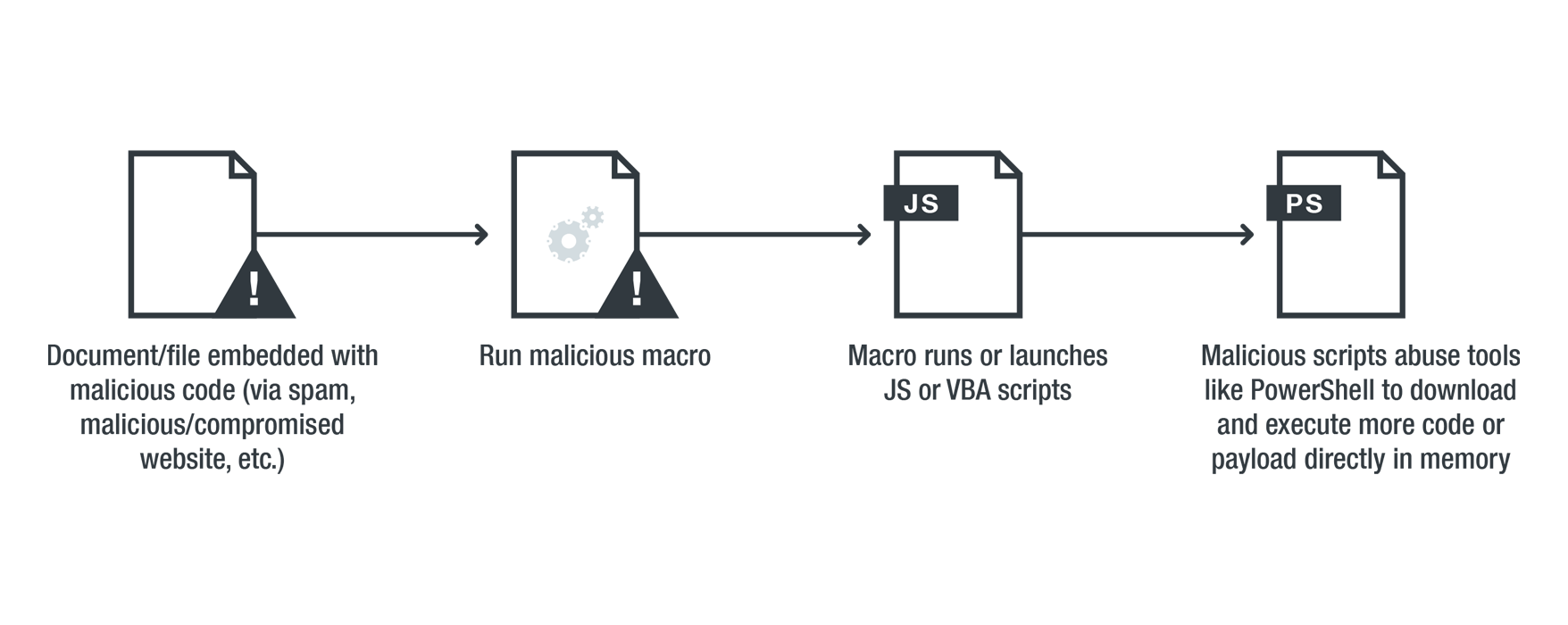
Unlike traditional malware attack, which requires something to be written on the hard disk, invisible malware attack uses no code. Instead, it uses legitimate system assets and trusted processes such as memory, PowerShell, etc., to infect victims' machine.
As these are highly trusted processes, most antivirus solutions don't even scan them.
Users can get their systems infected by clicking on a cleverly disguised spam email, which then downloads the malware, for example.
Using Flash, hackers can use it to access PowerShell and send instructions, operating just from computer’s memory, through the command line to download malicious PowerShell script, which collects sensitive data and sends it back to the attacker.
Symptoms of an invisible malware attack can include some warning signs from the computer as it tries to connect to botnet servers, or some other weird networks.
Knowing that this filesless "invisible malware" can do destructing damage with nothing can be done, what hope can users have?
Going into a bit more detail, invisible malware can:
- Unload its payload without touching the hard drive (not copying any files into the physical drive). This makes it pass antivirus scanning.
- Its payload is loaded in the context of the legitimate process that executes the scripts.
- Leave no traces, making little chance for forensic analysis to find evidence.
Fortunately, for hackers to install a virtual rootkit onto a server is difficult - to the extent that attackers who are trying to this happen generally work as state-sponsored attackers. In addition, while invisible malware is literally "invisible", at least some of its activities can be detected and a few can be stopped.
For example, fileless malware which operates only from the inside of an infected system's memory, can be detected by forcibly powering off the computer on which the malware is running.
But such malware may be accompanied by what's called 'Blue Pill malware'.
This is a form of virtual rootkit that can load itself into a VM to then load the entire operating system into a VM. This makes the malware capable of initiating a fake shutdown and restart, while allowing the original malware infection to keep running.
This is why shutting down a computer using the designated feature on an infected operating system may not kill this malware. Instead of powering off this way, users is required to manually pull the power plug instead.
Other types of invisible malware attacks can also be detected, but only possible when the attack is being commencing. To do this, an EDR package may work autonomously and combine information with other endpoints to build context, for example.
Other solution includes an antivirus solution in capable of inspecting script behavior by exposing script contents in a form that is both unencrypted and unobfuscated.
What this means, the antivirus should work beyond normal scanning, to include things like behavior monitoring, memory scanning, and boot sector protection, to catch a wide spectrum of threats, including new and unknown fileless threats or other sophisticated malware.
Understanding the context and the flow, the anti-malware can create stories that can be used to detect the operations of the malware.
But still, this approach can't catch everything, especially when it happens outside of the operating system. A USB thumb drive that rewrites the BIOS before the computer boots is one example.
This is where the next level of preparation comes in.
For example, creating computer chips and processors that are hardened in security, specially designed to prevent malware infections by isolating critical resources and protecting those resources.
Another solution includes a security procedure which can lock down an infected BIOS. Here, the security system should make the BIOS able to communicate with the operating system, so when the malware is detected, the operating system can respond and protect against the attack once operating system is turned on.
But for existing systems without the above protections, there's nothing much users can do.
The only way most users can do, is to merely avoid the problem to happen in the first place, by moving all their critical data and processes to the cloud.
Without considering the occasional data breach that may happen on third-party cloud storage companies, generally, storing files on the cloud is the safest bet for users.
To safeguards systems against this zero-footprint invisible malware attacks, users can:
- Disable processes when not in use.
- Disable PowerShell, macros, Windows Management Instrumentation when not in use.
- Always keeping the software and patches current and up-to-date.
- Constantly monitor security, network, and activity logs.
- Grant privileges and access to only credible and trusted users.
- Monitor system’s behavior patterns regularly.