
Google Play Store boasts protections that come from Google itself, powered by one of the most powerful AIs and search capabilities unmatched by others.
But that doesn't mean the app store is free from malware and apps with malicious intentions. In the past, Google has struggled to police its Play Store with various malware issues. And this time, things are just repeating again and again.
According to a report disclosed by cybersecurity firm CSIS Security Group, a malware called 'the Joker', is designed to surreptitiously sign users up for premium service subscriptions.
In addition, the malware can also steal victim’s SMS messages, contact list, and device information.
The Joker that has been around since at least June 2019, is just another instance of ad fraud malware. In total, CSIS found 24 Android apps on Google Play containing the malware, which successfully received more than 472,000 downloads by unsuspecting Android users.
The apps in question include:
- Advocate Wallpaper.
- Age Face.
- Altar Message.
- Antivirus Security – Security Scan.
- Beach Camera.
- Board picture editing.
- Certain Wallpaper.
- Climate SMS.
- Collate Face Scanner.
- Cute Camera.
- Dazzle Wallpaper.
- Declare Message.
- Display Camera.
- Great VPN.
- Humour Camera.
- Ignite Clean.
- Leaf Face Scanner.
- Mini Camera.
- Print Plant scan.
- Rapid Face Scanner.
- Reward Clean.
- Ruddy SMS.
- Soby Camera.
- Spark Wallpaper.
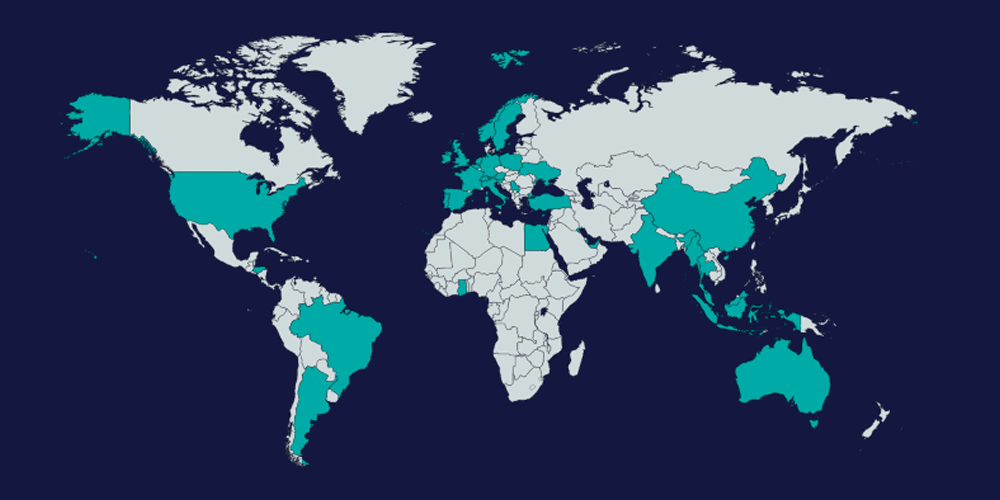
According to the report, the Joker has claimed victims in 37 countries:
Australia, Austria, Belgium, Brazil, China, Cyprus, Egypt, France, Germany, Ghana, Greece, Honduras, India, Indonesia, Ireland, Italy, Kuwait, Malaysia, Myanmar, Netherlands, Norway, Poland, Portugal, Qatar, Republic of Argentina, Serbia, Singapore, Slovenia, Spain, Sweden, Switzerland, Thailand, Turkey, Ukraine, United Arab Emirates, United Kingdom and United States.
"The Joker malware only attacks targeted countries," the report said.
"Most of the infected apps contain a list of Mobile Country Codes (MCC) and the victim has to be using a SIM card from one of these countries in order to receive the second stage payload. The majority of the discovered apps target the EU and Asian countries, however, some apps allow for any country to join. Furthermore, most of the discovered apps have an additional check, which will make sure that the payload won’t execute when running within the US or Canada."
According to CSIS, the malware not only obfuscates the modus operandi of delivering the actual malicious payload from the command-and-control (C&C) server owned by the attacker. It’s also been programmed to generate "as little footprint as possible" by hiding itself within advertisement frameworks used by the apps.
The malware managed this by receiving its dynamic code and commands over HTTP, and runs that code via JavaScript-to-Java callbacks. This essentially makes lots of its malicious instructions not hard-coded into the app.
This provides the malware an extra layer of protection against static analysis.
Fortunately, following CSIS finding, Google removed those apps from its platform.
