A blockchain is cryptography-based technology that uses tamper-resistant distributed ledger to store data in a consensus driven, peer-to-peer network.
It enables the process of transferring value between two parties without having to rely on third-parties. Decentralized, the blockchain network has no governance by a hierarchical authority. This is a contrast to the likes of banks, credit card companies and so forth.
Because it also provides an important trust layer for transactions, blockchain plays a unique important role where it can change how modern businesses work, and capable of offering solutions that are otherwise impossible.
As with all technologies, blockchain technology, concepts, and business models are often misunderstood and misapplied. In many cases this confusion can be attributed to the difference of paradigms by permissioned and permissionless blockchain models.
Permissioned Blockchain
This blockchain model restricts the actors who can contribute to the consensus of the system state.
In a permissioned blockchain, only a restricted set of users have the rights to validate the block transactions, and it may also restrict access to approved actors who can create smart contracts. This way, the owner of a permissioned blockchain has the ability to dictate who can and cannot become part of its network, dictate the network’s structure, issue software updates, and generally control everything that takes place on the blockchain.
Information on permissioned blockchains can only be validated by approved members of that blockchain. While the owner can control who sees that information, in some cases, the public can also view certain information stored on the chain.
Other permissioned blockchains may be totally created, managed and operated in house (highly permissioned). Because permissioned blockchains are sometimes referred to as 'private blockchains', what it means is that the network cannot be accessed or read outside of the authority who controls it.
Here are some of the key characteristics of a permissioned system:
- Decentralization: The extent and quality of decentralization depends upon its members.
- Transparency: Depends upon how the business relationships are set up and how the blockchain is configured.
- Anonymity: Offers a more fine-grained access control and visibility into transaction details, along with metadata about those transactions.
- Governance: Largely decided and agreed upon by the members of the blockchain network.
- Tokens: May or may not employ a cryptoeconomic model or monetary tokens due to the nature of these business networks.
- Scalability and performance: Usually substantially better scalability and performance than its permissionless counterpart.
Permissionless Blockchain
This model is contrary to the permissioned blockchain.
Here, anyone can join the network, participate in the process of block verification to create consensus and also create smart contracts. Anyone can become part of this blockchain network and contribute to its upkeep.
Permisionless blockchain networks power up most of the market’s digital currencies. They allow every user to create a personal address, run a node to help verify transactions, run mining software/hardware, access wallet, and begin interacting with the network by submitting transactions, and hence adding entries to the ledger.
Bitcoin is the most famous example of a permissionless blockchain, as there is no barrier of entry to use it:
Because basically, permissionless blockchain allows anyone to read the chain, anyone can make legitimate changes and anyone can write a new block into the chain (as long as they follow the rules). As it's also described as a 'censor-proof' blockchain, there is no way for anyone to censor anyone else inside the network.
Permissionless in many ways, is just a fancy way of saying 'public blockchain'.
Here are some of the key characteristics of a permissionless system:
- Decentralization: The system must be decentralized and distributed, so that no one entity (or government) can bring the network down, or censor parts of it.
- Transparency: With no central governance, and for participants (miners) can be incentivized to run and trust the network, transparency is important.
- Anonymity: Miners and other participants of the network can largely stay anonymous. But blockchains still need to dictate whether or not anonymity is preferred.
- Governance: Governance model spanning both economic design and monetary policy is available.
- Tokens: There are two predominant types of tokens: monetary value tokens and utility tokens.
- Scalability and performance: The weakness in this model.
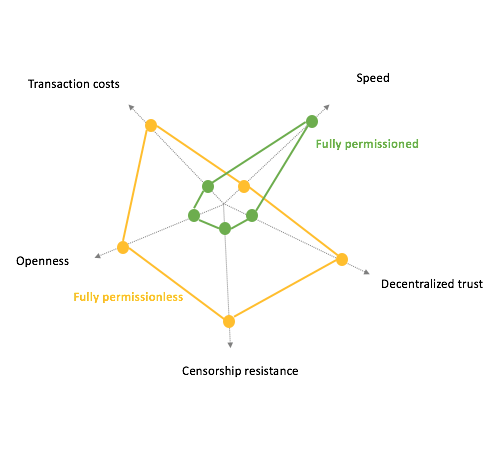
Which Is Better?
Short answer: it doesn't really matter because it is all subjectively based.
Long answer: There are three technologies that make up blockchain technology: cryptographic keys, a distributed network and a network servicing protocol. The key component of blockchain’s appeal is the immutability of transactions records; that being the inability to go back and change information that has been verified in the past.
This is secured by the consensus based Proof-of-Work algorithms that are decentralized among all the miners and nodes on the network.
Just like centralized and decentralized, permissioned and permissionless blockchain have distinct nuances of philosophy, capabilities, and adoption affordances.
Permissionless models are better suited when cryptoeconomics are part of the business model. Decentralizing the network secures the blockchain because it requires one party to convince the majority of nodes to change the content in order to change the content. On the other hand, a highly permissioned system where chosen people can control the nodes, the owner is merely opening with the same single point of failure weaknesses.
But when businesses intend to use blockchain mainly for the purpose of having a trusted, non-repudiable source of truth, using a permissioned model is a better choice.
Another choice is using a hybrid permissioned blockchains. The option would be preferred by corporations or organizations with specific needs. In this example, they want to be the central authority that act as the transaction validators, and build their own nodes in many places. But at the same time, they don't value total transparency and an end in itself, and want to allow others to transact using their token without permission.
Related: The History Of Bitcoin