
Malicious software can be found almost anywhere, doing almost anything. Discovering new strains happens all the time.
And this time, a malware targeting multiple operating systems, including macOS, Windows, and Linux, has been found by researchers from Intezer, after being around for at least a year. Unlike most malware findings, this case in kind unusual, as it rare to discover a malware that can attack multiple platforms at once.
More than often, malware is created to attack a specific vulnerability in one platform only, rather than produced in a similar way to attack multiple platforms simultaneously.
Calling it the 'SysJoker' backdoor, the malware is essentially a trojan.
The researchers said that it was originally attacking Linux, before variants of the same backdoor were uncovered that went after Windows and macOS.
The malware can do this because its code is a universal binary covering Intel and arm64 builds, meaning that it could run on Apple Silicon as well as older Macs with Intel chips.
According to a blog post by the Intezer researchers, when the malware successfully installs itself into a host, ut will run and copies itself to the system's library as an update.
This is done so its can remain persistent in the infected system.
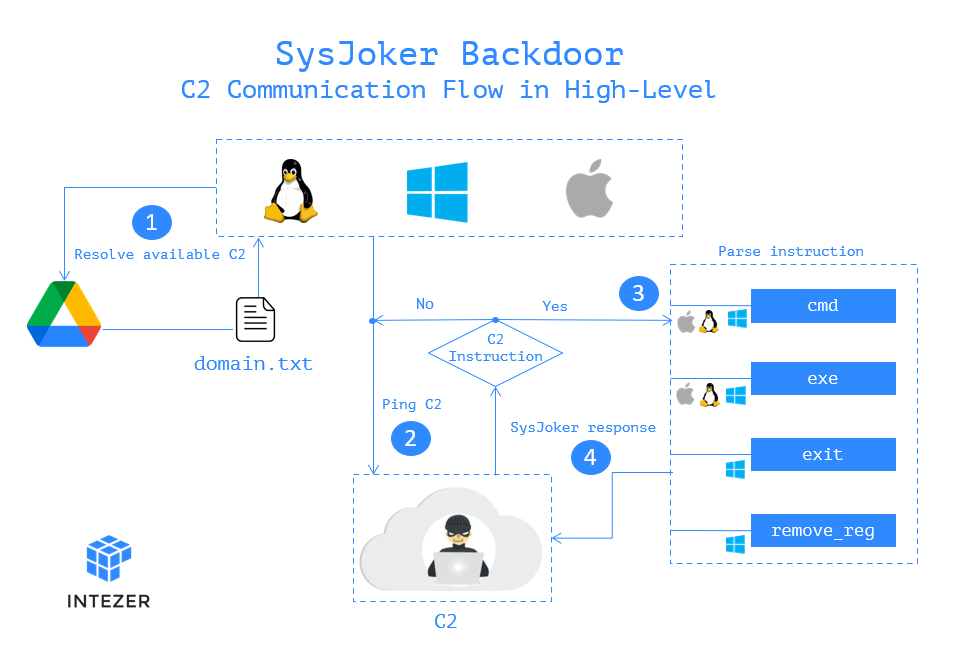
After that, the malware will attempts to download a file form a Google Drive account, to then run an executable, depending on the commands it is given from a designated control server. Other commands include unzipping a downloaded executable, and to change the permissions of the unzipped executable to allow it to run.
After several other actions are executed, the malware will begin collecting machine information such as the MAC address, serial numbers, and IP addresses.
In its research, Intezer didn't see any second-stage payload or command sent by the attacker.
What this means, the malware is likely to have a highly specific purpose, and therefore likely to be coming from an "advanced actor."
What makes this backdoor even more unique, is through the way it was written from scratch and made use of four separate command-and-control servers.
Due to its ability to infect different platforms, the researchers suggest that SysJoker's goal is "espionage," with possible ransomware attacks delivered at follow-up stages.
An indication that a system is infected with SysJoker, according to Intezer, is the presence of some files and directories created by the malware.
Intezer has detailed all the files and directories the malware creates when it is present in a system.
If these instances are found, it is advised to kill off all related processes and delete the files.
It's worth noting that the analysis of the malware on the Windows version is done by Intezer, whereas the version for Macs was done by researcher Patrick Wardle.
SysJoker that is written in C++, was first discovered in Ia leading educational institution's Linux web server.
The custom-written remote access trojan (RAT) went completely undetected for several months before its discovery.
It was only after the finding has been publicized, that antivirus engines started flagging this SysJoker malware.
