
The popular Signal app uses end-to-end encryption, as well as the proprietary open-source encryption protocol called 'Signal Protocol'.
This way, the app can keep messages and attachments as safe as possible from third-parties and unwanted eyes. This also prevents anyone from breaking into users' conversation, or access user data when they are being shared on the platform.
This fact makes Signal the popular messaging app for those who care about privacy. Twitter founder Jack Dorsey advocates it, and so does former NSA contractor Edward Snowden.
But this time, the Signal's end-to-end encryption has been broken.
That claim was made by the forensic-tool creator Cellebrite, that said it worked "tirelessly to empower investigators in the public and private sector to find new ways to accelerate justice, protect communities, and save lives."
But there is catch.
Long story short, Cellebrite needs physical access to the target device that has the Signal app installed.
In the original post cached by Archive.org before it was edited out by Cellebrite from its page, explained how it managed to break Signal:
Once the decrypted key is obtained, we needed to know how to decrypt the database. To do it, we used Signal’s open-source code and looked for any call to the database. After reviewing dozens of code classes, we finally found what we were looking for:
After finding this, we simply ran SqlCipher on the database with the decrypted key and the values 4096 and 1 for page size and kdf iterations. By doing so we managed to decrypt the database.
But Signal's encryption goes more than just that, as Cellebrite found that attachment files and messages are also encrypted, and this time, way harder to crack.
Looking at the shared preferences file, Cellebrite found the 'data' field which contains an encrypted JSON file. Decrypting this file revealed the decryption keys.
And by analyzing Signal's 'ModernKey' and turn it with 'data_random' values into the decryption keys, Cellebrite found a little piece of code that shows how the keys are generated, and that is by using the HMACSHA256 algorithm.
HMACSHA256 is a type of keyed hash algorithm that is constructed from the SHA-256 hash function and used as a Hash-based Message Authentication Code (HMAC). The HMAC process mixes the secret key right within the message data, hashes the result with the hash function, to then mix that hash value with the secret key again, to then apply the hash function a second time.
The output hash is 256 bits in length.
Knowing this, the Israeli company finally knew what decryption algorithm to use.
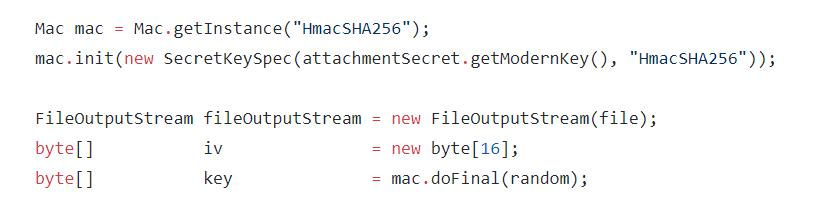
"We used our decryption key with the AES encryption in CTR mode and decrypted the attachment files," Cellebrite said.
Using the link between the messages and the attachments, "we can add the attachments to the conversation and see the chats as they were seen by the chat participants."
"Decrypting Signal messages and attachments was not an easy task. It required extensive research on many different fronts to create new capabilities from scratch."
The initial post, which was stored on the Internet Archive, Cellebrite "cracked the code" by reviewing Signal's own open source protocol and using it against it.
To promote this, the company has updated its Physical Analyzer product page with the new capability.
Cellebrite's Physical Analyzer is a tool that helps users organize and process data lifted from a target phone. And Cellebrite has updated the page to show how clients can use it to decode information and data from Signal.
"Law enforcement agencies are seeing a rapid rise in the adoption of highly encrypted apps like Signal, which incorporate capabilities like image blurring to stop police from reviewing data," wrote Cellebrite.
"Decrypting Signal messages and attachments was not easy. It required extensive research on many different fronts to create new capabilities from scratch."
Security experts quickly dismissed Cellebrite's claim. This is because in order to access data and run a forensic analysis, Cellebrite's clients need full access to a target's phone, whether through a passcode, touch ID, or face recognition.
After the news circulated, Moxie Marlinspike, Signal's creator, tweeted that Cellebrite "could have also just opened the app to look at the messages."
This (was!) an article about "advanced techniques" Cellebrite uses to decode a Signal message db... on an *unlocked* Android device! They could have also just opened the app to look at the messages.
The whole article read like amateur hour, which is I assume why they removed it.— Moxie Marlinspike (@moxie) December 11, 2020