
As more data is put on the internet and with the increasing demand of remote working, cloud-based technologies started to pick up their pace fairly quickly.
Following this trend, hackers too are shifting their targets to not only target personal computers and those inside corporate networks, as they are also targeting cloud-based technologies, knowing that data that goes around there is abundance. And with 'Blackrota', things get particularly dangerous.
Blackrota is a malware that focuses on a security bug in Docker, the platform-as-a-service products that use virtualization to deliver software in packages called containers.
This malware that is created using the Go programming language (Golang), is a backdoor, first discovered by security researchers using their Anglerfish honeypot when it attempted to exploit an unauthorized-accessibility vulnerability in the Docker Remote API.
What makes Blackrota particularly dangerous is because of its heavy level of obfuscation. This makes the malware virtually unattainable to reverse-analyze.
Using substantial anti-detection tactics, the malware is difficult to examine.
As explained by researchers in a 360 Netlab post:
Researchers named the malware Blackrota, because of to its command-and-handle (C2) domain identify (blackrota.ga).
The Blackrota backdoor when it was found, only offered for Linux, in Executable and Linkable Format (ELF) file format, and supports equally x86/x86-64 CPU architectures. ELF is a widespread regular file format for executable files.
The researchers said that Blackrota is configured and compiled based on geacon, a CobaltStrike Beacon implemented in Go. This is a kind of beacon is usually used by malware to converse with a C2 server, asking for guidelines or to exfiltrate gathered information.
However, the researchers realized that Blackrota only implements some of the key functions in the original CobaltStrike Beacon.
"Unlike the original geacon, Blackrota uses gobfuscate to obfuscate the source code before compiling. gobfuscate is an open-source tool for Go code obfuscation, which can obfuscate the following elements of Go source code with random character substitutions," the researchers found.
This gobfuscate also replaces all strings used in the code with XOR encodings. What this means, it assigns each string an XOR Decoding function that dynamically decodes strings during program execution. Because Go uses fully-static links to build its binary files, the gobfuscate makes the codes packed into very large binary files, making reverse-analysis extremely difficult.
"The biggest obstacle to reverse analysis is that the function names, type names, and method names are obfuscated into meaningless random characters in the source code of the third-party packages."
"With thousands of random string-named functions and a large number of randomly-named data types, methods, and global variables, we could not be sure what third-party Go packages were used inside the sample, making the reverse analysis almost impossible to move forward," the researchers added.
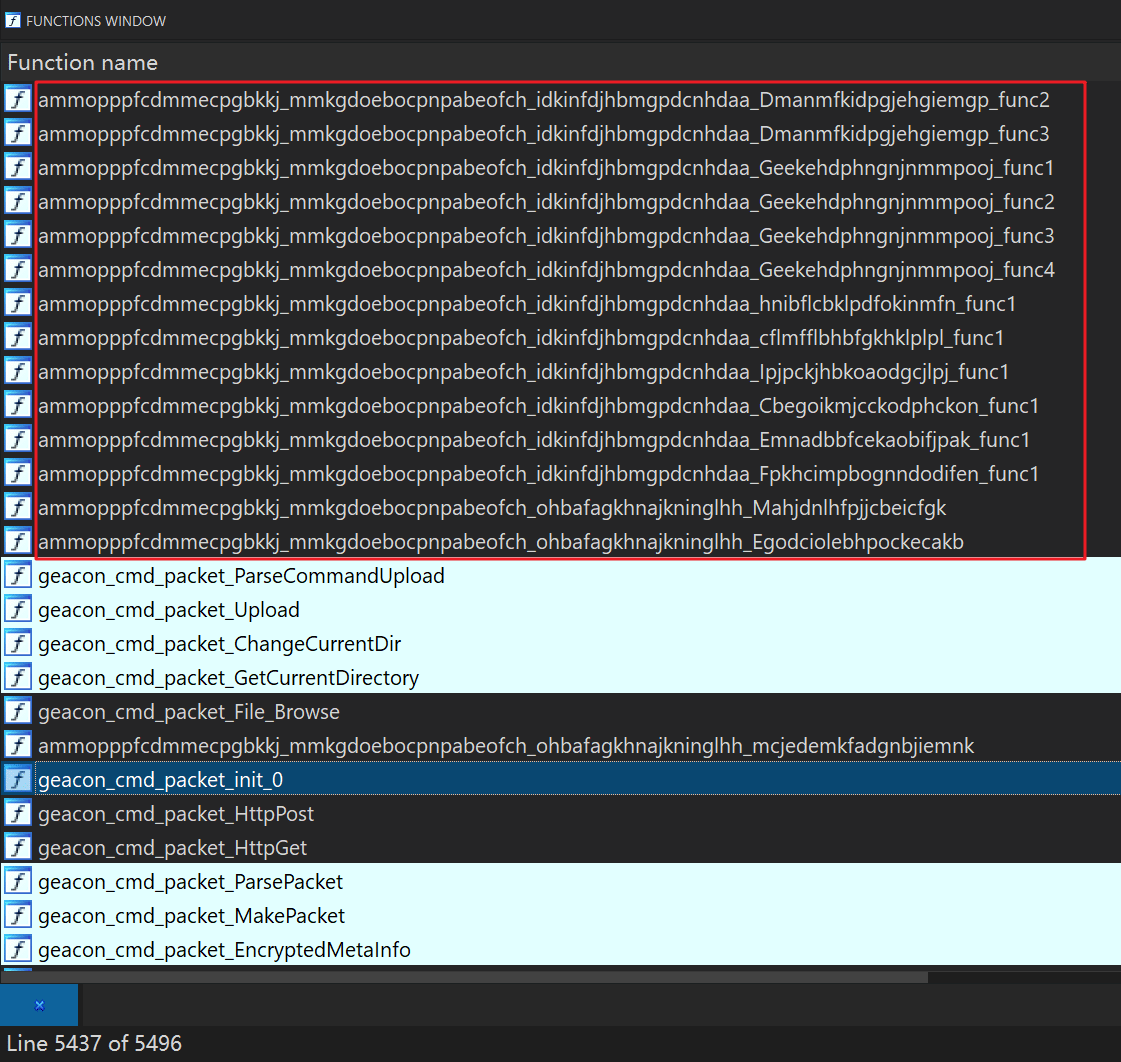
Fortunately for the researchers, the Go language has a mechanism that packs RTSI (Runtime Symbol Information) and the RTTI (Runtime Type Information) into the binary in a way that data cannot be stripped.
Through this, researchers can reverse engineer the Go binaries for analysis.
"Generally, the recovered RTSI and RTTI will lead us to the corresponding open-source package, we can then read the source code of third-party packages, which will further increase the efficiency of reverse analysis," the researchers said.
Researchers stated that obfuscated malware written in Go is rare, but has been heard of.
The EKANS ransomware for example, is one of the gew. The ransomware that is also created in Golang was earlier uncovered making use of a similar obfuscation technique as Blackrota.
Due to the malware's ability to hide its original intentions and payload, the researchers warned that these types of malware can create headaches for security defenders.
“The obfuscation method of Blackrota and EKANS makes new troubles for reverse examination,” claimed researchers. “As the Go language becomes more popular, additional and a lot more malware will be penned in Go in the future…we will retain an eye on what is likely to come about.”
The lesson here is that, hackers are increasing their efforts to target cloud-based technologies at a larger scale than before.
Companies, web developers, and engineers running Docker systems are advised to review the official Docker documentation to make sure they have secured Docker's remote management capabilities with proper authentication mechanisms, such as certificate-based authentication systems.