Since 2018, billionaire and tech's serial entrepreneur Elon Musk has launched thousands of satellites to the Earth's orbit, through Starlink, a satellite internet constellation operated by SpaceX.
Through these satellites, Starlink is able to beam internet connections to places anywhere on Earth. Users are only required to own a Starlink User terminal (UT) and its dish, and a subscription. Among others, Starlink has been a vital source of connectivity during Russia’s war in Ukraine.
Because the device uses quality materials, and also because it uses SpaceX to launch the satellites, Starlink is often regarded as a product with space-grade quality.
The thing is, that is not true.
Lennert Wouters, a security researcher at the Belgian university KU Leuven, has disassembled a Starlink UT and its dish, and managed to hack into Starlink's system and access locked parts that aren't available to him.
He was even able to attack Starlink's satellite system itself, if he wanted to.
The first thing Wouters did, was physically stripping down a Starlink dish he purchased.
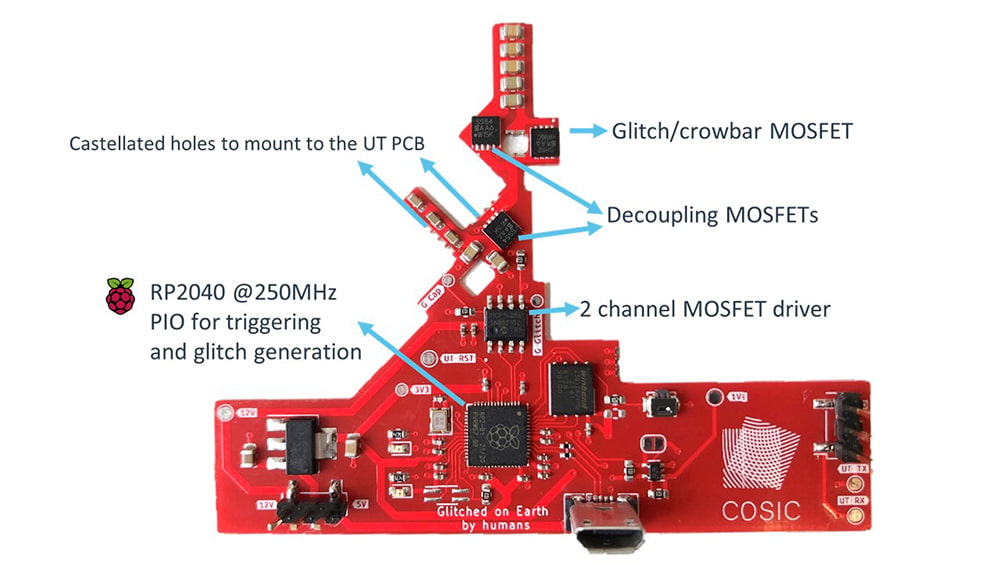
The Belgian researcher then purchased a custom circuit board known as modchip, and assembled it using off-the-self parts that costed his around $25.
His homemade printed circuit board (PCB), which consists of a Raspberry Pi microcontroller, flash storage, electronic switches and a voltage regulator, was designed it to fit over the existing Starlink board.
After that, he soldered the modchip, and connected Starlink's PCB to it using only a few wires.
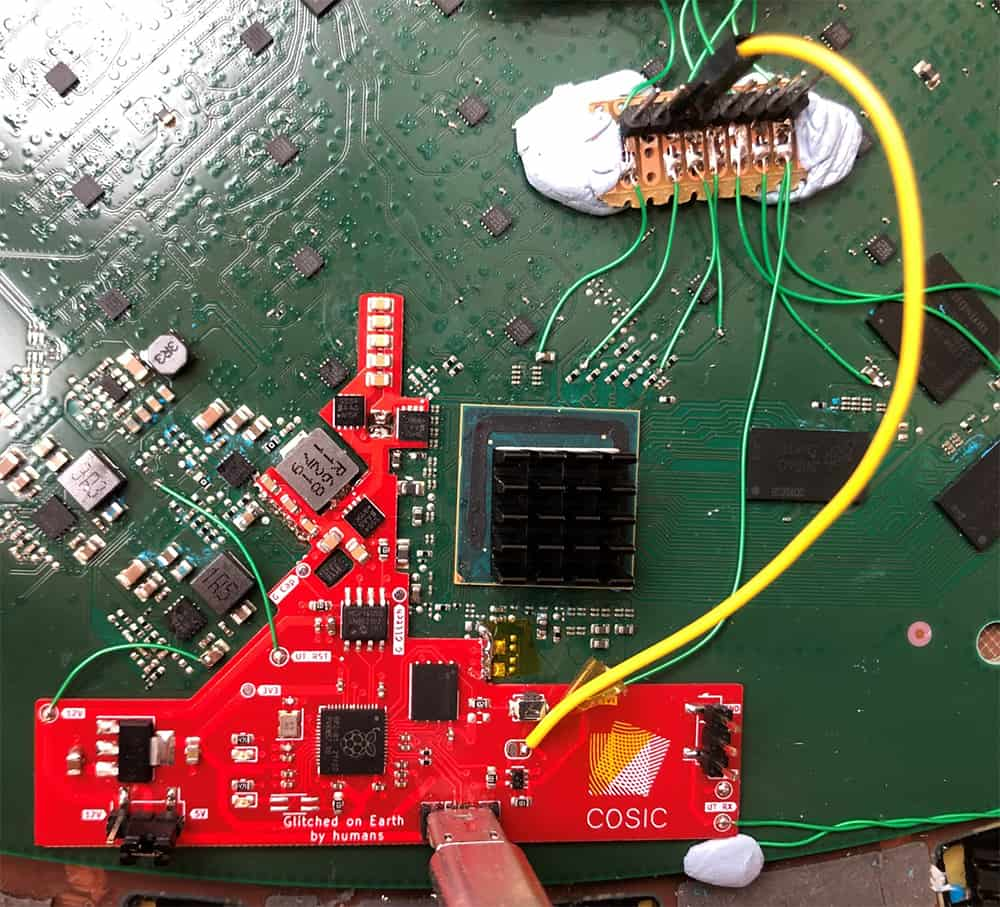
After that, Wouters was able to initiate a fault injection attack, which temporarily short circuited the system.
He did this by stopping the decoupling of the capacitors, which are used to smooth out the power supply, from operating.
This allowed him to bypass Starlink's security protections, and doing so allowed him to have deeper access to the system.
Wouters then deployed his own firmware, which gave him control of the dish, according to the report.
"As an attacker, let’s say you wanted to attack the satellite itself," Wouters explained, "You could try to build your own system that allows you to talk to the satellite, but that’s quite difficult. So if you want to attack the satellites, you would like to go through the user terminal as that likely makes your life easier."

In short, what Wouters did was bypassing signature verification security checks, a security system which is designed to prove that the system is launching correctly and hasn’t been tampered with.
Wouters' method involved multiple stages of attacks. He also had a number of measures before he boldly launched his voltage fault injection attack to "glitch" his Starlink system.
His first performed the attack in a lab before implementing the modchip on the dish itself, he revealed in a write-up about his presentation published on the conference’s website.
The attack runs the glitch against the first bootloader, which is the Starlink UT's ROM bootloader.
This component is located inside the device's system-on-chip, meaning that it cannot be updated.
The researcher notified Starlink of the flaws last year and the company paid Wouters through its bug bounty scheme for identifying the vulnerabilities. Wouters said that while SpaceX has issued an update to make the attack harder, the underlying issue can only be fixed if the company creates a new version of the main chip.
Before that happens, all existing user terminals are vulnerable, concluded Wouters.
“Our attack results in an unfixable compromise of the Starlink UT and allows us to execute arbitrary code,” Wouters wrote. “The ability to obtain root access on the Starlink UT is a prerequisite to freely explore the Starlink network.”
"We’re using this to accurately time when to inject the glitch," said Wouters.
"From a high-level view, there are two obvious things that you could try to attack: the signature verification or the hash verification," Wouters explained. The glitch works against the signature verification process.
"Normally you want to avoid shorts," he said. "In this case we do it on purpose."
Initially, Wouters attempted to glitch the chip at the end of its boot cycle. This is the stage when the Linux operating system has fully loaded. But in the end, Wouters found it a lot easier to cause the glitch at the start of the boot.
This way, according to Wouters, is more reliable.
"I think it’s important to assess how secure these systems are because they are critical infrastructure," Wouters said. "I don’t think it's very far-fetched that certain people would try to do this type of attack because it is quite easy to get access to a dish like this."
Wouters has revealed his finding in a presentation called “Glitched on Earth by Humans” at the annual Black Hat ethical hacker conference.
Wouters has made his hacking tool open source on GitHub, in which he also detailed the things needed to launch the attack.
It's worth noting that Wouters has also revealed the vulnerability to SpaceX in a responsible way through its bug bounty program, before publicly presenting the issue to the public.
I am excited to announce that our talk "Glitched on Earth by humans" will be presented at @BlackHatEvents!
I will cover how we glitched the Starlink User Terminal SoC bootrom using a modchip to obtain root.
This might be the first tweet sent through a rooted Starlink UT! #BHUSA pic.twitter.com/0XMMIidEKk— Lennert (@LennertWo) May 19, 2022
Just like any other forms of technologies, the increase use and deployment of Starlink UTs mean that threat actors have a greater interest in exploiting security holes.
In the past, there has been a number of teardowns of Starlink’s user terminals since the company started selling them. Engineers on YouTube have also opened up their terminals, exposing how the components work, while others have also discussed the specifications in details on forums, including on Reddit.
Knowing the critical nature of its security, SpaceX has responded to Wouters’ presentation with a six-page paper (PDF), inviting security researchers to “bring on the bugs” to help the company better protect the Starlink system.
SpaceX has also offered detailed explanation of how it protects Starlink.
The paper also congratulates Wouters’ research, calling it “technically impressive,” The company also assured users that Starlink’s “defense-in-depth approach to security limits the overall impact of this issue to our network and users.”
Starlink is SpaceX’s low Earth orbit satellite constellation, an ambitious project from Elon Musk that aims to provide satellite internet coverage to the whole world.

And here, Starlink’s UT is one of three core components of the Starlink system.
The first are the satellites that move hundreds of kilometers above the Earth's surface to beam down internet connection, and the second are the gateways that transmit connections up to the satellites.
UTs are the consumer-grade devices that communicate with the satellites, in order to provide internet access.
It uses greater power delivery than the more common Power over Ethernet (PoE) which is usually limited to about 30 watts. Starlink UTs are able to run on higher power due to its custom PoE that uses 90 to 100 watts in operation. This required the devices to use well-shielded cables to sustain the heat.
As for the antenna itself, it contains a self-contained computer, complete with an ARM processor and RAM that are connected to the PCB, in what appears to be custom-made silicon designed specifically for SpaceX.
Before this, Wouters created hardware that can unlock a Tesla in 90 seconds, looked at the security of the terminal and its chips.
"The user terminal was definitely designed by capable people," he said at the time.