
Apple is often marketed as the safer option if compared to Android. But that isn't always true.
This is because Apple is just like any products out there, that can have vulnerabilities and issues here and there. And this time, Citizen Lab, which worked with Google’s Threat Analysis Group (TAG), reported that Apple devices had security vulnerabilities that were used to install the notorious 'Predator' malware on iOS devices..
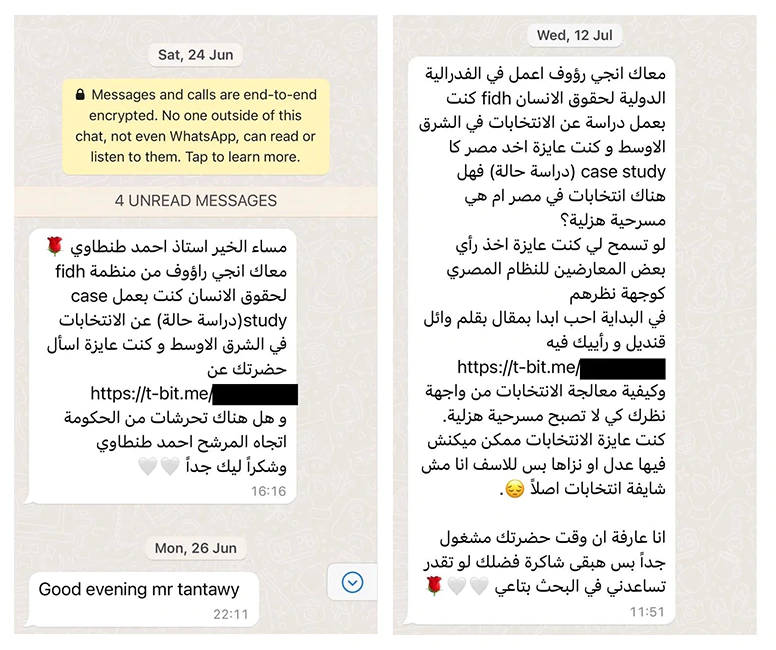
In particular, it's said that the bugs were exploited to hack into the Egyptian presidential candidate Ahmed Eltantawy.
"Our forensic analysis showed numerous attempts to target Eltantawy with Cytrox’s Predator spyware," Citizen Lab said in a report.
Following the findings and report from the spyware watchdog group, Apple rushed out an emergency patch to protect iPhone, iPads, and Macs from the threat.

The Predator malware in question, is created by Cytrox, an Israeli-Hungarian cyber arms dealer. Similar to the notorious NSO Group, Cytrox also sell its malware to be used by foreign governments to spy on journalists and high-profile individuals.
.
This malware was first discovered in 2022, hunting on Android phones by exploiting zero-day weaknesses.
At that time, the malware is said to have been used in at least three campaigns, including one that successfully infiltrated the phone of an exiled Egyptian politician.
“In August and September 2023, when Eltantawy visited certain websites without HTTPS from his phone, using his Vodafone Egypt mobile data connection, he was silently redirected to a website (c.betly[.]me) via network injection,” Citizen Lab said.
To burrow deep into Eltantawy’s iPhone, the relied on phishing messages. Citizen Lab noted that the attackers sent several SMS texts from September 2021.
That particular domain was created to only target marked targets.
Using a packet inspection device sitting on a cellular network in Egypt, sold by Egypt-based Sandvine, the attacker kept an eye out for only the connections that came from targets. Only when spotted, that the website would redirected the visitor to another site that proceeded to exploit the iOS vulnerabilities to hack the iPhone.

"In reality, clicking the links [in the messages] would likely have infected Eltantawy’s phone with Cytrox’s Predator spyware," Citizen Lab said.
Then in March and September 2023, they also sent a few more to his device while pretending to come from WhatsApp.
On iOS, the Predator malware leveraged three iOS vulnerabilities.
- CVE-2023-41991: PAC bypass.
- CVE-2023-41992: Local privilege escalation in the XNU Kernel.
- CVE-2023-41993: Initial remote code execution in Safari.
Exploiting the vulnerabilities allowed hackers that created a fake website to trigger rogue computer code on an iPhone, in order to elevate their hacking privileges on iOS. While Apple has strong walls to keep outsiders from getting in, the Predator can bypass Apple’s security system, and remain invisible to the operating system's list of installed apps.
Similar to Android, the result allowed the hacker to exploit zero-click attack to launch the Predator.
But the most disturbing of the finding, is how Eltantawy’s own cellular provider played a role in installing the spyware on his phone. It was Vodafone Egypt that forwarded his iPhone’s browser to malicious websites designed to load the Predator payload.
"Given that Egypt is a known customer of Cytrox’s Predator spyware, and the spyware was delivered via network injection from a device located physically inside Egypt, we attribute the network injection attack to the Egyptian government with high confidence," the group added.
According to Apple in a dedicated support page, the company patched the bugs in iOS versions 16.7 and iOS 17.0.1.
"Apple is aware of a report that this issue may have been actively exploited against versions of iOS before iOS 16.7." reads an advisory published by the company.
According to Google in a blog post, the company praised Apple's quick patching, adding that "we encourage all iOS users to install them as soon as possible."