Username-password alone is not anymore sufficient to protect user accounts. This is where multi-factor authentication (MFA) solutions can help.
But according to the U.S. Federal Bureau of Investigation (FBI) in a security advisory to private industry partners, the rising threats of attacks against organizations and their employees have included methods that can bypass MFA solutions.
Most notably, the methods used included: SIM swapping, using vulnerabilities in online pages handling MFA operations, and using transparent proxies like Muraen and NecroBrowser.
According to a report from ZDNet, the FBI sent out a Private Industry Notification (PIN) on September 17th that said:
In other words, there are actually multiple ways for malicious actors to bypass MFA protections.
To explain the matter, here are some listed incidents where hackers bypassed MFA and steal money from companies and regular users alike:
- In 2016, customers of a U.S. banking institution were targeted by a cyber attacker who ported their phone numbers to a phone the attacker controlled. The attack used was the SIM swapping method.
- Over the course of 2018 and 2019, the FBI's Internet Crime Complaint Center and FBI victim complaints observed SIM swapping as a common tactic from cyber criminals seeking to circumvent two-factor authentication. Victims of these attacks have had their phone numbers stolen, their bank accounts drained, and their passwords and PINs changed. Many of these attacks rely on socially engineering customer service representatives for major phone companies, who give information to the attackers.
- In 2019, a U.S. banking institution was targeted by a cyber attacker who was able to take advantage of a flaw in the bank's website to circumvent the two-factor authentication implemented to protect accounts, using a manipulated string into the Web URL to set the attacker's computer as the one recognized on the account.
- In February 2019, a cyber security expert at the RSA Conference in San Francisco, demonstrated a large variety of schemes and attacks cyber actors could use to circumvent multi-factor authentication. Examples include: man-in-the-middle attacks, session hijacking to intercept the traffic, social engineering attacks, phishing schemes or fraudulent text messages purporting to be a bank or other service to cause a user to log into a fake website and give up their private information.
- In June 2019's Hack-in-the-Box conference in Amsterdam, cyber security experts demonstrated Muraena and NecroBrowser, which worked in tandem to automate a phishing scheme against users of multi-factor authentication.
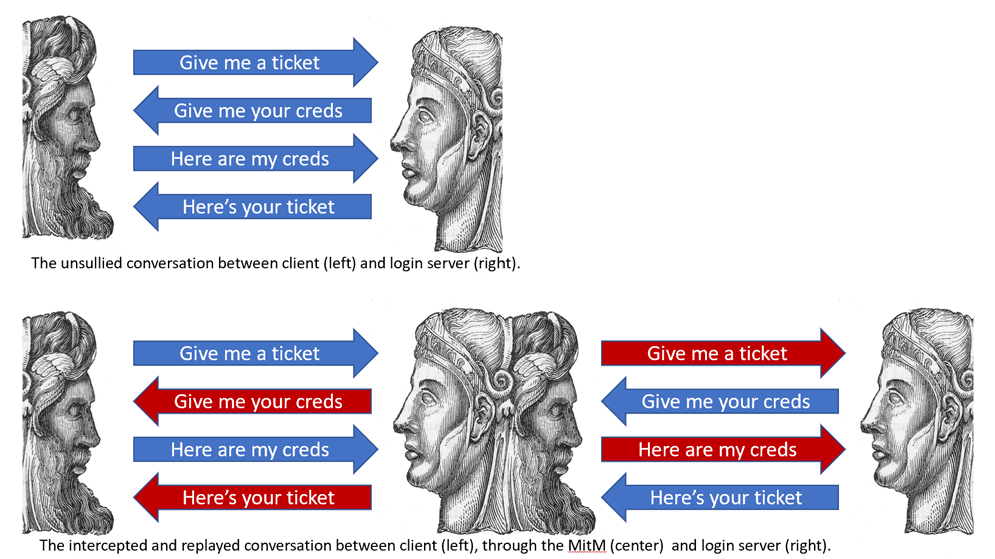
Unless companies employ “biometrics or behavioral information—such as time of day, geolocation, or IP address,” there are risks that an attack can either trick a user into disclosing a MFA code or use technical interception to create one for themselves, said the FBI.
While the warning should alert everyone who uses MFA to secure their accounts, the FBI made it clear that its report should only be taken as a precaution.
The agency is still recommending MFA solutions, as they can protect users much better than using none at all. Here, the FBI only wants users of MFA solutions to be aware that cyber-criminals are already leveraging methods to bypass such account protections.
"Multi-factor authentication continues to be a strong and effective security measure to protect online accounts, as long as users take precautions to ensure they do not fall victim to these attacks," the FBI said.
Despite the rise of hacks that bypassed MFA, the number of successful attacks is still incredibly low. This is because the methods of bypassing MFAs have not been automated at scale.
Microsoft for example, said that when MFAs are enabled, the protection method should help users block 99.9% of hacks. Attacks that bypassed MFAs are so rare that the company didn't even have the statistics on them.
Previously, Google also said a similar thing, when it claimed that users who added a recovery phone number to their accounts (enabling SMS-based MFA) have improved their account security.
"Our research shows that simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks that occurred during our investigation," Google said at the time.
What this means, MFAs in general are still very effective at preventing most mass and automated attacks.