Scammers are smart. They can use their knowledge and experience, as well as all the available tools at their disposal to trick victims to do their bidding.
One of the methods of scam, is called 'email spoofing', which can be described as the fabrication of an email header in the hopes of tricking the recipient into thinking that the email originated from someone or somewhere other than the intended source.
Another way of saying it: email spoofing is when someone sends an email with a forged sender address.
The ultimate goal of email spoofing is to get recipients to open, and respond to a solicitation. Which ultimately makes the recipient a victim.
Some people can quickly guess whether an email is legit, by the looks of the email's body or the subject. To those people, spoofed emails are just nuisance that require little attention besides removal. But for most others unfortunately, spoofed emails can be so tricky to spot.
Making things worse, there are more malicious varieties of spoofed email that can cause significant problems, and sometimes pose a real security threat.
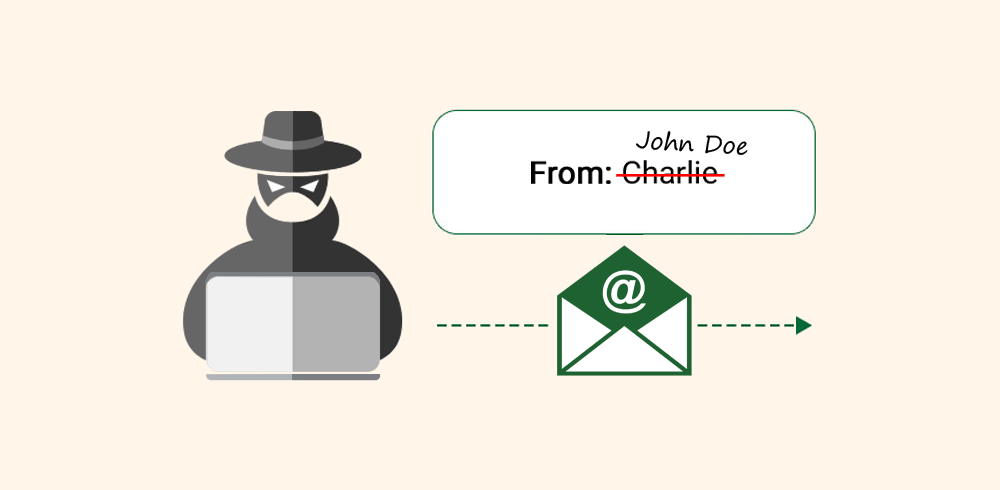
In a spoofed email, scammers can alter different sections of an email to disguise the true sender, including the following properties:
- FROM: Name and email address.
- REPLY-TO: Name and email address.
- RETURN-PATH: Email address.
- SOURCE IP: IP address.
The first three properties can be easily altered using settings in Microsoft Outlook, Gmail, or other email software. The IP address can also be altered, but this requires more technical knowledge from the scammers' side.
Email spoofing is possible because core email protocols don't necessarily have a built-in method of authentication. As a result, it's common for spammers to send phishing emails using the spoofing technique to trick recipient into trusting the origin of the message.
Examples of common spoof emails include:
- Email sent from a well-known company, asking the recipient to provide personal information like a password or credit card number.
- Email sent from a supplier, or an executive of a company, requesting wire transfer to be sent to different payment location.
- Email sent from a hacker, who claims to have hacked the recipient, and threats to expose their sensitive information to public unless paid.
- Email sent from family members or friends, asking for the recipient to open a link that ultimately collects the recipient's personal information.
The link may direct to a web page asking user account credentials, or a method to disguise a malware. In this case, when clicked, the malware will download and installs itself on the recipient's device.
Email spoofing is very common. And here is what you need to know to protect yourselves and your data.
The first thing that scammers do to initiate a spoof email, is to have an active email address, obtained by purchase, scraping or by using malware.
As for the latter, a malware that infects someone's device, can collect the victim's address book and other contact information. It's these information that may lead to the scammer in sending you the spoofed emails. If you fall for the scammer's trick, you too will become the victim of extortion, which will then be past on to the contacts stored on your device.
By knowing how email spoofing work, you can create defenses in order to prevent such attacks from attacking you.
This can include, and not limited to:
- Use spam filters.
- Avoid clicking on unfamiliar links, or download anything that looks suspicious. Extra cautious is needed when opening shortened links.
- Masqueraded emails can contain bad spellings or grammar, and may only include text (without email design template).
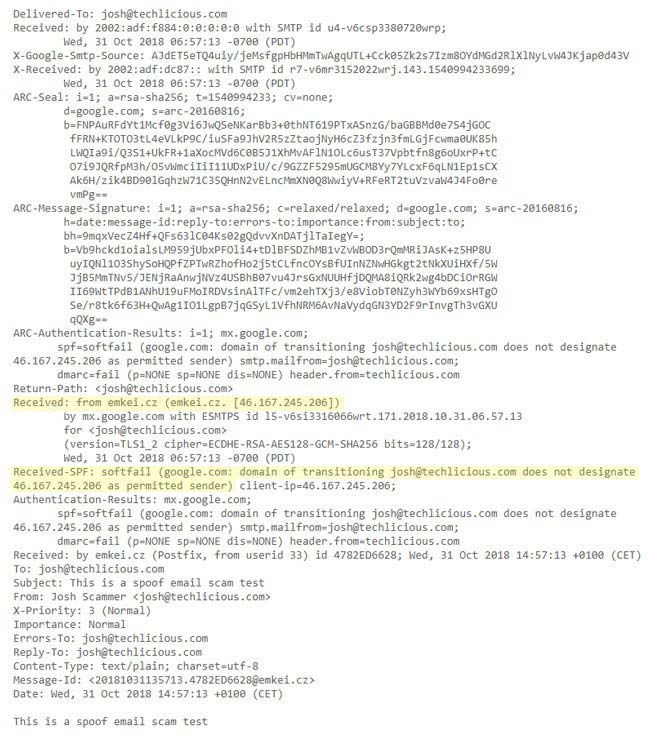
- Read the message headers, and trace IP addresses.
- Use tools like Gmail's Priority Inbox.
- Never enter sensitive information into web pages that are not secure (not using HTTPS).
- Audit using Sender ID, SPF (Sender Policy Framework), DKIM (Domain Key Identified Mail), and DMARC (Domain-Based Message Authentication, Reporting, and Conformance).
If you think you've fallen as victim of a spoofed email, there are a number of steps you can do to safeguard your accounts and personal information. But remember that time is crucial. You're literally racing against time to block all possible access you've inadvertently gave the scammers.
- Delete the spoofed email.
- Run antivirus and antimalware software to clean any infections.
- Change your passwords, especially your email accounts, and whatever you inadvertently gave the scammers.
- Turn multi-factor authentication whenever possible.
- If involving your bank accounts/credentials, contact the company that manages your data and explain your situation.
- Monitor for unknown activities, irregular charges, suspicious login attempts or unwanted social media posts.
- Notify the people that you have their contacts stored on your device.