Since we know that username and password combination isn't secure, there have been attempts to improve the irreplaceable authentication process.
From captcha to two-step login, we want to be more secure than ever when trying to log in into our accounts.
The World Wide Web Consortium (W3C) and FIDO Alliance have announced that method called 'WebAuthn' or "Web Authentication", has been promoted to the Candidate Recommendation stage. This is the penultimate stage in the web standards process.
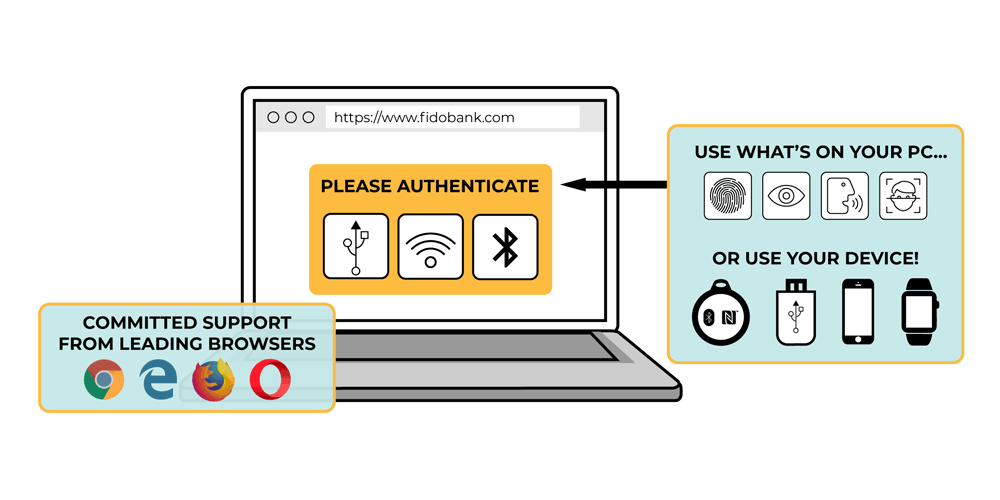
What WebAuthn does, is allowing web browsers to use hardware authentication devices plugged or built inside the system - USB, Bluetooth or NFC - and expose them to websites on the web. These hardware enable users to provide their identity to those websites, without having to input their usernames and passwords.
Also with With WebAuthn-enabled browsers and sites, users can sign in using both integrated biometric hardware (such as fingerprint and facial-recognition systems) and other external authentication systems
WebAuthn system is a credential management API, built on FIDO's previous specification in 2014, called the Universal Authentication Factor (UAF).
The specification for UAF fell short, and it seems there was never a real push to have the necessary functionality added to major browsers/ Developers that wanted to implement it were required to create a workaround due to the lack of native support. There are also little reference to make UAF work properly on Android and iOS devices.
But WebAuthn that has a similar approach, is different as it is fairly easy to implement in practice.
Microsoft, Google, and Mozilla have all committed to supporting WebAuthn. What this means, WebAuthn has strong backing from major browser vendors.
Here, the widespread of the adoption should allow the use of passwordless authentication to be more useful than ever, and also more practical.
The advantage of WebAuthn is that, no user credentials have to leave the browser, and no username and passwords combination is needed. Its API relies on strong cryptographic principles and asymmetric encryption.
What's more, it's also designed to be versatile. For example, it supports more than just a wide range of authentication factors, covering not just biometrics and hardware authenticators. It's designed to also include PINs and even more basic tests that merely verify that a user is present, without any indication who the user is.
This should provide a very strong protection against phishing or man-in-the-middle attacks.
When considering security, most issues like with the implementation of the WebAuthn specification by developers. If a developer doesn’t check for things like replay attacks or making sure that the authenticator hasn’t been compromised in some ways, then attacks are still possible. Most concerns regarding the authenticator and manufacturer can be mitigated if the developer is careful.
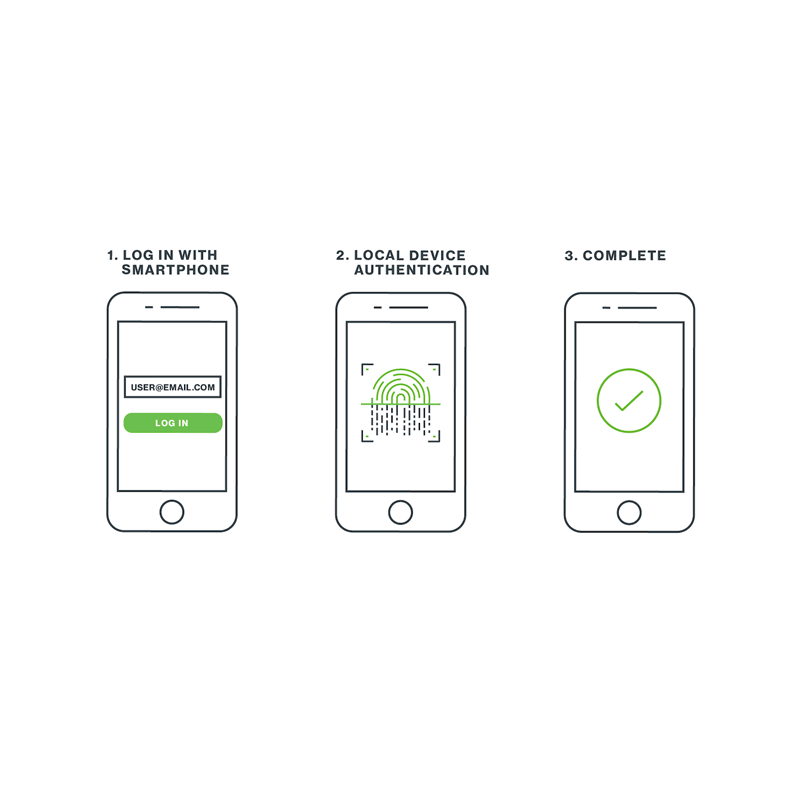
The big step up that WebAuthn introduces, is a biometric multi-factor authentication based on "something a user is."
In most cases if not all, a user has things that are unique to them. Like their voice, fingerprint or retina. Since many smartphones provide their own sensors to read these, WebAuthn allows people to manage their credentials on the web, using their own unique traits.
WebAuthn won't be ending username and password combination, as they are still the de facto way for authentication. But it can certainly create the infrastructure needed before it can really be replaced.