The Tor network is known to be one of the best way to remain anonymous on the web. But it's the Tor's exit node that seems to be the network's big weakness.
In order for a Tor user to browse the web, information is delivered from the source to the destination by bouncing it through multiple nodes. Through each of these nodes that information is decrypted layer by layer to reveal the next node in the circuit to pass the remaining encrypted data.
And when it's about to exit, the information needs to be decrypted to the innermost layer of encryption so the target can understand what's within it.
But even without revealing or knowing the source IP address, the exit relays are where the user traffic leaves the Tor network and accesses the public internet.
These are the points where data can be read.
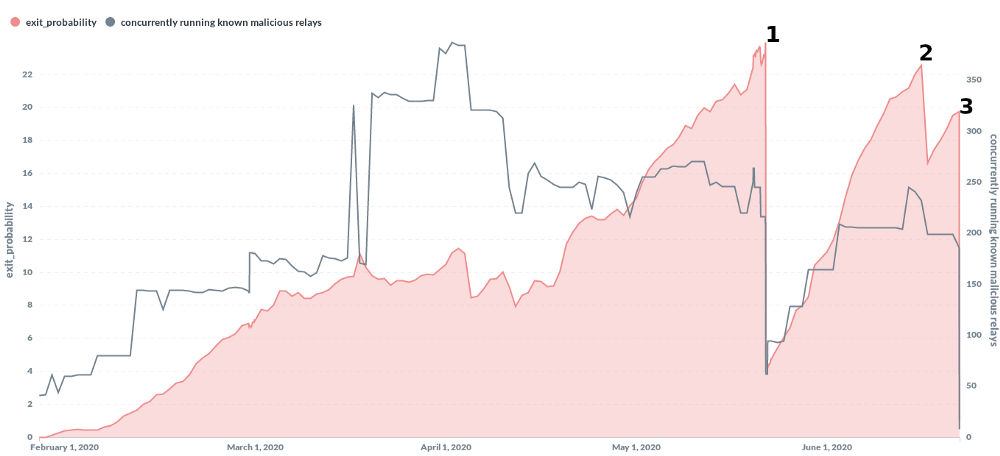
And here, a mysterious threat actor has been adding many servers to the Tor network in order to perform SSL stripping attacks, by adding servers to the Tor network since January 2020.
The hacker added new servers in a persistent manner that by May 2020, the hacker managed to run 380 malicious Tor exit relays at its peak.
At the time, that was 23.95% of all available Tor exit relays.
Controlling about a quarter of all exit nodes, any user using the Tor browser to run through the Tor network, had a one-in-four chance of landing on a malicious exit relay controlled by the hacker.
That according to a report published by an independent security researcher and Tor server operator known as Nusenu.
When the Tor team realized this, the team made the first of the three interventions to stop this growing network of exit node relays from further compromising users' privacy.
Nusenu said he has been reporting the malicious exit relays to the Tor team since May. And after the takedown on June 21, Nusenu found that the hacker's capabilities have been severely reduced.
But still, Nusenu found that "there are multiple indicators that suggest that the attacker still runs >10% of the Tor network exit capacity (as of 2020–08–08)."
The security researcher suggested that the hacker is very likely to continue attacking, considering that it still controls a handful of exit nodes, and acknowledging that the Tor Project doesn't really have a thorough vetting process in place.
"The full extend[sic] of their operations is unknown, but one motivation appears to be plain and simple: profit," said Nusenu.
The researcher said that the group is performing " person-in-the-middle attacks on Tor users by manipulating traffic as it flows through their exit relays," and that the group is specifically and Tor users that access cryptocurrency-related websites, namely multiple Bitcoin mixer services.
Bitcoin mixers are websites that allow users to send Bitcoin from one address to another by breaking the funds in smaller sums, to then transfer them through thousands of intermediary addresses before re-joining the funds at the intended destination address.
By replacing the destination address at the HTTP-traffic level, the hacker can effectively hijack user's funds without the users' knowledge, or the Bitcoin mixer's knowledge.
This is done by doing "SSL stripping" attacks, which downgrades users' web protocol from the secure HTTPS to the less secure HTTP alternative. If that happens, data can be manipulated as they pass through the Tor exit nodes controlled by the hacker.
The goal is to replace the Bitcoin addresses inside the HTTP traffic that goes to the Bitcoin mixing services.
"Bitcoin address rewriting attacks are not new, but the scale of their operations is," the researcher said.