
The underground business of malware has evolved tremendously, and for end users, this can mean a lot of things.
Some forms of malware aren't anymore controlled or utilize by their developers, as distribution model like 'malware-as-a-service' is gaining attention. Take the Raccoon malware for example.
Using this distribution model, the creators can make their product available to clients worldwide over the internet, by offering clients 24×7 customer support, features like an easy-to-use automated backend panel, and more.
In turn, the creators can earn money by selling the license, and at the same time leverage their product, and receive good reviews from 'happy clients'.
This time, Dharma, another malware-as-a-service, has its source code available on sale for just a couple of thousands of dollars on dark web forums.
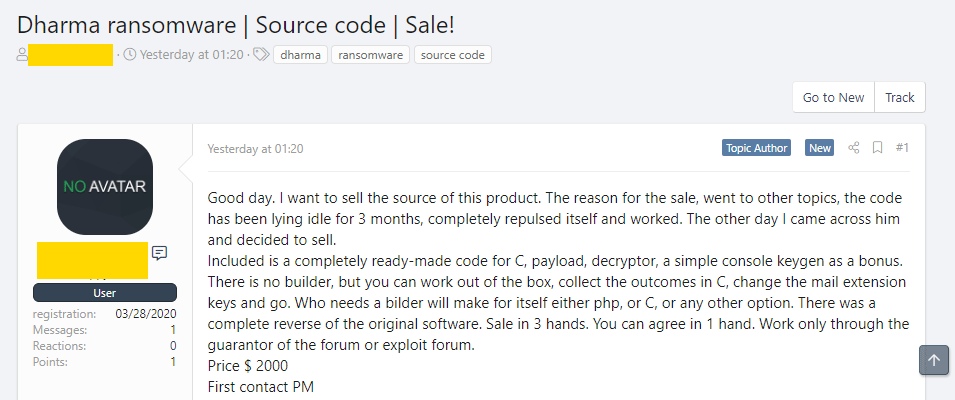
Dharma has came a long way since 2016.
After an anonymous source posted the CrySIS decryption keys online in 2016, and again several times through 2017, the CrySIS RaaS variant was restarted under the name Dharma.
Dharma is commonly delivered via spam email as a Trojan in software installers. It is also commonly installed over RDP connections via leaked user credentials.
After being installed on a victim's computer, this high-risk ransomware-type virus will first delete all of its victim's Windows Restore Points, to then use AES-256 encryption to encrypt practically every file type, while skipping system and malware files.
it then creates registry entries to maintain its persistence.
The malware is said to have targeted several healthcare in the U.S., with its developers frequently updating the malware to produce encrypted files with different extensions.
Dharma victims have even included security surveillance cameras in Washington DC, but most of the time, the ransomware attacks small businesses and charge as little as $1,500 for file recovery.
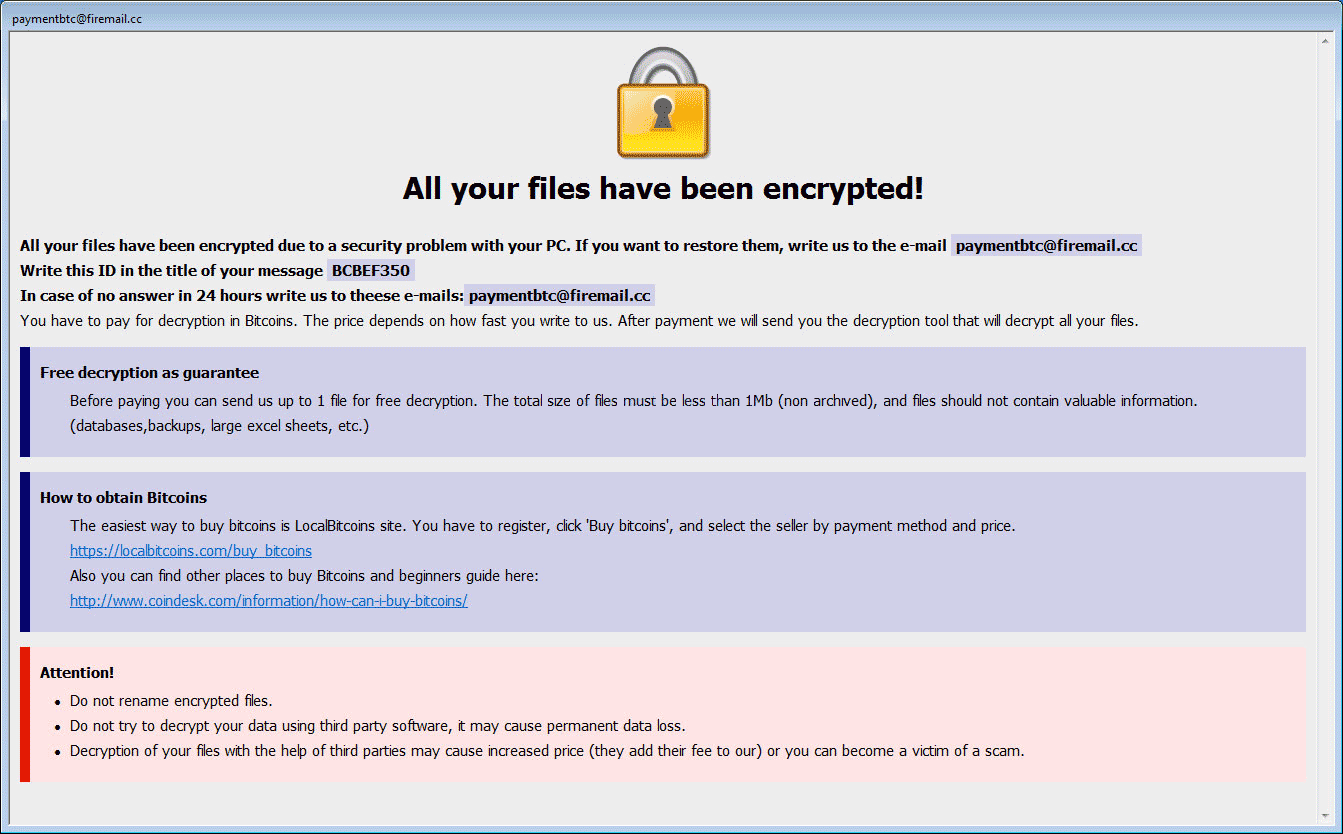
PC security analysts strongly advise computer users against paying the Dharma ransomware ransom.
This is because it's very unlikely that the people responsible for Dharma will provide the means to decrypt the infected files, especially in the case of the ransomware is still under development.
For years, there has been a steady stream of new versions of Dharma as the ransomware received updates and new customers signed up to distribute it all over the world, each of which diffused its unique unique Dharma variation.
And with its source code available to the general public, there is no saying what damage can be done if it falls to the capable cybercriminals.
For example, a wider proliferation between various cybercrime groups can happen, as well as a possible expansion of attacks using Dharma-derived ransomware tools.
According to the FBI at the 2020 RSA Security Conference, CrySIS/Dharma was the second most profitable ransomware variant on the internet, netting $24.48 million from November 2016 to November 2019.
This is about 40% of the profits made by the leader, Ryuk, or three times more than the number three earner, BitPaymer.