The tech world is still developing, and there is no end to it as long as the technology that powers it continues to advance.
And as long as there is a target to be targeted, malicious actors will continue to create malware to spy, if not destroy the systems. And this time, researchers at Check Point Research discovered a malware that is uniquely destructive, and that a single click can result to a whole catastrophe.
The scary part of this malware is how it can spread extremely fast, and along the way, how it can also wipe everything in its path.
And it can do that 666 bytes at at time.
Azov is a particularly aggressive form of malware, and that it can infect devices ranging from personal computers, smartphones, and also tablets.
We took a look at #Azov #Ransomware — a new destructive data wiper:
- Manually crafted in Assembly using FASM
- Multi-threaded intermittent overwriting (looping 666 bytes) of original data content
- Effective, fast, and unfortunately unrecoverable data wiper pic.twitter.com/RGgscpSYXE— Check Point Research (@_CPResearch_) November 2, 2022
What makes it particularly disturbing is that, Azov has a unique capability of writing its own code.
Azov's code-writing capabilities makes it easier for the malware to infect the files used to launch and run applications, and effectively wipe victims' devices clean with random data.
What's more, the ability also helps it evade detection by creating a completely different code each time it corrupts one of victims' devices.
This trait sets Azov apart from most malware and ransomware out there in the wild.
According to the report, Azov is a polymorphic malware.
When it was discovered by the researchers at Check Point Research, there are two different versions of Azov.
They share most of their capabilities, but the newer version uses a different ransom note, as well as a different file extension for destroyed files (.azov).
According to the researchers, the Azov malware spreads from one device to another through clickbait campaign.
In an example, malicious actors can send greeting cards seemingly addressed personally to the victims.
Clicking on the online greeting card will quickly download Azov, and before victims know what's going on, the devices can be wiped clean.
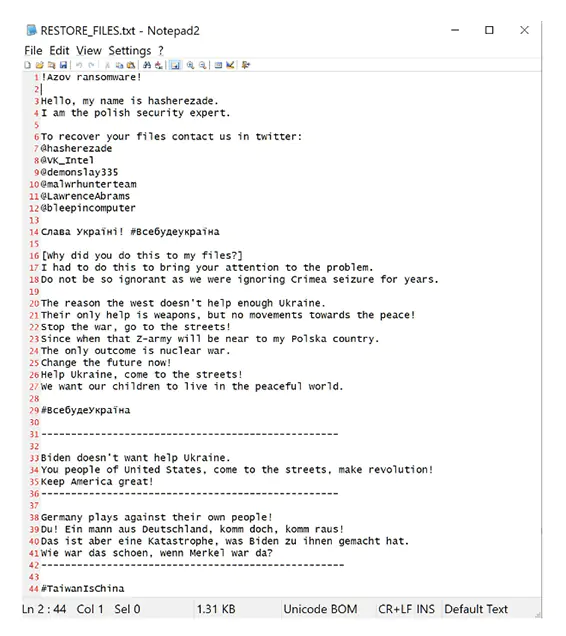
According to the researchers at Check Point Research in a blog post:
Azov has an "appetite for destruction." But what makes it worrying is its polymorphic ability.
Because Azov can evade detection, this led to a surge of publicly available files infected with Azov.
"Every day, hundreds of new Azov-related samples are submitted to VirusTotal, and as of November 2022, has already exceeded 17,000," the researchers at Check Point Research said.
To prevent Azov, or any form of ransomware attacks, the researchers suggest people to backup their data, and practice their cyber awareness.
More importantly, people should always update their software and to patch any weaknesses in their system, strengthen user authentication, and use anti-ransomware solutions in order to utilize better threat prevention.
