Apple's iOS ecosystem is supposed to be one of the safest for consumers. But apparently, there is one big flaw.
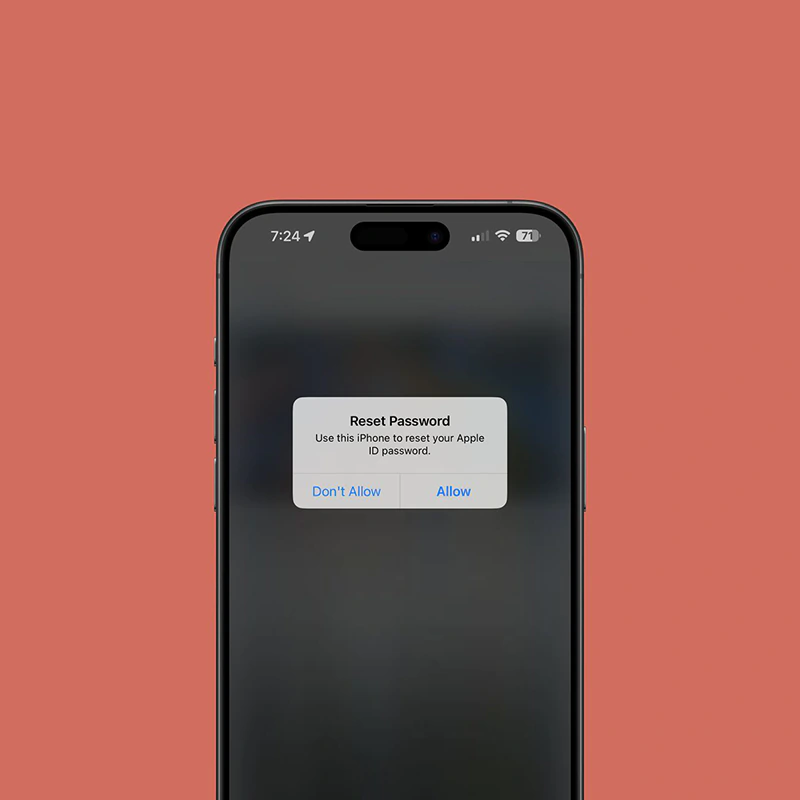
As it was realized, Apple has a password rest tool that can accessed by anyone. Scammers are using this tool to spam their targets with dozens, if not hundreds, of notifications, asking the users to reset their Apple ID password. Pressing the 'Allow' option will make the scammers one step closer to resetting the user's credentials.
This is because pressing allow would allow that to be used to create a new Apple ID password.
Unfortunately, tapping on the 'Don't Allow' on all the notifications doesn't solve the problem.
It's 'Push Bombing', the scammers are persistent, and they're good at it.
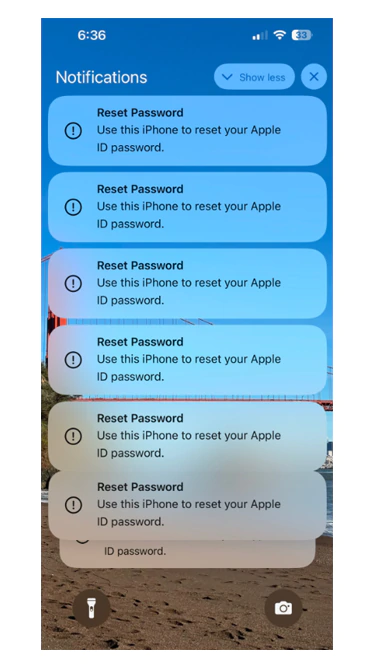
Assuming that users didn't have their fingers to accidentally slip and tapping on the 'Allow' button, or if the 'MFA Bombing' attack doesn't make targets to experience 'MFA Fatigue' or that feeling of tiredness and annoyed of seeing the notifications and press that 'Allow' button, the scammers have another trick up their sleeves.
And that it calling the targets claiming that they were from Apple's support team.
Because the attack method is to get pass Apple's multi-factor authentication, the goal of the call was to send a password reset code to the user's device, and then have the user tell them the code.
Armed with that information, the scammers could simply reset the Apple ID password and get full access to the user's account.
What this means, the victims can be locked out permanently from their Apple account.
It's unclear how many Apple users have been impacted by this MFA bombing attack.
However, according to a post by Krebs on Security, victims include those using iPhones, Apple Watches, and Macs, suggesting the attack isn't just limited to one type of Apple device.
What's worse, there's no simple way to stop it.
Krebs on Security said that some victims have called Apple for help, and that the company responded by saying they should create a recovery key, a 28-character code that they would need to input to change their Apple ID password.
However, after creating a recovery code, Krebs on Security reported that it was still possible to trigger the notifications the users saw when targeted by the spammers.
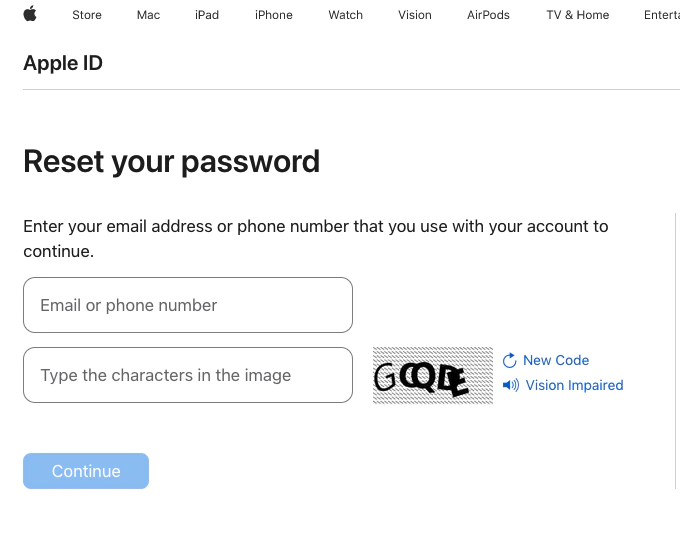
It appears Apple's password reset feature may be to blame and until the company changes how that works, hackers could conceivably continue to exploit the flaw and target users.
"We are aware of reports that a small number of iPhone users are receiving a high volume of alerts asking if they are attempting to reset their password and have taken steps to address the reported issue," a spokesperson for the company said.
Before Apple makes changes to how the tool works, Apple users must stay in the know and remain vigilant.
If ever they receive a slew of password reset requests that they didn't initiate, be sure to always choose the 'Don't Allow' option on the notifications, no matter how tiring it is.
Don't be tempted to choose 'Allow' for any reason.
Additionally, Apple has made it clear that the company does not call any of its users directly.
Phishing attacks have been used for more than many years, targeting unsuspecting victims. Since users account can hold so many data, including personal identifiable information, sensitive information, as well as financial data, scammers have increasingly turned to phishing as a desirable way to steal people's accounts.
