A software bug is something that should be eliminated, terminated, obliterated, and annahilated.
It should be squashed as soon as possible, because failure to do so, can create huge catastrophe.
And when it comes to software that runs on the internet, a failure to patch a bug can result to hacks, that would later harm end users.
This is what exactly happened on Twitter.
While the popular microblogging platform managed to patch a zero-day bug that was used to link users' phone numbers and emails to user accounts, the company took quite an amount of time before patching the bug.
The bug was found in January 2022, and was stemmed from a code change made by the company back in June 2021.
The bug allowed anyone to submit an email address or a phone number and learn which specific account was associated with the information entered.
"As a result of the vulnerability, if someone submitted an email address or phone number to Twitter's systems, Twitter's systems would tell the person what Twitter account the submitted email addresses or phone number was associated with, if any," the company said in an advisory.
While no passwords were exposed as a result of the incident, at least one hacker managed to exploit the flaw before Twitter even knew about it.
The six-month delay gave the hacker enough time to take advantage of the bug, in order to scrape user information and sell it for profit on a hacking forum.
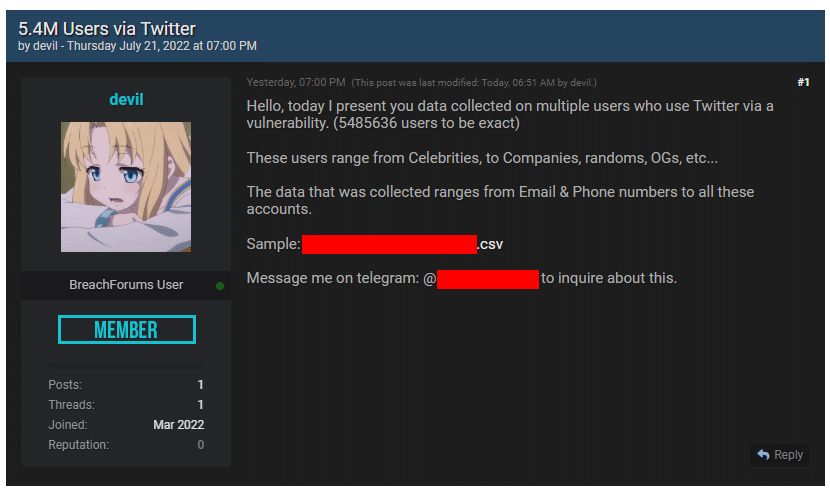
Twitter didn't say anything much about the exact number of affected users, but the forum post by the threat actor suggests that the flaw allowed the threat actor to compile a list containing allegedly over 5.48 million user account profiles.
The data includes: user name, real name, location, bio, followers count, status count, favorite count, account creation date, account status, profile image, email address, phone number and more.
The said database is being sold for $30,000.
"After reviewing a sample of the available data for sale, we confirmed that a bad actor had taken advantage of the issue before it was addressed," Twitter said in a blog post.
Realizing this, Twitter stated that it is notifying all affected account owners of the issue, while also urging users to turn on two-factor authentication as an extra layer of security to protect their accounts.
When two-factor authentication is turned on, iInstead of only entering a password to sign in, users are also required to enter a code or use a security key.
"This additional step helps make sure that you, and only you, can access your account. During enrollment, we’ll also make sure you have a confirmed email address associated with your account. That way, we can use your email address for things like communicating with you to keep your account secure," Twitter explained in a dedicated help page.
This news came after Twitter, in May, agreed to pay a $150 million fine to settle a complaint from the U.S. Justice Department that alleged the company between 2014 and 2019 used information account holders provided for security verification for advertising purposes without their consent.