While most online conversations happen on social media networks and messaging apps, the old and traditional email is still widely used, especially among businesses.
When using emails, with the many ways people can send files to others, one of the best way is to simply embed a link, and not the whole file itself. Not only that it's more convenient, it's also easier and faster, because it doesn't require upload or download..
Since almost everything on the web has its own URL, this is somehow unfortunate.
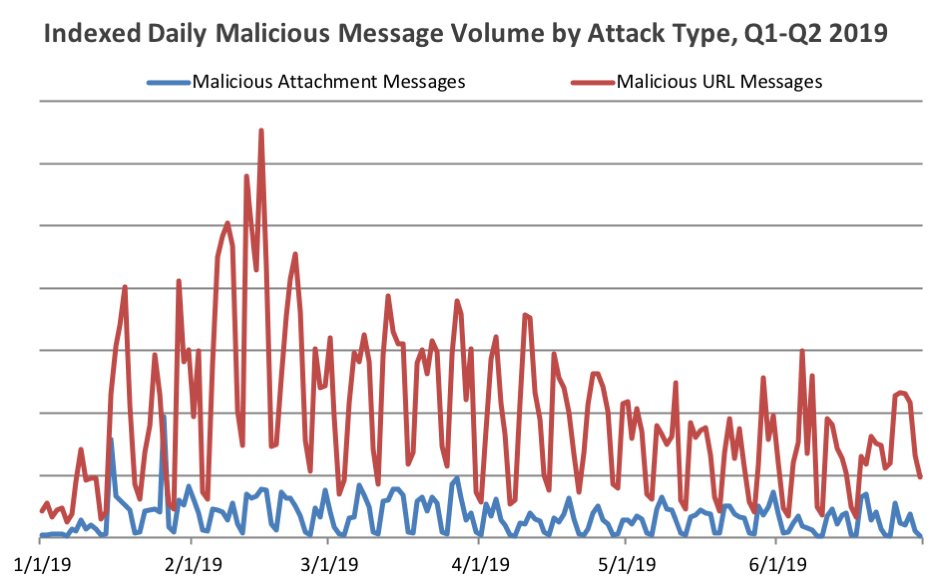
According to telemetry gathered by cyber-security firm Proofpoint, the report found that 85% of all malicious email spam (malspam) sent in Q2 2019 contained URLs, and not attachments.
The trend somehow continued the Q1 trend, where malicious URLS were also dominating the distribution of malware via email.
Email providers have become better in finding malware inside attachments. And as a matter of fact, people have also been conditioned to always be suspicious when receiving attachments from unknown sender, more than when they see links.
"While the reason for the continued dominance of URLs may be due to a range of factors, it is likely that most end users have been conditioned to be suspicious of attachments in unsolicited email," Proofpoint said. "URLs, on the other hand, are increasingly common in business email as we regularly receive notifications of shared files and collaboration updates via email as organizations move to the cloud."
Based on the facts, cyber criminals are ramping up their efforts to be more efficient in delivering more compelling emails to lure their victims.
As a result, cyber criminals are getting higher clickthroughs and infections when compared to the classic technique of attaching files to emails.
This highlights a previous Proofpoint report that found that 99% of all email-based cyber attacks require human interaction (open files, click on links, or carry out certain actions).
Other findings from the Proofpoint's Q2 2019 Threat Report, include:
- 57% of all malspam uses domain spoofing.
- Botnet-based malware was the most popular malware payload sent via malspam campaigns, accounting for 37% of all emails.
- Botnet malware was followed by banking trojans (23%), infostealers (16%), malware loaders (8%), remote access trojans (6%), and backdoor trojans (5%).
- As in recent quarters, ransomware was virtually absent in Q2.
- Ursnif accounted for 80% of all banking trojan payloads sent via email. It was followed by URLZone, The Trick, and Dridex.
- The ranking for infostealer had Pony in front, followed by AZORult, Loki Bot, and Formbook.
To minimize the chances of infection, and for companies to protect their data, customers, and brands, Proofpoint recommends:
- Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
- Build a robust defense against impostor attacks. This solution must also be scalable, and where possible, should include full implementation of DMARC.
- Look for a comprehensive domain fraud solution that scans the web and reports fraudulent and suspicious activity.
- Partner with a threat intelligence vendor, and leverage a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets.