Whenever and wherever there is money involved, there will be scammers and tricksters.
Knowing that people use smartphones to do just about anything, malicious actors target those people using malware to steal sensitive data. And among the most dangerous malware types, is remote access trojans, or RATs, which can be programmed to do insidious things when installed on victims' phones.
This time, cybersecurity researchers at Cleafy reported that the 'TeaBot' malware is gaining traction.
The team found that there's a huge increase in the number of TeaBot targets, in which the malicious actors behind the malware are targeting at least 400 apps used for banking, cryptocurrency transactions, and digital insurance.
According to the researchers, has malicious actors have begun targeting victims in Russia, Hong Kong, and the United States.
"In less than a year, the number of applications targeted by TeaBot have grown more than 500%, going from 60 targets to over 400," the researchers wrote in a post on Cleafy's website.
TeaBot is an Android banking trojan, and has been around since at least 2021.
Originally, the malware tried to lure in users via "smishing," or fake SMS messages from innocent-looking services embedded with malicious links.
At the time, TeaBot somehow diminished, and was thought to have disappeared.
Unfortunately, it hasn't been fully vanquished.
According to Cleafy, the malware has been updated with more ways to creep into people's phones.
This particular malware operates using "on-device fraud," in which it manipulates accessibility services of the devices it managed to infect. The malware then affects the device's live-streaming ability in a way that permits attackers to remotely interact with phones and monitor them.
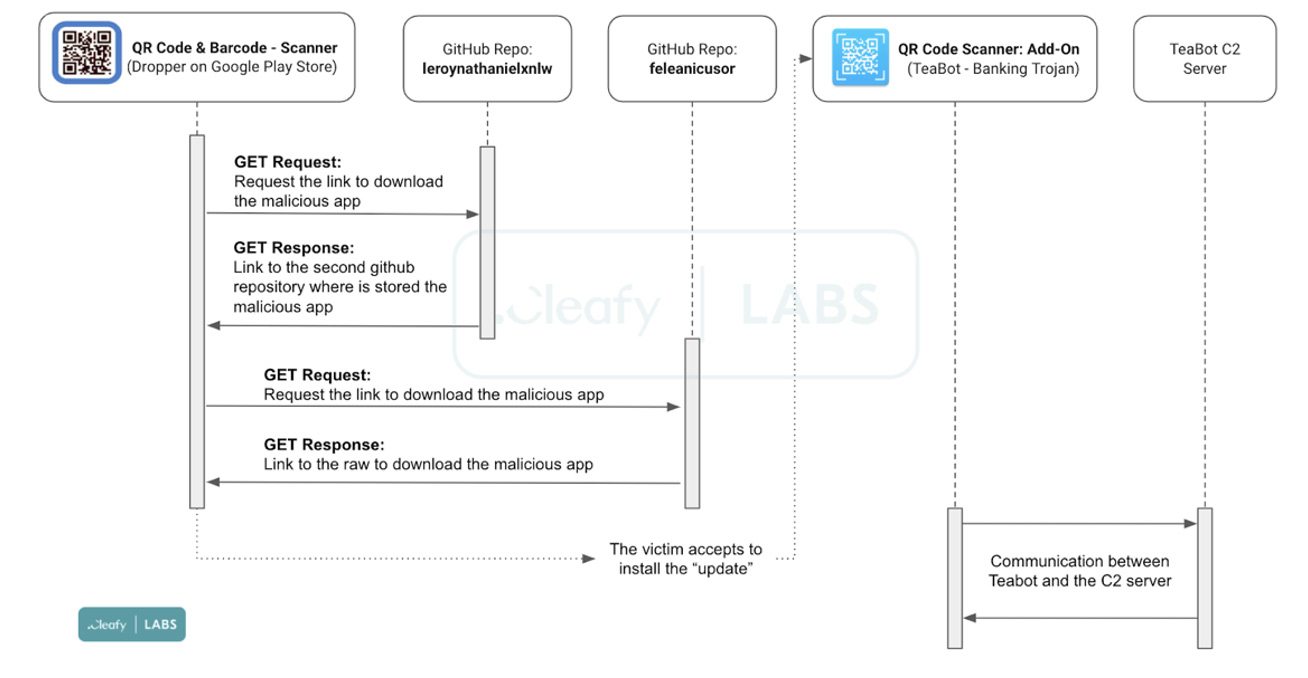
In an example, one QR code app found on Google's Play Store functioned as a dropper for the malware.
Unsuspecting users of the app would think that they've downloaded a legit app. And indeed, the app did what it is supposed to.
The thing is, the app also asks users to install an add on, which tricks users to sideload.
The malware does this by cleverly abusing Github service for hosting the actual malicious payload.

If victims do what they are told, the app will successfully install the malware.
The app then asks users to grant it a number of permissions, particularly the phone's accessibility services. Granting this will allow the malware to seize control of the screen.
With this permission, the app can record login attempts, SMS, as well as two-factor authentication codes.
TeaBot's 2022 version has added more languages that include Russian and Mandarin Chinese) to target more countries, and more ways to avoid conventional detection by standard antimalware apps.
"Since the dropper application distributed on the official Google Play Store requests only a few permissions and the malicious app is downloaded at a later time, it is able to get confused among legitimate applications and it is almost undetectable by common AV solutions," the researchers explained.
What males this TeaBot trojan unique is that it requires no malicious email or text message, no fraudulent website or third-party service to spread or infect. Instead, it typically comes packaged in a dropper application, which acts as the vehicle to deliver a second-stage malicious payload.
Cleafy's researchers said that if Android users find this 'QR Code Scanner: Add-On' app installed on their phone, they should quickly remove it.
Notifying Google, the company responded by removing the app in question from its Play Store.