People store many things on their smartphones, including sensitive data that they don't want anyone to know.
This is the fact that makes user data so tempting to have. And as for hackers, they can go to great length to get their hands on those data, in order to benefit their own, and/or make profit. And one of the ways to do that, is by using 'Ghimob', a malware that has the ability to spy on 153 apps.
Ghimob is a banking trojan that targets various Android apps from banks, cryptocurrency and exchanges.
According to the researchers at Kaspersky who discovered it, Ghimob is a “full-fledged spy in your pocket” that can be accessed remotely by its operators.
In other words, Ghimob is a RAT (Remote Access Trojan), capable of bypassing financial institutions’ security and antifraud measures, in order to make fraudulent transactions on the victim’s phones.
Initially targeting people in Brazil, the researchers warn that its operator has big plans to expand abroad, knowing that some of Ghimob's targeted apps are based outside of Brazil.
Of the 153 apps targeted by Ghimob, 112 are in Brazil.
According to Kaspersky's report:
"Our telemetry findings have confirmed victims in Brazil, but as we saw, the trojan is well prepared to steal credentials from banks, fintechs, exchanges, crypto-exchanges and credit cards from financial institutions operating in many countries, so it will naturally be an international expansion."
Ghimob infects target using methods that are also commonly used by other malware types.
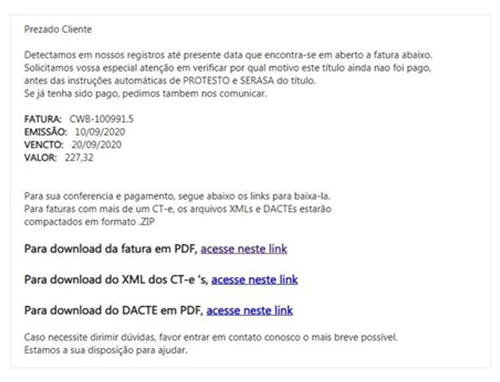
Victims are persuaded to install a malicious file via an email written in Brazilian Portuguese. This email purports to be from a creditor, and provides a link where the recipient could view more information.
That link is malicious, as it leads to an app, which pretends to be various legitimate tools, such as Google Defender, Google Docs or WhatsApp Updater.
As soon as the victims install the app through the link, the trojan will quickly work.
The first thing it does when it is installed, is sniffing out any possible emulators or debuggers. If any of such software are present, the malware will terminate itself.
“Newer versions of the malware have moved the emulator names to an encrypted configuration file,” said researchers.
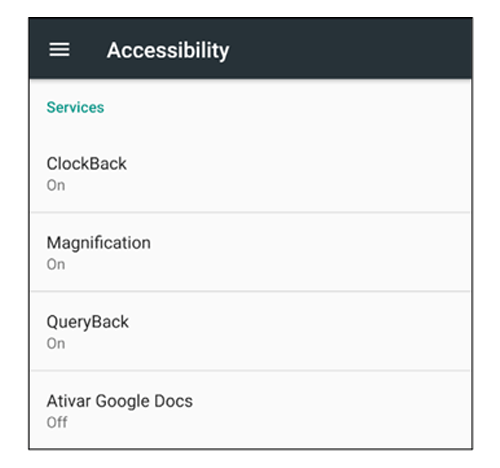
“If those previous checks are passed, the user is then presented with the default Android accessibility window, as the malware heavily relies on accessibility to work.”
After that, the malware will send a message to its command-and-control (C2) server, to send information about the victims.
This can include the victims’ phone data, including the model, whether it has a screen lock activated, and a list of all targeted apps that are installed on the victims' device, including their version numbers.
Ghimob which has screen-recording capabilities, will start recording user input, including screen lock patterns, so it can replay the pattern later to unlock the device.
When it goes to work, one of its methods is by relying on a common overlay screen tactic which is also used by Android mobile banking trojans to avoid detection.
Here, Ghimob inserts a black screen overlay, or open a website. while in the background, the trojan performs attacks to financial apps installed on the victims' phone.
While doing this, it can prevent victims from uninstalling the Ghimob-infected app. It can even prevent users from restarting or shutting down the device.
According to the researchers, Ghimob is far more advanced and richer in features, and also has a strong persistence, if compared to other banking trojans.
"It took some time for Brazilian crooks to decide to try their hand at creating a mobile banking trojan with a worldwide reach," the researchers said, adding that they believe "this campaign could be related to the Guildma threat actor, a well-known Brazilian banking trojan."
Kaspersky recommends financial institutions to watch for these threats closely. They also suggest taking measures such as “improving their authentication processes, boosting anti-fraud technology and threat intel data, and trying to understand and mitigate all of the risks that this new mobile RAT family poses.”