No product is perfect. There should be some imperfections here and there waiting to be found.
Malware is something that affects all platforms. And here, according to a report by the security firm Check Point, the ‘Agent Smith’ malware has infected more than 25 million Android devices around the world with its malicious ad injection.
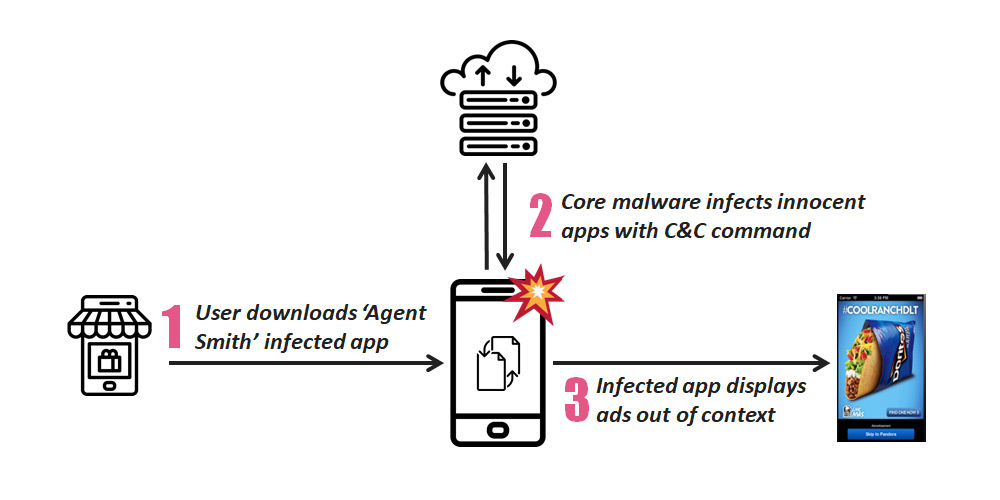
The malware is dubbed after the Matrix character because it hacks apps installed on users phone, and forcing them to show more ads.
Agent Smith then take the ads revenue by taking credit for ads that are already shown.
Check Point said that the malware originated in China, developed by an internet company that helps Chinese Android developers to localize and publish their apps to foreign markets.
Agent Smith usually hides in sex-related apps, games and photography apps.
Once the malicious app has been installed, the app requests numerous permissions, which unfortunately most people are reluctant to observe before granting. Using permissions given by victims, it hides itself by changing its name to a regular-looking and authentic apps like Google Updater, Google Themes or something else similar with the name "Google" on it.
The malware then goes to work by injecting its malicious codes into the bits of other popular apps. This code is then used to serve more ads and fraudulent ads for financial gains of its developers.
Agent Smith can do all these without users' knowledge or interaction.
And not only that. Because the malware injects its own codes to tamper other apps, the malware can also inject codes designed for even more dangerous purposes, such as stealing sensitive information, or spying on victims through their phones' camera or microphone.
According to Check Point detailing how the malware operates, the company explained how there were “endless possibilities” for hackers to harm a user’s digital security through Agent Smith.
Given the way it works, detecting Agent Smith is very difficult.
"The malware attacks user-installed applications silently, making it challenging for common Android users to combat such threats on their own," said Jonathan Shimonovich, Head of Mobile Threat Detection Research at Check Point Software Technologies.
"Users should only be downloading apps from trusted app stores to mitigate the risk of infection as third party app stores often lack the security measures required to block adware loaded apps."
Agent Smith spreads through third-party app stores like 9Apps. But according to Check Point, the malware's developers have also attempted to upload their apps to Google Play Store. 11 apps have managed to enter Play Store, all of which had codes related to previous versions of the malware.
However, the malware was inactive on those apps. Google has also removed those apps, saying them as "infected" or "at risk".
Agent Smith is capable of spreading by exploiting the vulnerability found on Android operating system.
This vulnerability was actually patched years ago within Android. However, it relied on developers updating their apps to add the protection. This made it unclear how many have not done their updates, further highlighting the importance of real-time updates and the weaknesses of the Android ecosystem.
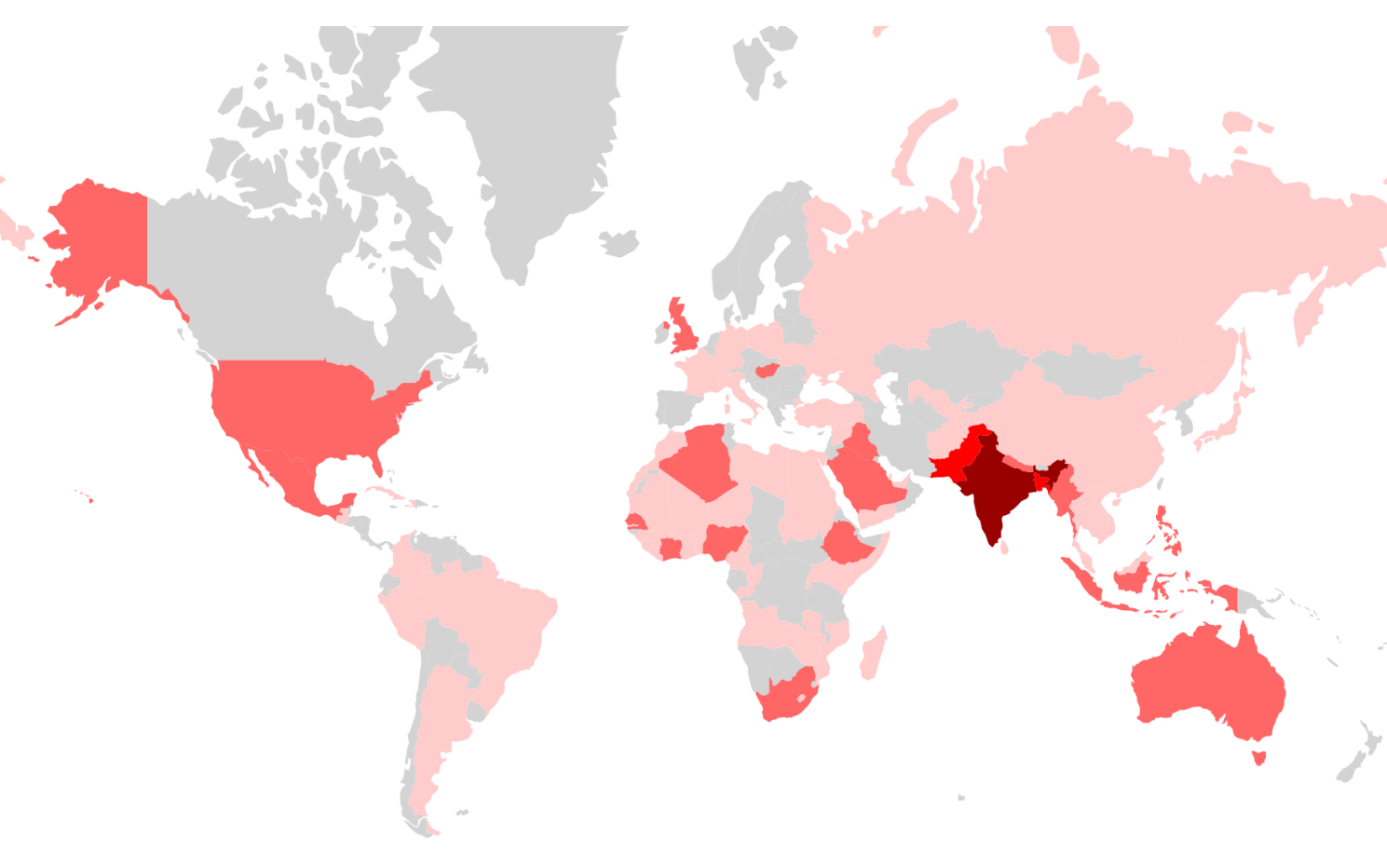
Agent Smith has claimed majority of its victims in India, Pakistan, and Bangladesh. About two-thirds of all infected devices are located in the south Asian country.
The malware has also managed to claim around 303,000 victims in the U.S. and a further 137,000 devices in the UK
Some of the apps that ended up being infected include WhatsApp, Opera, MX Video Player, Flipkart, and SwiftKey.
"Combining advanced threat prevention and threat intelligence while adopting a ‘hygiene first’ approach to safeguard digital assets is the best protection against invasive mobile malware attacks like ‘Agent Smith’," said Shimonovich.
"In addition, users should only be downloading apps from trusted app stores to mitigate the risk of infection as third party app stores often lack the security measures required to block adware loaded apps."