
Bluetooth is one of the methods for people to transfer data and files to different platforms. And again researchers found a critical bug in the technology.
The flaw resides in the Bluetooth Low Energy (BLE). Called the 'BLE Spoofing Attack' (BLESA), according to seven researchers at Purdue University, the flaw affects the reconnection process that occurs when users' device moves back into range after previously losing or dropping its pairing.
Normally, when reconnecting, the two BLE devices should check each other's cryptographic keys negotiated during the first pairing process, in order to reconnect and continue exchanging data.
But the researchers discovered that the official BLE specification didn't contain strong-enough language to describe the reconnection process.
This area is often overlooked by security researchers. Most researches on BLE security issues were focused on the pairing process, and not on the BLE protocol itself.
And here, the flaw in the Bluetooth Low Energy (BLE) allows hackers to initiate spoofing attacks, that could affect the way devices carry out their tasks.
To initiate an attack, hackers can exploit denial-of-service attacks to make Bluetooth connections go offline. This will automatically trigger a reconnection operation on demand, and this is where the hackers can execute a BLESA attack.
Safeguarding BLE devices against disconnects and signal drops is impossible.
In a paper published by the researchers, a successful BLESA attack would allow malicious actors with a device (by getting around reconnection authentication requirements) to send spoofed data to it.
Affecting billions of smartphones, tablets, laptops, and IoT devices that use BLE, those malicious packets can convince target machines to carry out different or new malicious behavior.
IoT devices in particular, are exceptionally vulnerable due to their lacked security.
For humans, hackers could feed a device to show deceptive information.
The vulnerability is particularly significant because of the ubiquity of the BLE protocol which, because of its energy efficiency and simplicity of use, is used by many devices to pair and connect.
“[...] BLE requires limited or no user interaction to establish a connection between two devices,” the researchers wrote.
The BLE protocol is designed to allow any device to connect with other BLE device to obtain its attributes. This is for convenience. BLE is a slimmer version of the original Bluetooth (Classic) standard, and designed to conserve battery power while keeping connections alive as long as possible.
“Unfortunately, this simplicity is the root cause of several security issues.”
Making things worse, BLE also facilitates access for an attack, simply because its advertising packets are always transmitted in plaintext.
What this means, hackers can easily impersonate the benign server by advertising the same packets and cloning its MAC address, the researchers explained.
Through this method, hackers can also broadcast spoofed advertising packets to ensure that whenever the client attempts to start a new session with the previously-paired server, it will receive the spoofed advertising packets again, added the researchers.
“At this point, the adversary is ready to launch BLESA against the client.”
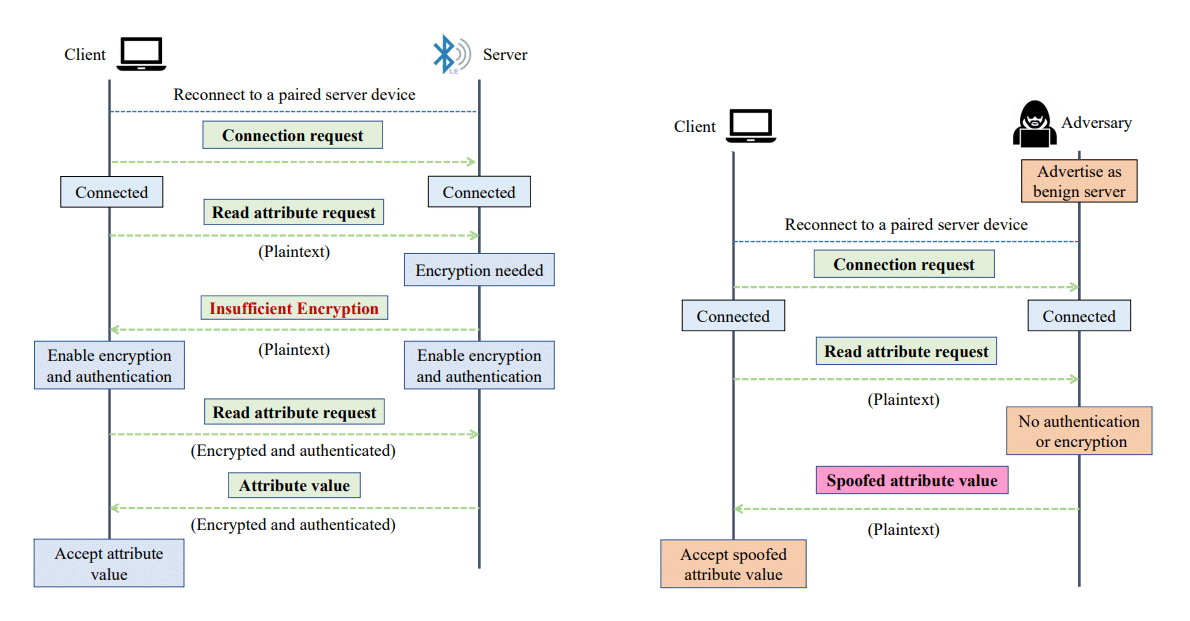
The researchers on their paper focused on two critical weaknesses in the BLE technology that allows BLESA attacks to happen.
First, as previously mentioned, is during authentication when reconnection is marked as optional instead of mandatory.
“The client and the server may choose to disable [authentication] for a specific attribute,” researchers wrote. “Therefore, in the case of the basic attribute, the confidentiality, integrity and authenticity goals of the attribute-access request and response can be violated.”
Second, is when BLE specification provides two possible authentication procedures when the client reconnects with the server after pairing. What this means, authentication can potentially be circumvented.
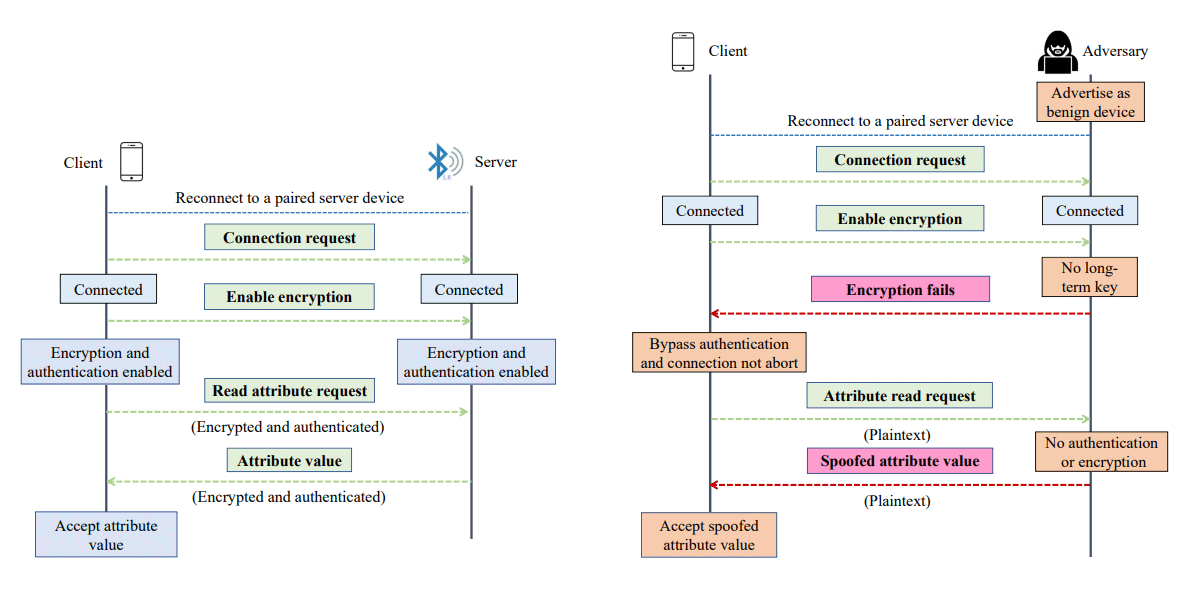
Attackers can use BLESA on BLE implementations on Linux, Android and iOS platforms, researchers said. Specifically, Linux-based BlueZ IoT devices, Android-based Fluoride and the iOS BLE stack are all vulnerable. Windows implementations of BLE however, is immune.
"As of June 2020, while Apple has assigned the CVE-2020-9770 to the vulnerability and fixed it, the Android BLE implementation in our tested device (i.e., Google Pixel XL running Android 10) is still vulnerable," researchers said in the paper.
As for Linux-based IoT devices, the BlueZ development team said it would replace the code that makes it devices vulnerable to BLESA with code that implements proper BLE reconnection procedures, immune to BLESA.
Unfortunately, it seems like the flaw is fated like previous Bluetooth bugs, in which it will remain permanently unpatched on most vulnerable devices.
The reason is because patching all vulnerable devices is a nightmare for system admins, especially since most IoT devices already sold don't come with built-in update feature.
Since patching only some devices might not be an option, they may as well leave the bug present as it is, and hoping that hackers won't be around to exploit it.
This is the second major bug found in Bluetooth this September. Previously, researchers discovered 'BLURtooth', a flaw in Bluetooth that allowed hackers within range of the wireless to bypass authentication keys and snoop on devices in a man-in-the-middle attack.