Security researchers have discovered vulnerabilities that compromised hundreds of GPS services. Dubbed the 'Trackmageddon', the flaws on affected GPS services could enable attackers to steal sensitive data.
Two security researchers, Vangelis Stykas and Michael Gruhn, detailed the security issues. They said that the Trackmageddon affects several GPS services that harvest geolocation data of users from a range of smart GPS-enabled devices, including car trackers, children trackers, pet trackers and others
The vulnerabilities include easy-to-guess passwords, exposed folders, insecure API endpoints, and insecure direct object reference (IDOR) issues.
By exploiting these flaws, hackers can have their hands on personally identifiable information collected by those location tracking devices. They include: GPS coordinates, phone numbers, device model and type information, IMEI numbers, and custom assigned names.
To make the matter worse, some of those devices can give unauthorized access to third-party individuals where they can steal photos and audio recordings uploaded using those location tracking devices.
According to the researchers, ThinkRace which is one of the largest global vendors for GPS tracking devices, may have been the original developer of the flawed location tracking online service software and seller of licenses to the software.
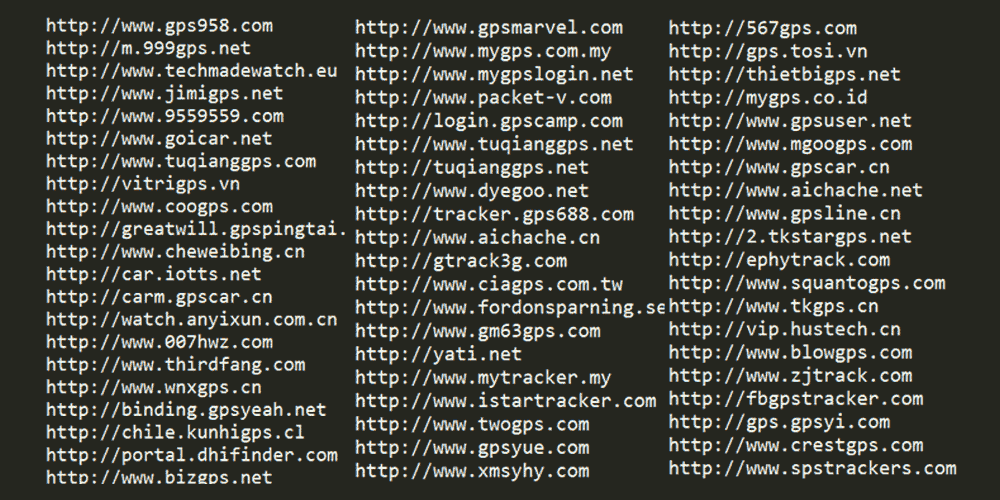
While the affected ThinkRace domains have been fixed, devices that are still using the same flawed domains, are still vulnerable. According to the research, more than 70 domains are still vulnerable.
What's more, vendors that attempted to patch vulnerabilities, the fix can end up in creating new unwanted issues.
"We tried to give the vendors enough time to fix (also respond for that matter) while we weighted this against the current immediate risk of the users,"
"We understand that only a vendor fix can remove user’s location history (and any other stored user data for that matter) from the still affected services but we (and I personally because my data is also on one of those sites) judge the risk of these vulnerabilities being exploited against live location tracking devices much higher than the risk of historic data being exposed."
"There have been several online services that stopped being vulnerable to our automated proof of concept code, but because we never received a notification by a vendor that they fixed them, it could be that the services come back online again as vulnerable."
Stykas and Gruhn recommended some suggestions to avoid these vulnerabilities, which includes removing data from the affected devices, changing the password for the tracking services and use a stronger one, or stop using the affected devices until there are clear fixes in place.