The fear for the coronavirus threatens the world, and apparently also the digital world.
While tech companies are doing what they can for their part. Hackers too are piggybacking the trend to spread their malicious campaign, including impersonating WHO.
And here things go a step further with hackers targeting even more of those who are keeping a close eye on the coronavirus 'COVID-19' disease.
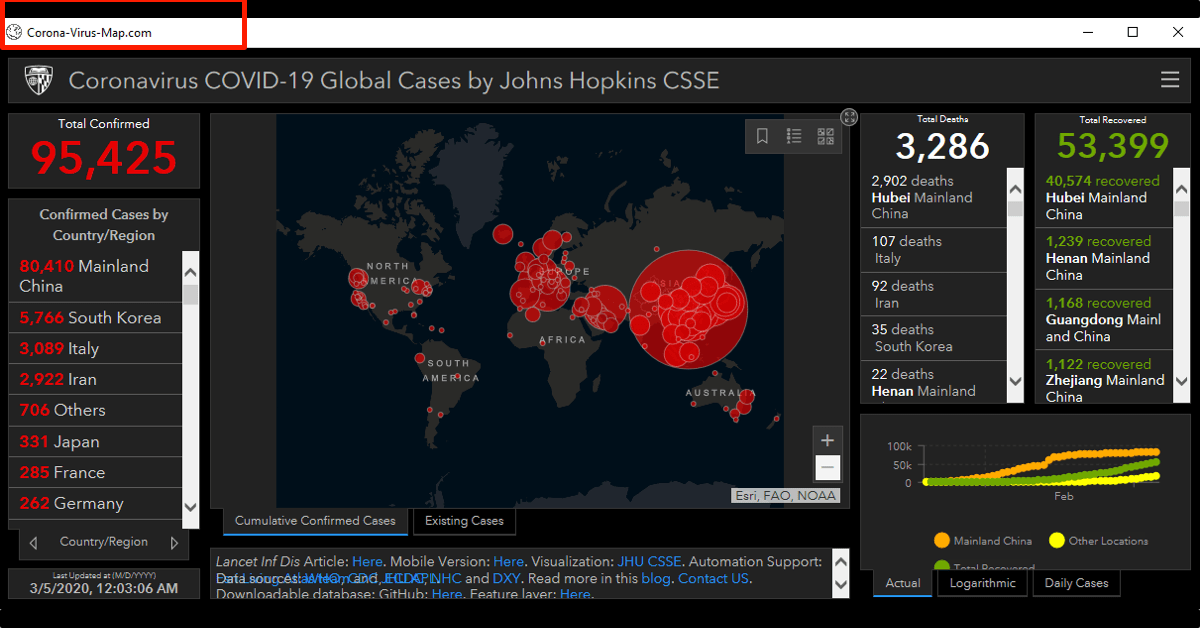
Several organizations have made dashboards to keep track of the virus. These dashboards provide interactive maps to show the spread of the disease.
Johns Hopkins' COVID-19 dashboard for example, has been a go-to source for many people who want to stay up to date on the virus. Knowing that these websites have a lot of viewers, hackers is trying to benefit from the trend.
According to Shai Alfasi, a security researcher at Reason Labs, hackers have managed to use these kind of maps to steal information of users, including usernames, passwords, credit card numbers, cookies, and other information.
To do this, hackers designed websites dedicated to show maps related to the coronavirus.
But when visiting the websites, visitors are prompted to download an application to see the updated data for the situation.
The application doesn't need installation. When downloaded and executed, the application will show a genuine map of how the COVID-19 is spreading. However, the websites have different URLs or different details from the original source.
And in the background, the application generates malicious binary file and install it on the victims' computers.
Initially, the malware only affects computers with Windows operating system.
Alfasi suspects that attackers may work on a new version to affect other systems too.
Alfasi explained that the method uses a malicious software known as AZORult.
First found in 2016, researchers noted that AZORult can also steal financial data, credentials, as well as cryptocurrencies and more.
AZORult is commonly sold on Russian underground forums for the purpose of collecting sensitive data from infected computers. The malware is one of the most commonly bought and sold in the underground forums, despite it's relatively high price tag.
Hackers buy this malware for its broad functionality, as explained by cybersecurity company Trend Micro, a variant of this malware can also act as a downloader of more malware.
It can also create a new, hidden administrator account on the machine to set a registry key to establish a Remote Desktop Protocol (RDP) connection.
Considered a high-risk trojan, AZORult is known to spread via emails that typically contain deceptive text to trick users into opening attached files.
And in the coronavirus-infected world, hackers spread AZORult by using the virus map as their deception.