Hackers are those people who are experts in breaching computer security through networks and various connections. Not only that, as they are known to improvise.
It has always been a cat-and-mouse game between hackers and cybersecurity companies. It's either one or the other who excel, before the race repeats itself. And this time, hackers are utilizing a known strategy to hack into systems, by tweaking the methods a bit.
As warned by Microsoft, the company informed its Office 365 customers that they're being targeted by a widespread phishing campaign aimed at stealing usernames and passwords.
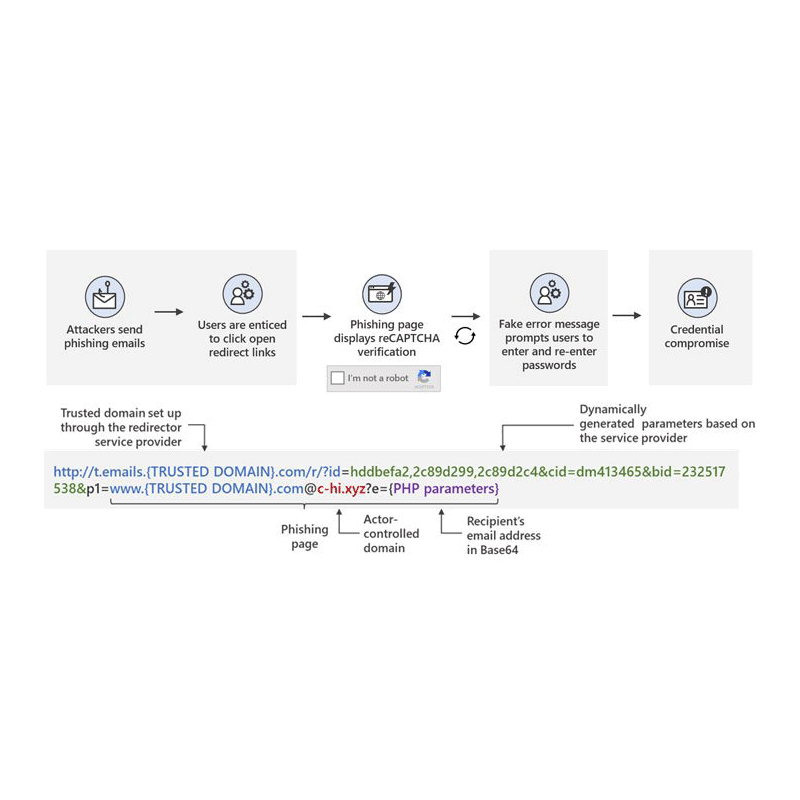
The hacking campaign uses multiple links, called 'open redirects'.
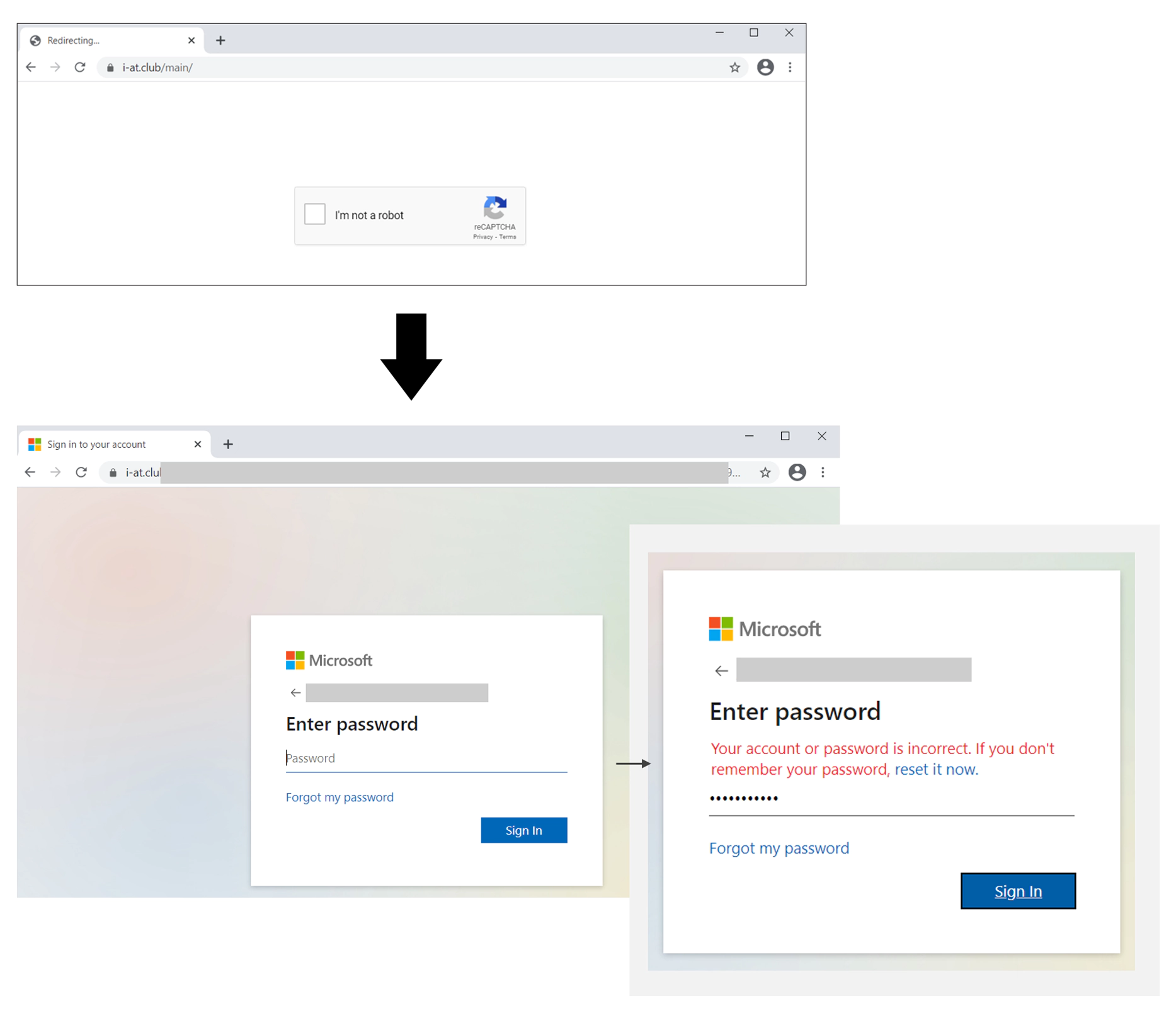
When victims visit a link the hackers have provided, a series of redirections will occur, which will then lead to a Google reCAPTCHA page.
Solving the reCAPTCHA will lead the victims into a phishing page, where Office 365 credentials can then be stolen.
In the past, it's advised for internet users to hover on links to know where that link will lead them to.
But this hacking method is immune to the link hover technique because it uses multiple redirections, before the final redirection leading to the bogus page.
Hackers do this not only to avoid the link hover technique. The main goal is to use the redirections to disguise the bogus page behind a Google reCAPTCHA page.
Not only Google reCAPTCHA prevents bots from Google or Microsoft from following the links, as it also adds human verification, putting an apparent legitimacy that visitors of the bogus page are humans and not bots.
This 'open redirects' method has been abused in the past. And in this case, Google doesn't rate open redirects for Google URLs as a security vulnerability.
What it does, is only displaying a 'redirect notice' in the browser.
Knowing this, the hackers utilize the open redirects to phish victims out of their credentials.
It should be noted that the phishing page can ask users to enter their credentials twice, by saying that the first attempt is wrong. This allows the attackers to ensure they obtain the correct password.
"However, attackers could abuse open redirects to link to a URL in a trusted domain and embed the eventual final malicious URL as a parameter. Such abuse may prevent users and security solutions from quickly recognizing possible malicious intent," the Microsoft 365 Defender Threat Intelligence Team said.
"Once recipients hover their cursor over the link or button in the email, they are shown the full URL. However, since the actors set up open redirect links using a legitimate service, users see a legitimate domain name that is likely associated with a company they know and trust. We believe that attackers abuse this open and reputable platform to attempt evading detection while redirecting potential victims to phishing sites," Microsoft warned.
"Users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it," it said.
At the moment of the warning, Microsoft has found over 350 unique phishing domains used in this campaign, including free email domains, compromised domains, and domains automatically created by the attacker's domain generation algorithm.
The email subject headers are specifically tailored to the targets, in order to fool the targets into believing that it's the real thing.
Headers include a calendar alert for a Zoom meeting, an Office 365 spam notification, or a notice about the widely used but ill-advised password expiry policy.
While open redirects aren't new, and neither are open redirects attacks, hackers know that people hover on links, and reCAPTCHAs block bots. Using the knowledge, the open redirects attack gets a twist, which makes them even more efficient.