Virtual Private Networks, or VPNs, are essentially encrypted connections in which data can be transferred through a secure "tunnel".
This allows companies to allow employees to access corporate networks from outside the office. For personal uses, commercial VPN services can protect users internet traffic from eavesdroppers by routing it through remote servers. In theory, VPN has become an important part of internet security.
But no matter how good VPNs are, they are only as secure as the software that makes them.
WireGuard is one of the protocols used by VPN services.
The free and open-source software runs as a module inside the Linux kernel for better performance that the IPSec or OpenVPN tunneling protocol.
Developed by Jason A. Donenfeld and is published under the GNU General Public License (GPL), WireGuard approaches VPN tunneling with simplicity.

WireGuard claims that:
Usually, the more complex a software is, the more difficult it is to audit security issues.
IPSec for example, is known to be complex. With more than a hundred thousand lines of code in its makeup, each has the potential to be the backdoor for hackers. OpenVPN itself is also complex, and famously slow to run, and again, also hard to secure.
In comparison, the first version of WireGuard VPN only had less than 4,000 lines of code.
Due to its simplicity, debugging is a lot faster for WireGuard than its IPSec and OpenVPN counterparts.
But this smaller size doesn't make WireGuard less secure, as the VPN already repackaged cryptography by focusing on ciphers.
Donenfeld believes that ciphers are among the more secure encryption method. WireGuard here supports cryptography technologies such as the Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, and HKDF.
WireGuard protocol is compatible with a range of other platforms.
For mobile users, WireGuard has been designed as a “stealth VPN,” meaning that it doesn't send any packets by default, unless there’s actual data to be sent. This way, WireGuard can reduce the amount of “chatter” associated with the VPN powered by its protocol, resulting in the cut down of the amount of information potentially available for eavesdroppers or packet sniffers to get a hold of.
This approach also extends mobile device battery life.
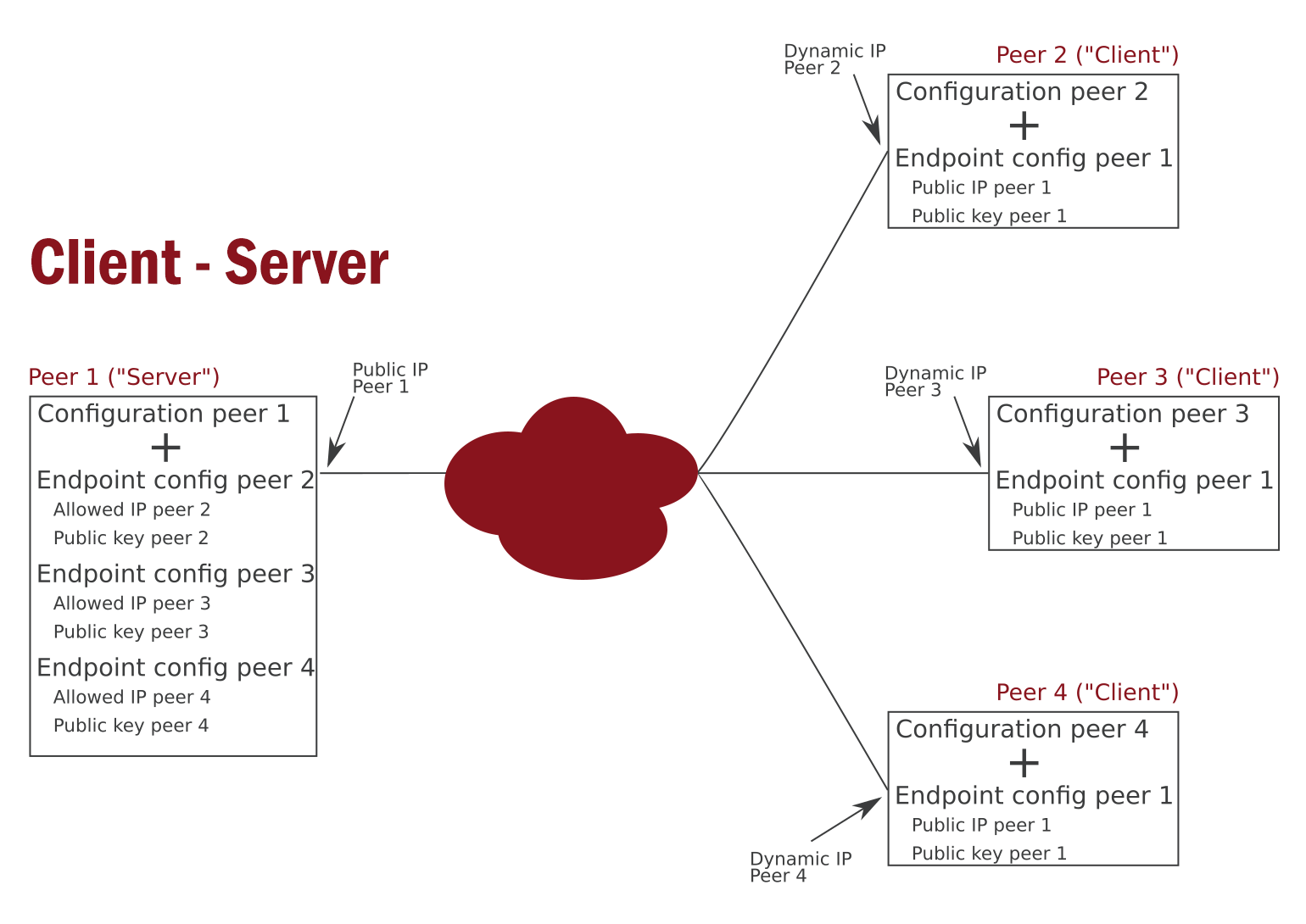
At its heart, WireGuard boasts a process called Cryptokey Routing. The method works by associating public encryption keys with a list of VPN tunnel IP addresses which are allowed inside the tunnel.
When a connection is established, a unique private key is created and a list of peers is associated with each network interface. Each of the peers has a short and simple public key that is used for authentication with other peers. The public keys may be distributed for use in configuration files in a number of ways, similar to the transmission of SSH public keys.
In any server configuration, each peer (client application, etc.) can send packets to the network interface by having a source IP address that matches its corresponding list of allowed IP addresses. When the network interface wants to send a packet to a peer, it should first look at the destination IP of the data packet, and compares that to each peer’s list of allowed IPs, in order to determine which peer to send it to.
The list of allowed IP addresses works like some sort of routing table when transmitting packets, and also as a kind of access control list, when receiving them. WireGuard calls this a Cryptokey Routing Table.
When a VPN uses the WireGuard protocol, its configuration contains an initial endpoint for its destination server, so that the service knows where to send encrypted information before it has received any. For security purposes, the configuration of the server doesn’t contain any initial endpoints for its clients (peers).
Instead, the server is left on its own to discover the endpoints of its peers, by scanning the location from which the authenticated data is coming from. This method also forces the client to continue track the server, and update the configuration whenever a new server endpoint is created.
And as for the encrypting and decrypting processes, they all happen on the most recent IP endpoints.
Advantages of WireGuard
- Quick and easy setup.
- Small code base.
- Focus on a few but modern cryptographic techniques.
- Supports many operating system variants.
- The ability to switch between WLAN and mobile connection without noticeable interruption.
- Fast connection setup
- Faster than IPSec and OpenVPN.
- Open-source project.
Disadvantages of WireGuard
- Restrictions for VPN application purposes in the area of anonymization.
- The protocol cannot be used without logging, meaning that user activities should be recorded.
- No dynamic IP assignment, as clients need to have a fixed IP.
WireGuard's approach has been praised by the Linux kernel creator Linus Torvalds.
When compared to OpenVPN and IPsec, Torvalds consider WireGuard as a "work of art", "hard to go back" and "no nonsense" instant reconnections.
This was why he wanted WireGuard to work deep inside the Linux kernel, to allow the software to communicate directly to the operating system, in order to make the protocol work even faster.
This way, WireGuard can also encrypt and decrypt data directly from the network card, instead of having the data to flow back and forth between the kernel and software at a higher level.
What this means, WireGuard changes many things in the way Linux kernel work.
And since essentially all VPNs run off Linux servers, the entire VPN world changes.
Though initially designed and optimized for running inside the Linux Kernel, WireGuard can be adapted for a number of different platforms. For example, WireGuard may be used on systems running Ubuntu, macOS, and Android.
Read: How WireGuard VPN Can Change The Linux Kernel To A Better Operating System
