The more complex a system is, the more holes that could be created. And this particular one is affecting billions of devices.
Named 'CallStranger' by discoverer Yunus Çadırcı, a cyber security senior manager at EY Turkey, it's a security vulnerability that affects devices running the Universal Plug and Play (UPnP).
The protocol was invented years ago as away for devices to plug-and-play onto a network. Using the protocol, users don't have to configure anything.
This is because any device that attempts to connect to a home router supported UPnP (often turned on by default), connectivity happened automagically.
But there is a problem.
The UPnP protocol can also allow more and more devices inside the network to connect to external entities on the internet without having to authenticate. This is troublesome.
As Çadırcı describes it, CallStranger (CVE-2020-12695) is simply a “Server Side Request Forgery (SSRF)-like vulnerability.”
Exploiting this vulnerability, hackers could use it to co-opt to vulnerable devices for DDoS attacks, bypass data loss prevention security to sneak data out of networks, and possibly carry out port scanning to probe for exposed UPnP devices.
In the modern days of technology where connecting devices have become so easy that people tend to not care about the complexity of protocols and to always secure them, the number of potentially affected devices could account to billions.
They include, and not limited to: home routers, modems, smart TVs, printers, cameras, and media gateways.
And because the UPnP protocol is often enabled by default, including on Internet of Things (IoT) devices, as well as well as major operating systems such as Windows 10, and even the Xbox games console, there is no saying how many more devices that could have been affected.
To educate people about this CallStranger vulnerability, a website (https://callstranger.com/) has been set up to list known and suspected vulnerable devices.
Çadırcı has also created a tool on GitHub, to help people check if their devices are vulnerable or not.
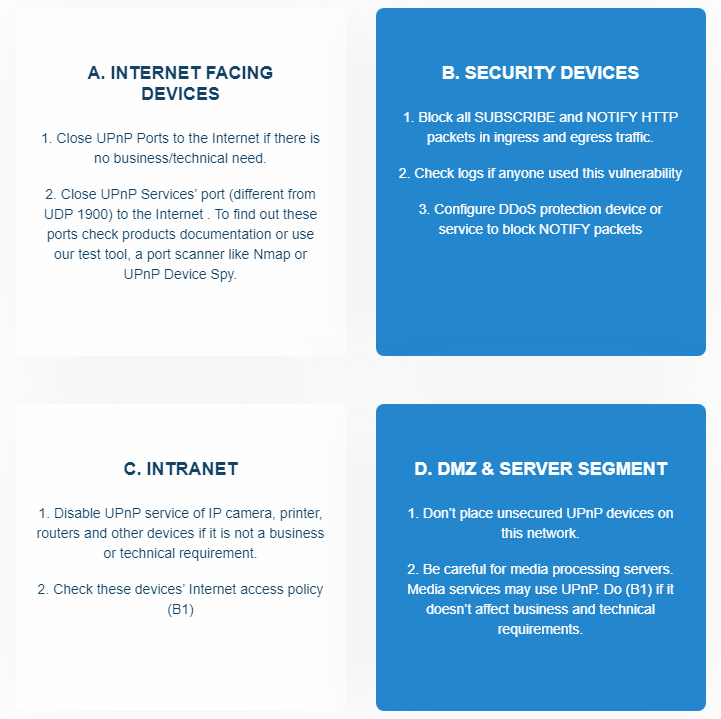
CallStranger is caused by Callback header value in UPnP SUBSCRIBE function. It can be controlled by an attacker and enables an SSRF-like vulnerability which affects millions of Internet facing and billions of LAN devices.
According to Çadırcı, this vulnerability can exploited by hackers for:
- Bypassing DLP and network security devices to exfiltrate data.
- Using millions of Internet-facing UPnP device as source of amplified reflected TCP DDoS.
- Scanning internal ports from Internet facing UPnP devices.
Back in December 2019, Çadırcı reported the flaw to the group that looks after UPnP, the Open Connectivity Foundation (OCF). Since then, he said that received hundreds of emails as part of the effort to coordinate a vendor response.
The OCF updated the UPnP specification on 17 April, which means that devices designed after that shouldn’t be vulnerable to the issue. Çadırcı however, said that home users are not expected to be targeted directly. But if their internet facing devices have UPnP endpoints, their devices may be used for DDoS source.
Because this is a protocol vulnerability, it may take a long time for vendors to provide patches.
It should be noted though, that the one UPnP stack that isn’t affected by CallStranger is MiniUPnP.
Nevertheless, billions of UPnP devices will still need to be patched. In the meantime, users should be able to mitigate the problem by turning off UPnP when not in use.