
Google said that it has removed 1,700 unique apps that have the billing fraud malware called the Bread.
Also known as the 'Joker', the malware that has been around since at least June 2019 is designed to surreptitiously sign users up for premium service subscriptions. In addition, the malware can also steal victim’s SMS messages, contact list, and device information.
Back in September 2019, Google managed to remove several Joker-ridden apps. This time, the tech juggernaut managed to remove a lot more.
The company said that the apps were removed before users could even download them.
But it's the sheer volume that appears to be the preferred approach for Bread developers.
At different times, Google researchers have seen three or more active variants using different approaches or targeting different carriers. Within each variant, the malicious code present in each sample may look nearly identical with only one evasion technique changed.
For example, sample 1 may use AES-encrypted strings with reflection, while sample 2 can use the same code but with plaintext strings.
"At peak times of activity, we have seen up to 23 different apps from this family submitted to Play in one day. At other times, Bread appears to abandon hope of making a variant successful and we see a gap of a week or longer before the next variant. This family showcases the amount of resources that malware authors now have to expend. Google Play Protect is constantly updating detection engines and warning users of malicious apps installed on their device," said the researchers.
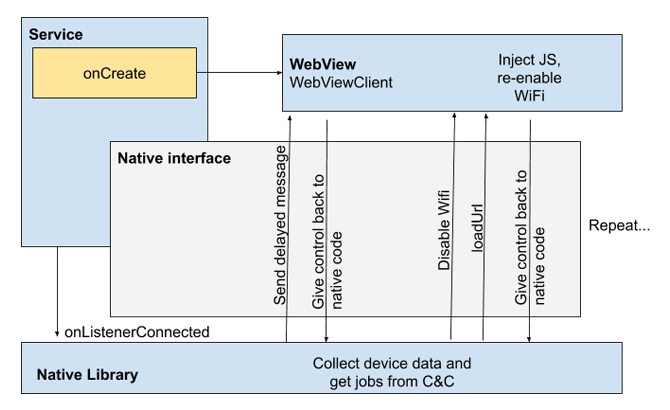
According to Google researchers:
While Google is capable of better detecting the Joker malware, the bad news is that developers are still making their ways to put apps with the Joker malware to the Play Store, by improvising their methods.
The Joker malware's developers continually change their tactics to search for gaps and weaknesses in Google Play Store's defenses.
"They have at some point used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected," Google says.
The malware managed this by receiving its dynamic code and commands over HTTP, and runs that code via JavaScript-to-Java callbacks. This essentially makes lots of its malicious instructions not hard-coded into the app.
This provides the malware an extra layer of protection against static analysis.
The Joker malware can use " just about every cloaking and obfuscation technique under the sun in an attempt to go undetected. Many of these samples appear to be designed specifically to attempt to slip into the Play Store undetected and are not seen elsewhere,” wrote Google researchers Alec Guertin and Vadim Kotov, in a blog post.