
Signal was one of the pioneers of secure messaging apps, and things were looking good.
With former NSA contractor Edward Snowden and then billionaire Elon Musk among others, recommending Signal, the app has indeed experience huge popularity. Millions of people who are looking for an encrypted messaging app, are signing up to Signal.
Making things even better for the messaging app, the WhatsApp exodus has indeed benefited it handsomely.
Following the trends, the authorities and the governments may have more to be worried about.
More than ever, they need to have some sorts of forensic techniques to access Signal messages.
Fortunately for them, according to court documents first obtained by Forbes, they do have the ability to steal messages from encrypted messaging apps.
It is reported that the FBI may have a way to access Signal's encrypted messages, even when they are behind the lockscreen of an iPhone.
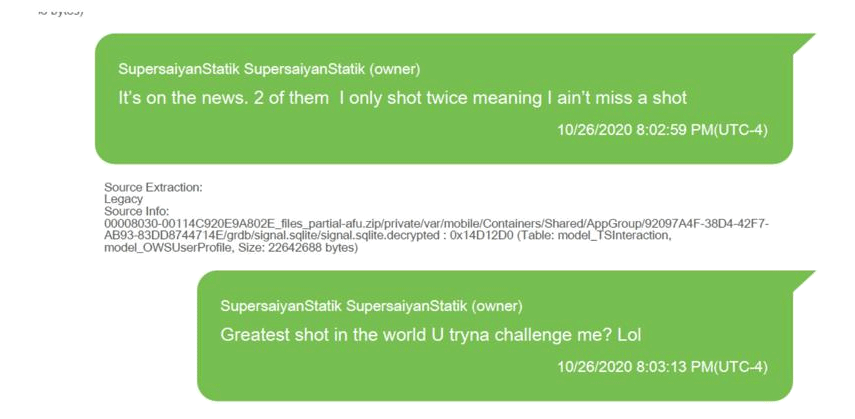
The clues were revealed by Seamus Hughes from the Program on Extremism at the George Washington University, based on court documents, with other documents showing screenshots of Signal messages between men accused back in 2020, of running a gun trafficking operation in New York.
In the Signal chats obtained from one of their phones, the authorities found that they were not just discussing weapons trades but attempts for murders too. That according to the documents, which were filed by the U.S. Department of Justine.
And not only that, as the documents show that there is also some metadata, indicating that not only the authorities could have decrypted Signal's encryption, but also extracted the messages.
The authorities were reportedly able to do this using “partial AFU,” or “after first unlock.”
AFU describes a state where an iPhone that is locked, but has been unlocked once and has not turned off since then.
In this AFU state, the authorities were allegedly capable of extracting Signal's data because the encryption keys for the encrypted messages are stored inside the iPhone's memory.
What this means, the authorities were able to use their hacking tools to exploit this state, retrieve the keys, and using them, start cracking the private data inside the device.
Apple declined to comment on this case, but pointed Forbes to its response to previous research regarding searches of iPhones in AFU mode, in which the company noted people must require physical access to the device they want to hack, and were costly to do.
This was also suggested by a Signal spokesperson.
“If someone is in physical possession of a device and can exploit an unpatched Apple or Google operating system vulnerability in order to partially or fully bypass the lock screen on Android or iOS, they can then interact with the device as though they are its owner," the spokesperson said.
“Keeping devices up-to-date and choosing a strong lock screen passcode can help protect information if a device is lost or stolen.”
Speculations suggested that the FBI was using tools like the GrayKey, made by Grayshift, an Atlanta-based startup, or the Cellebrite UFED from Israel.
These two apps arethe most prominent iPhone forensics tools used by the agency.
When Signal co-founder Moxie Marlinspike commented on the Cellebrite claims in December 2020, he called it “amateur hour.”
But whatever tools the FBI used to crack the Signal app in this case, and whatever they did, they were certainly not amateurish.