
With the more devices that can connect to the internet, hackers can turn unprotected ones into armies of bots to help them in attacking websites.
This kind of attack is called Distributed Denial of Service, or DDoS. This malicious attempt can disrupt the normal traffic of a targeted server, service or network, by overwhelming it and its infrastructure with a flood of internet traffic. This can cripple its system, by making it run out of resources.
Because DDoS attacks have become common, internet users are often treated with a "welcome screen" when they visit certain websites.
This security feature when present, is an unavoidable short-term annoyance. But what it does, is protecting the website from malicious operatives.
Unfortunately, hackers know this too, and because of that, they are turning this security feature into an opportunity to launch another kind of malicious campaign.
And that campaign is to plant malware through fake Cloudflare prompts.
Cloudflare, the U.S.-based content delivery network and DDoS mitigation company, is one of the most popular platform for internet security among web developers and webmasters.
Hackers that also know this, are using that fact to attack poorly protected WordPress websites.
According to a report from Sucuri, a website security and protection platform, hackers are doing this by adding a heavily obfuscated JavaScript payload that displays a fake Cloudflare protection DDoS screen.
Unsuspecting visitors of the website are requested to click on a button to bypass the DDoS protection screen.
However, clicking on the button would automatically download a security_install.iso file to the computer.
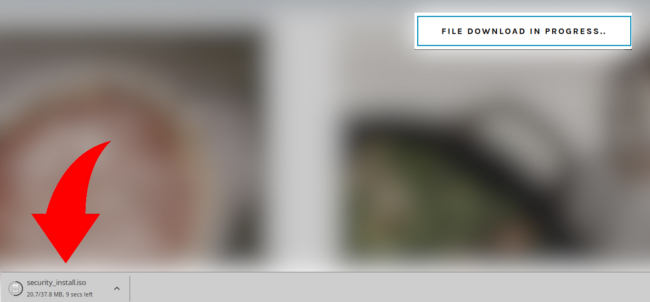
Victims are told that the file is an application called the 'DDOS GUARD', required to bypass that DDoS verification.
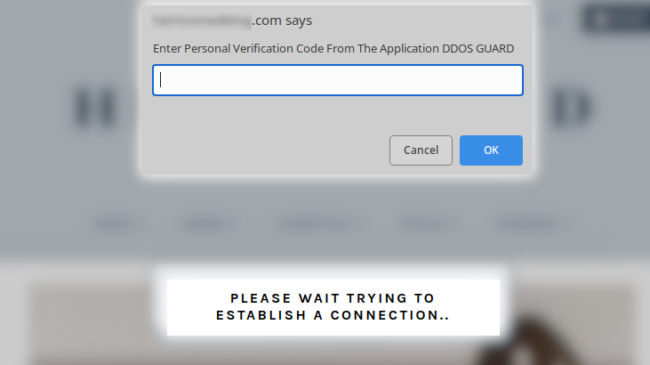
Victims are then told to open the file, and enter the code shown.
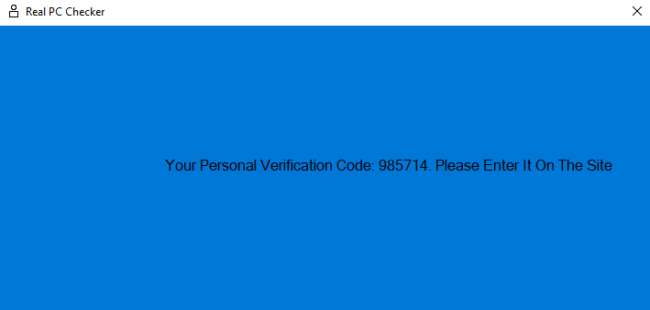
But what this file actually is, is a Windows shortcut that runs a PowerShell command, which causes a chain of scripts that ultimately install the NetSupport RAT, a remote access trojan used extensively in malicious campaigns.
Additionally, the scripts can also download the Raccoon Stealer password-stealing trojan and launch it on the compromised device.
According to researchers, the most common infection point in this campaign is the WordPress' theme files.
Administrators of compromised WordPress websites should check their sites' theme files, and check what JavaScript file runs from there.
Commonly, the infection comes from the jquery.min.js file that has been compromised.
Additionally, it is advised that administrators employ file integrity monitoring systems to catch those JavaScript injections as they happen and prevent their WordPress website from being infected with the RAT.
As for internet users, they can protect themselves from such threats by enabling strict script blocking settings on their browser.
This method should prevent the malicious script from running. Unfortunately, this will also break the functionality of almost all sites.
It's worth noting no legitimate website would require users to download anything before their website can be accessed by visitors.
What this means, no legitimate website would require users to download ISO files, even when the procedure is part of a DDoS protection.
