Some malicious actors deploy malware to grab any identifiable information about victims, including location. To do that, various techniques can be deployed.
First and the most simple, is by grabbing victims' IP address, the numerical label assigned to devices when they connect to the internet. By running the IP addresses against IP-to-geo databases, the malicious authors can pinpoint victims' approximate geographical location.
This technique while easy to deploy, isn't the best around, mainly because it isn't at all accurate. This happens because telecommunication companies and data centers can acquire or rent the IP addresses on the free market, making IP blocks being assigned to different organizations in other regions of the globe from their initial/actual owner.
Because of this, malware authors tend to also rely on other information found inside the victims' system to determine the victims' more accurate, or actual physical location.
Then there is the second method, as discovered by Xavier Mertens.
The security researcher found that a malware strain is grabbing victims' BSSIDs.
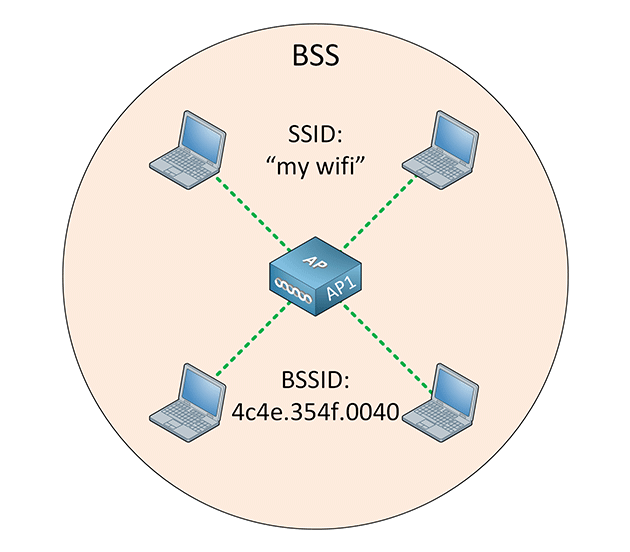
Known as a "Basic Service Set Identifier," BSSID is basically the MAC physical address of the wireless router or access point (AP) the user is using to connect via Wi-Fi.
In other words, BSSID is the MAC address of the AP’s radio, a unique address that identifies the AP. All wireless clients have to connect to the AP, meaning that the AP’s signal range defines the size of the Basic Service Set (BSS).
Mertens said that the malware he discovered was collecting BSSID of victims, and then checking it against a free BSSID-to-geo database maintained by Alexander Mylnikov.
The free database maintains a collection of known BSSIDs and their last known geographical locations.
It should be noted that the ability to obtain BSSID and people's location data through online databases isn't anything new. Usually, this is done by mobile app developers who couldn't directly locate their users' location due to rejected app permission and so forth.
But in this case, malware authors in checking victims' BSSID on that kind of databases allow them to effectively determine the physical geographical location of the Wi-Fi access point the victim was using to access the internet.
By running both victims' IP addresses and BSSIDs, malware authors can confirm that the initial IP-based geolocation query is correct with the second BSSID method.
In other words, malware authors can double-check their victims' location to ensure that they are located where they say they are.
In a blog post, Xavier Mertens said that:
The method is nothing new, but malware authors may want to go to all the troubles to pinpoint their victims' location down to their accurate physical location, most likely because they want to make sure that their victims are the actual targets.
Since IP-to-geo databases are not accurate, the malware authors know that they cannot rely only on victims' IP addresses if they want to target people inside specific countries (like during state-sponsored hacks), or if they don't want to infect victims in their native country (like to avoid attention from local authorities).
While using BSSID-to-geo database a second method to double-check a victim's geographical location isn't widely adopted, the technique has benefits, and this can be troublesome when other malware authors decide to implement the method as well.