Many new devices are introduced each day, and many of them are fitted with sensors to embrace the Internet of Things. Because the number of the devices introduced is increasing at an staggering rate, more data are being exchanged throughout the internet and its networks. When privacy comes to concern, some may wonder: where do all the data go?
Data and wireless technologies have been beaming data around the world for quite a while. The technologies that we see common these days were once dominated by people in the governments and large corporations. The advances of computers and its processing technology have made them smaller but yet a lot more powerful.
Computers that were once a common thing on people's home are slowly being replaced by smaller but more sophisticated machines. While the more of them are produced and the cost lowered, the once was expensive pieces of technologies can now be afforded by even the most common people.
When the internet came to a rise, the advanced technologies are racing to put more of themselves online; they're pursuing to further lower the operation costs to make more data to be transmitted.
The world as we see it is flowing with invisible data. Whether we realize it or not, the atmosphere we live in is becoming more crowded. Something should be able to control it, or else chaos will happen.
The Internet of Things (IoT) is one of the most talked about technology that will take even more devices to the internet. It's basically new and complicated, and many people are racing to make it happen.
"Dumb" Things To Become "Smart", Humans Are Fooled
Making ordinary things "smart" can give a huge benefit to how people will interact with their everyday objects. In the race to automation, there is nothing better than having the total control of everything you own. While the possibilities that we hear are mostly the good things, IoT in fact wasn't built with security in mind.
While privacy is something, IoT is pretty far from it.
Before IoT was realized and people were still using their desktop computers to go online, security breaches were already common. People have data and information, and computers are one of the most place to keep them in one place. Virus and malware spread like wildfire, antivirus companies were racing to be the best.
As the internet widens, people are becoming eager to peek into others' belongings; wondering what they have and seek to some more to relieve their curiosity.
The more a thing is private, the expensive it will become. You sensitive information is expensive and you should be aware that many people want to get a hold of them.
Related: When Things Are Free On the Internet, They Aren't "Free". Your Data Is Expensive
There are already places on the web where users can sneak into people's bedroom through webcam feeds. The devices are already a common thing, and it's practically everywhere a computer/laptop is. From the streaming protocol which allows them to share video, many have no authentication password in place, allowing the whole world to see (if you know where to look).
Digging through those images and feeds, people's lives from the kitchen to everything in between classrooms and bedrooms can be seen.
When mobile devices came to everyone's pockets, everyone is literally a walking source of information. When people share the information they don't need to expose through the internet is one thing. The next is those people having their information taken from them without their knowledge.
The governments and their officials were known to tap into people's communication. One of which that came to the surface was when former contractor Edward Snowden leaked several documents he got from the NSA, revealing some secret projects the government do to expose people's lives to their own benefit.
When the whole world would eventually becomes connected, and "dumb" devices become "smarter", they also become part of the problem. All of them becomes one in a connected digital sphere of countless network of networks. Everyone of them are vulnerable.
IoT can have a bright future. But its growth will be slowed or even stalled if the industry fails to put privacy and security as priorities.
There is not enough coordination to response to threats support the beings threatened. Before the IoT starts to be common, people needs to create standard bodies to develop guidelines for the use. People need integrators and regulators. People need the government to govern a law above it.
The approach is one thing. The next is engagement, consultation and collaboration of everyone involved: from companies' stakeholders, the chip maker industry, intellectual property providers to end-users.
People will need to fill any occurring gaps and everyone has a role to play.
Building A Safer IoT
When peeking into someone's bedroom is possible through webcams, imagine them sending the footage to websites on the web. Devices that are connected to the internet can pose many vulnerable privacy breach. Now imagine when more than just the moments in your house are exposed; imagine your house itself is exposed.
People spying through your webcam have occurred, and that is just one thing. There are many other things you can on the internet these days if you know where to look. A Russian website for example, have already done the job: before its shut down, it provided links to 73,011 locations with unsecured security cameras in 256 countries. In an unrelated incident, a hacker in Cincinnati compromised a baby monitor and used it to scream at a sleeping child.
IoT can be friend to many people. It should ease almost everything we do in our daily lives. But as privacy is a concern, it could be touted as our worst enemy.
Researchers have discovered that in some cases, people can hack IoT to intercept printed documents and divert it to somewhere else. They can plant a malware inside your smart TV and even control the lights in our house.
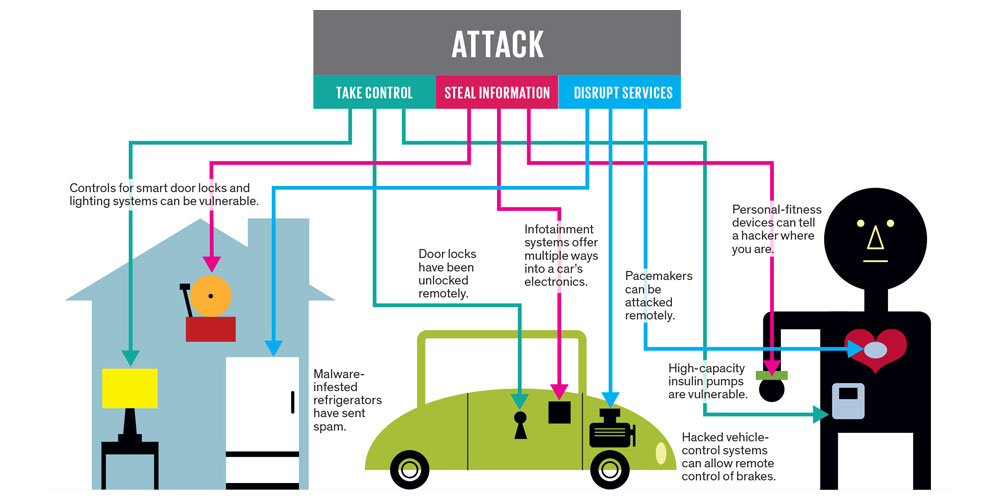
With IoT, you can make your house smarter. You can turn on/off your appliances and many other things. But what if it wan't you that did that? Hackers can get into your house by cutting the electricity remotely to simplify burglar attempt. If you have a security camera, that can be hacked to show other feeds. If you have smart locks for your home, hackers can unlock them remotely so your doors will open to them by the time they get there.
Modern cars can be equipped with sensors to remotely start and turn on the engine when signaled by your mobile device. Since it's integrated with the GPS, it can tell the weather and traffic data. Cars can also be equipped with sensors to record and report diagnostics. While this can be a good thing for mechanics, hackers that can get themselves inside the system through IoT can remotely flash the car's lights, enabling them to identify it on your street, unlock the door and get in as your house's doors were already unlocked, start the engine, and drive it away.
As people are depending on gadgets and technologies more than they use to, like for example using gadgets as wearables, hackers can even control your body.
With the IoT, there is practically no place to hide. Hackers who do the attack, typically do one of the three things: take control, steal information, or disrupt the service.
In an episode of the TV show, a murderer kills someone remotely by accelerating a heart pacemaker. While this is a trick that is not yet reported in real life, it has been demonstrated in a lab. Researchers have also demonstrated that insulin pumps, used to help control diabetes, can be remotely instructed to pump all their insulin out at once, killing the user.
To most IoT devices, even if they're secured, there is no way to automatically update their software vulnerabilities as they're discovered. IoT devices are different that traditional computers and mobile devices we have.
Some precautions that can be used to prevent/limit the access of any unauthorized access are using the ordinary available protections. Some of which are:
- Firewall to act as a gatekeeper to prevent unauthorized traffic to get through.
- Rules-based filtering to set policies that act to prevent unauthorized remote updates to embedded firmware.
- Data encryption to prevent others from reading data easily.
- Sophisticated authentication methods that can use biometric data to allow access only to those that should.
- Security standards coming out from specific industry and applications.
- Device-management agent that would allow the product to communicate with a security management system.
- Etc..
Securing Privacy Is Everyone's Self-Responsibility

When there is a lot of data to be tapped, users should know some technical details on how things work. They need to know the precautions to keep themselves safe as well as keeping their sensitive information locked where they belong.
Security is really context-dependent. There are a lot of privacy issues over mobile devices. Many apps and companies have been questioned regarding how they use users' data and why do they need them.
The challenges here is to explore how IoT devices can be updated with ease, and how people can keep sensitive things to themselves. Focusing on IoT security should be done to avoid any past mistakes we've had.
And as IoT gets to more places, we are in the start of what will likely become a long journey. Industries in the world are looking to move forward, and we're expecting it to happen. Will it changes the trend and how people communicate? The answer lies on how dependent we are on gadgets tomorrow than we do today.
Further reading: Embracing The Internet Of Things: New Potentials Same Problems
