
In the modern days of technology, things are entirely based on the transfer of data and files through different systems or platforms, which can be wired or wireless.
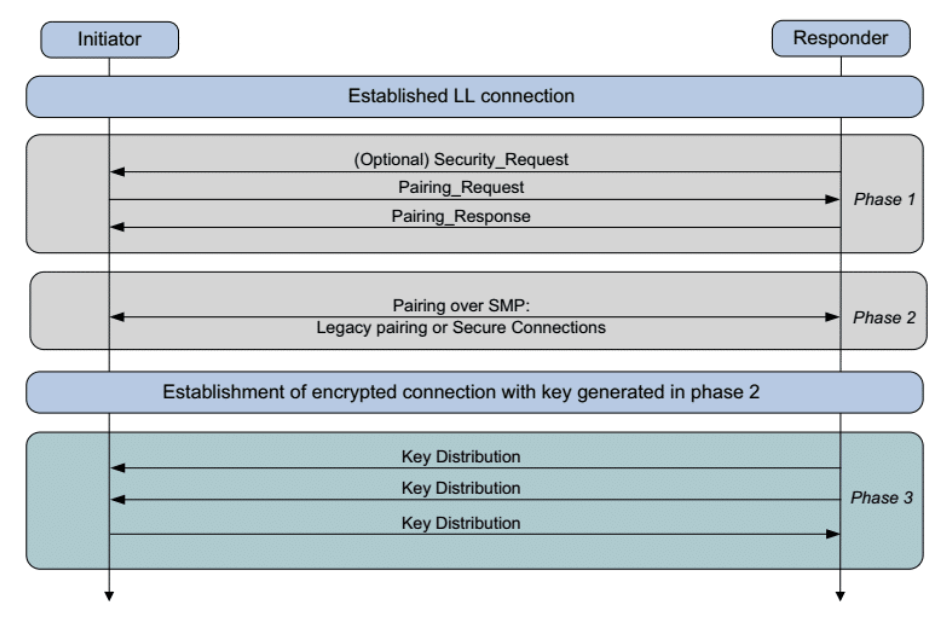
Bluetooth is one of the methods. It was not designed to transfer files and large amounts of data at a given time, but only capable of transferring data over short distances. This is done through pairing, which establishes keys that can then be used to encrypt a link between the devices.
And this time, a flaw in the pairing process was found left unpatched.
The flaw is allowing hackers to target nearby devices very easily. Bluetooth SIG, an organization that oversees the development of Bluetooth standards, has issued an official statement about this.
The organizations warns that the flaw potentially affects hundreds of millions of devices worldwide.
The flaw was discovered independently by researchers at the École Polytechnique Fédérale de Lausanne (EPFL) and Purdue University.
According to Bluetooth SIG, the flaw resides in the Cross-Transport Key Derivation (CTKD) of devices supporting both the Basic Rate/Enhanced Data Rate (BR/EDR) and Bluetooth Low Energy (BLE) standard.
CTKD is a Bluetooth component responsible for negotiating the authenticate keys when pairing two Bluetooth devices together. It's also known as "dual-mode" devices.
The flaw that is dubbed 'BLURtooth' and tracked as CVE-2020-15802, exposes devices powered with Bluetooth 4.0 or 5.0 technology, allowing attackers to connect to a targeted nearby device without authorization.
That can be done by overwriting the authenticated key or reducing the strength of the encryption key.
"Dual-mode devices using CTKD to generate a Long Term Keys (LTK) or Link Key (LK) are able to overwrite the original LTK or LK in cases where that transport was enforcing a higher level of security," the researchers explain.
"Vulnerable devices must permit a pairing or bonding to proceed transparently with no authentication, or a weak key strength, on at least one of the BR/EDR or LE transports in order to be susceptible to attack."
In other words, the flaw could allow man-in-the-middle attacks. in which the attackers overwrite authorization keys when the transport enforces a higher level of security.
To exploit the flaw, hackers using an attacking device would need to be within wireless range of a vulnerable Bluetooth device supporting both BR/EDR and LE transports that supports CTKD, in order to permit pairing with no authentication or no user-controlled access restrictions on the availability of pairing.
"If a device spoofing another device's identity becomes paired or bonded on a transport and CTKD is used to derive a key which then overwrites a pre-existing key of greater strength or that was created using authentication, then access to authenticated services may occur," Bluetooth SIG warned.
Bluetooth SIG recommends restrictions on CTKD mandated in Bluetooth Core Specification versions 5.1 and later as primary mitigation.
Following the findings, the organization has started coordinating with affected device manufacturers to help them release necessary patches rapidly.
"The Bluetooth SIG further recommends that devices restrict when they are pairable on either transport to times when user interaction places the device into a pairable mode or when the device has no bonds or existing connections to a paired device," the researchers said.
Previously in 2019, a flaw in the Bluetooth protocol was found, and was capable of exposing devices to trackers.
