
There are over 300 million fraudulent sign-in attempts to Microsoft cloud services every single day, and the number is increasing.
While many of those attack attempts were thwarted without having to use advanced technology, speaking at the RSA security conference, Microsoft engineers said that 99.9% of the compromised accounts they track every month didn't use multi-factor authentication (MFA).
In most cases, account hacks happen after rather simplistic attacks.
The primary sources of most Microsoft accounts hack were using 'password spraying', a method in which attackers randomly choose a common and easy-to-guess password, and goes through a list of common usernames.
"All it takes is one compromised credential or one legacy application to cause a data breach. This underscores how critical it is to ensure password security and strong authentication. Read on to learn about common vulnerabilities and the single action you can take to protect your accounts from attacks," Microsoft said on its blog post.
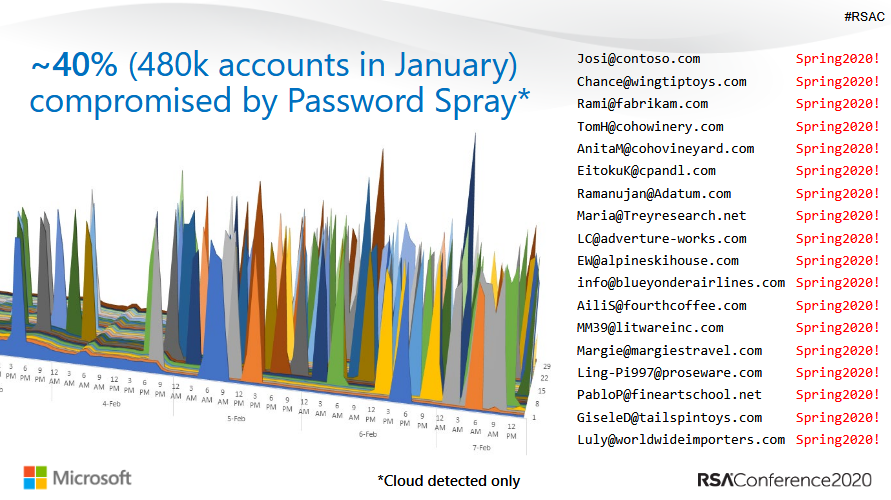
Password spraying method is known as a more advanced method than the more traditional brute-force attack attempt to gain unauthorized access to a single account.
While Microsoft has protection against this kind of attack, password spraying involves the hackers use 'low-and-slow' approach, in which they guess one common username-password combination on many accounts before moving on to attempt a second combination, and so on.
By avoiding rapid sign in attempts or frequent account lockouts, password spraying technique allows the hackers to remain undetected by the system.
The second most common method of hacks, was 'password replays'.
This involves hackers in taking credentials of previously known leak at another company, and then trying the same credentials on a Microsoft account, hoping that the user reused usernames and passwords.
"We know that 60% of users reuse passwords. It's super common," said Lee Walker, Identity and Security Architect at Microsoft. "Don't be confused. People reuse their enterprise accounts in non-enterprise environments."
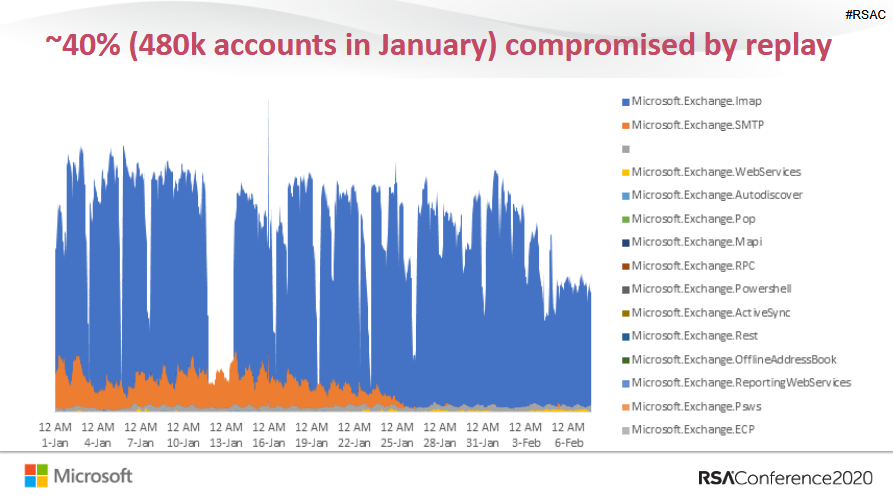
According to Walker, a vast majority of password spraying and password replay attacks on Microsoft's infrastructure are carried out and target older legacy authentication protocols, such as SMTP, IMAP, POP, and others.
To be more exact, 99% of all password spraying attacks and 97% of password replay attacks were actually carried out via legacy authentication protocols.
Users that leave these legacy authentication protocols enabled for their cloud systems and networks are more exposed to attacks. Microsoft suggests that they should disable them as soon as possible.
The reason, according to Microsoft, is that these legacy authentication protocols don't support MFA solutions (hardware key, SMS, etc.), making them alluring targets for hackers.
The recommendation applies not only for Microsoft accounts but also for any other accounts, on any other website or online service.
If a service provider supports multi-factor authentication, Microsoft recommends people to use it, regardless if it's something as simple as SMS-based one-time passwords, or as advanced as biometrics solutions.
Old advice like "never use a password that has ever been seen in a breach" or "use really long passwords" doesn't really help, said Alex Weinert, Group Program Manager for Identity Security and Protection at Microsoft.
Strong password does help, as it complicates password spraying method. But hackers apparently have different methods at their disposal to get their hands on users' credentials. And in many of those cases, the password doesn't even matter anymore
For example, hackers can use phishing scam, keyloggers, local discovery, and even extortion like blackmail or insider threat.
Back in May 2019, Google said that users who added a recovery phone number to their accounts and indirectly enabled SMS-based MFA were improving their account security.
"Our research shows that simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks that occurred during our investigation," Google said at the time.
With both Google and Microsoft are recommending the same thing, it would be wise for users to at least follow their advice.