One of the easiest ways for hackers to hack, is by planting malware. And the easiest way to plant malware, is by piggybacking existing resources.
Security firm Check Point has a surveillance campaign that has been going on for years, and has been stealing a wide range of data on Windows and Android devices used by Iranian expatriates and dissidents.
Calling it 'Rampant Kitten', the researchers said that its main goal is to steal Telegram messages, passwords, and two-factor authentication codes sent by SMS.
It can also take screenshots, and record sounds through infected devices' microphone, the researchers said in a blog post.
Among the different attacks the researchers found, include:
- Four variants of Windows infostealers intended to steal victims’ personal documents as well as access their Telegram Desktop and KeePass account information.
- An Android backdoor that extracts two-factor authentication codes from SMS messages, records the phone’s voice surroundings, and more.
- Malicious Telegram phishing pages, distributed using fake Telegram service accounts.
According to the researchers, the above tools and methods appear to be mainly used against Iranian minorities, anti-regime organizations and resistance movements.
They include those like the Association of Families of Camp Ashraf and Liberty Residents (AFALR), Azerbaijan National Resistance Organization, and the Balochistan citizens.
The researchers first found the campaign when they were observing the document name called: وحشت_رژیم_از_گسترش_کانونهای_شورشی.docx, which roughly translates to “The Regime Fears the Spread of the Revolutionary Cannons.docx”.
The title of the document itself was already referring to the ongoing struggle between the Iranian regime and the Revolutionary Cannons.
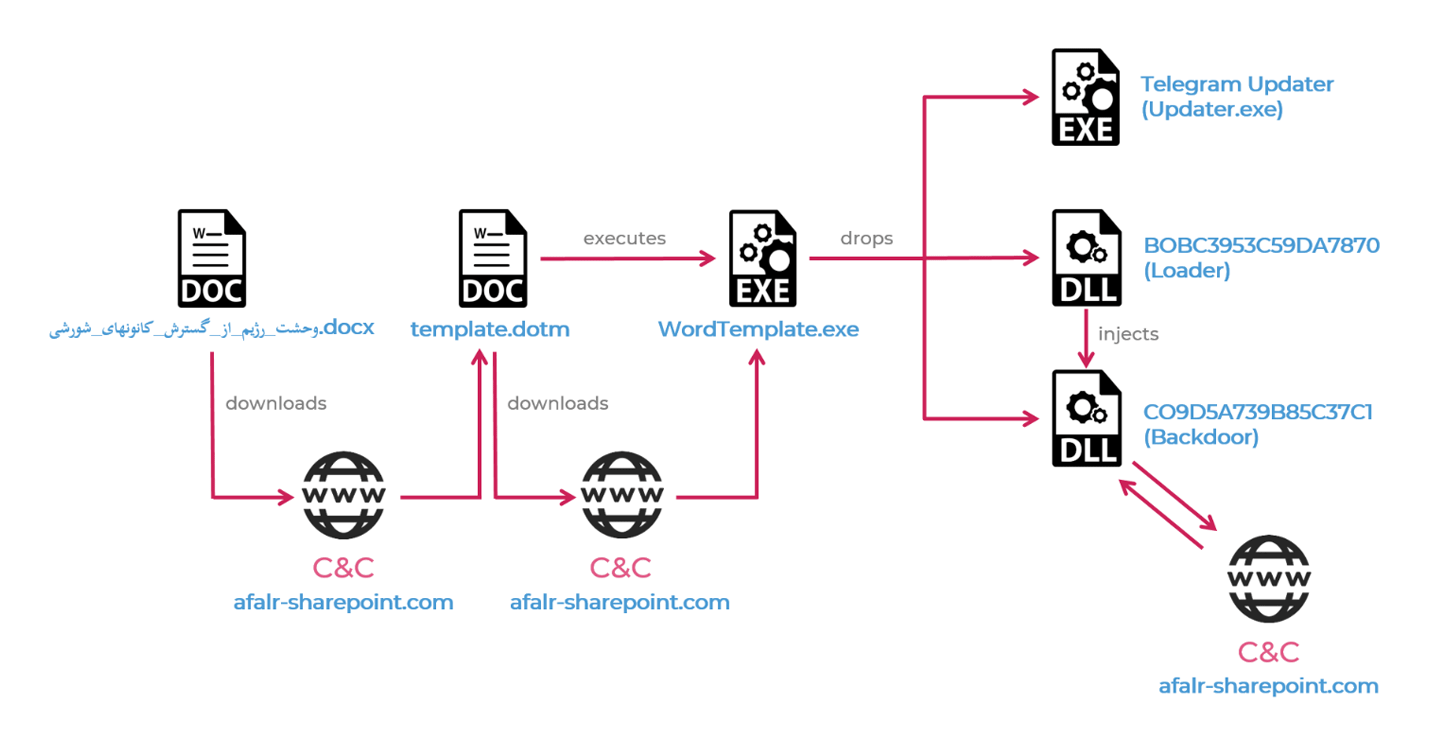
The document uses external template techniques, which allows it to load a document template from a remote server.
When victims open the infected document, the remote template will download. After that, it will run malicious macros, and tries to download and execute the next payload. If that payload is successfully installed, the malware can start checking if Telegram is installed in the infected machine.
If it found that it is installed, the malware proceeds by extracting three additional executables.
- Information Stealer: This in order to make full usage of victims' Telegram account, steal sensitive information, upload files, logs clipboard data, and take screenshots.
- Module Downloader: To download and install additional modules.
- Unique Persistence: A method to stay persistent based on Telegram’s internal update procedure.
"According to the evidence we have gathered, the threat actors, who appear to be operating from Iran, have been taking advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices, and their supposedly private, secure communications via Telegram and other social networks,” Check Point researchers wrote.
Since most of the targets the researchers identified are Iranians, it appears that similarly to other attacks attributed to the Islamic country. The researchers called those attacks operation ‘Domestic Kitten’.
In the 2018 blog post, the researcher named it that way to make it in line with the naming of other Iranian APT attacks.