
Android is the most popular mobile operating system, and that makes it a great target for hackers and alike.
According to a report by Slovakia-based cybersecurity firm WeLiveSecurity by ESET, their researchers discovered an Android ransomware family "that attempts to spread to victims’ contacts and deploys some unusual tricks" by leveraging SMS messages to spread.
The ransomware is distributed via pornographic post first found on Reddit and XDA Developers forum, the researchers noted.
And when it has successfully infect a victim, it uses the victim's contact list to spread further via SMS messages, with a link containing the malicious malware.
According to the researchers, the ransomware is active since July 12th.
The malicious SMS advertises the link for an app that supposedly uses the potential victim’s photos. But what it really is, is a malicious app containing a ransomware.
To trick unsuspecting victims click on the link and downloading the app, the attackers hide their true motives by masking the domain name using URL shorteners, like bit.ly.
And also to be better received by victims, the SMS sent can be written in one of 42 languages, depending on the potential victim's device language setting. To personalize these messages, the malware can prepend the contact’s name to them.
When the link is clicked, victims open an online sex simulator game. But that is only at the front.
In the background, the malicious app initiates a contact with its Command-and-Control (C&C) server to access a hard-coded list of addresses, and to encrypt and decrypt files.
The ransomware's Filecoder scans the infected device to encrypt most file types - including text files and images - with the extension
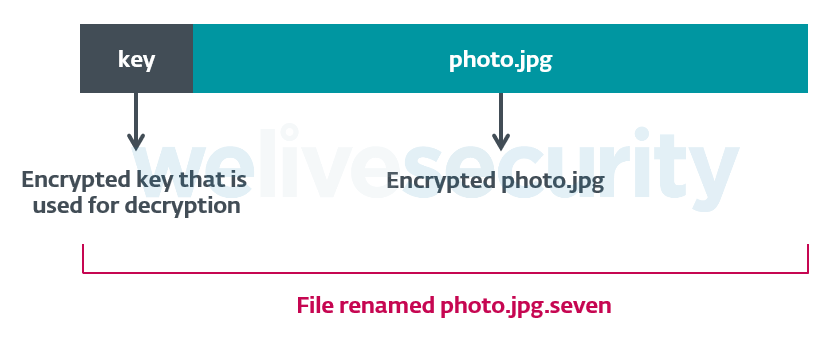
Encrypted and having different extension that their originals, the files can no longer be accessed.
The ransomware however, doesn’t lock victims out their device, and leaves files unencrypted if the file extension is .zip or .rar that are larger than 50MB, and .jpeg, .jpg and.png files that are less than 150 KB.
Android extensions such as .apk and .dex also appear to be excluded.
According to ESET, the ransomware that encrypts victims' data using RSA algorithm, appear to have its encryption file list copied from the notorious WannaCry ransomware that targeted Windows PCs.
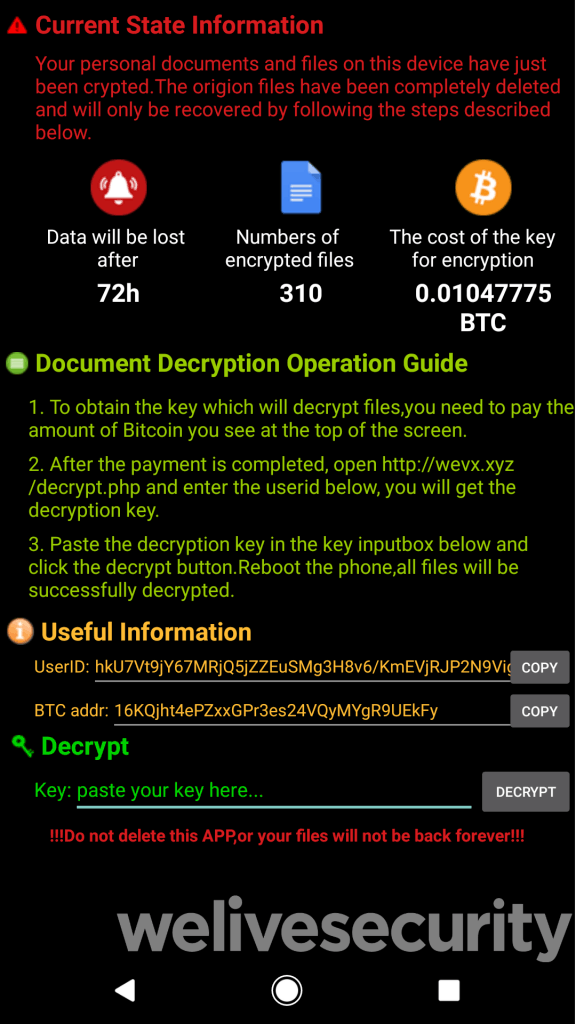
While the attacker demand ransom to decrypt the encrypted files, and warn that data will be lost after 72 hours, ESET found no evidence in the software code to support this claim..
The researchers found that most of the victims come from mainland China, the U.S., and Hong Kong.
While Android continues to face a continuous wave of security threats, such as from Agent Smith, the Monokle trojan, and others, it's advised to always download apps from Google Play or other reputable app stores.
Users should also keep their devices up to date, and always pay attention to permission types requested by apps.