
If a computer system is a country, then the firewall is its borders and the antivirus software is the police.
Hackers (outsiders without permit) that want to enter a computer, needs to pass through the firewall and evade antivirus protection. That is possible by sending a spy, or in this case, a malware. If installed, the malware can continuously send information as long as the police isn't catching it.
If the threat of the coronavirus epidemic wasn’t enough, people of the web have to watch out for a novel coronavirus-themed hacking campaign.
According to new research from security firm Check Point, coronavirus-themed domains are 50% more likely to spread malicious activity than other domains.
There have been over 4,000 coronavirus-themed domains registered since January. Out of that many, 3% were flagged as malicious, and another 5% as suspicious.
This is 50% higher than the malicious rate of all other domains registered in the same period of time, including the yearly Valentine’s Day scams.
"Many of these domains will probably be used for phishing attempts," warned the researchers. "An outstanding targeted coronavirus themed phishing campaign was recently spotted targeting Italian organizations, hitting over 10% of all organizations in Italy."
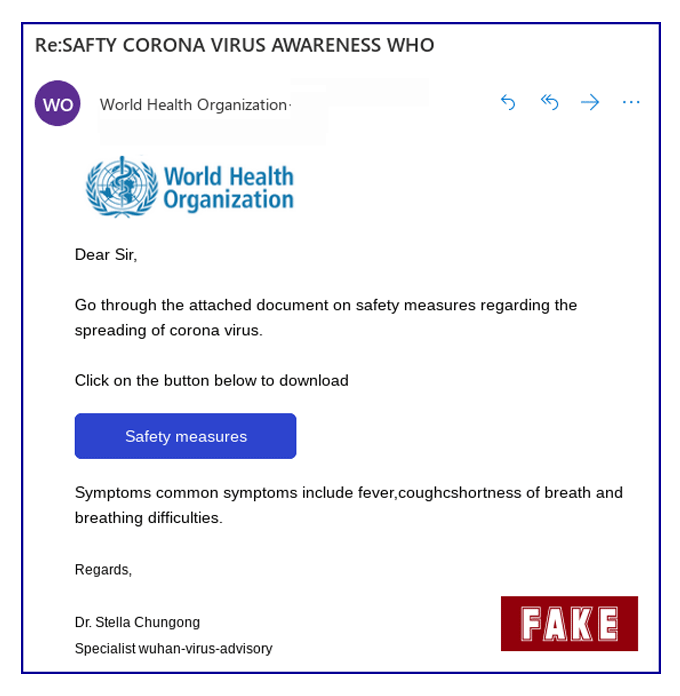
The campaign in question attempts to trick users into downloading a malicious file disguised as “a document that includes all the necessary precautions against coronavirus infection” prepared by the World Health Organization.
In reality, victims are actually downloading a banking Trojan, which can harvest their personal information and credentials.
Fake coronavirus news is spreading faster than the virus itself.
The pressure burdened on messaging apps, social media and the internet in general have caused any message with the word "coronavirus" very much appealing to read and picked up.
This is where hackers slipped in to launch their malicious campaign by piggybacking the trend.
Read: Indonesia's First Coronavirus Patients Suffer More Damage From The Internet Than The Virus Itself
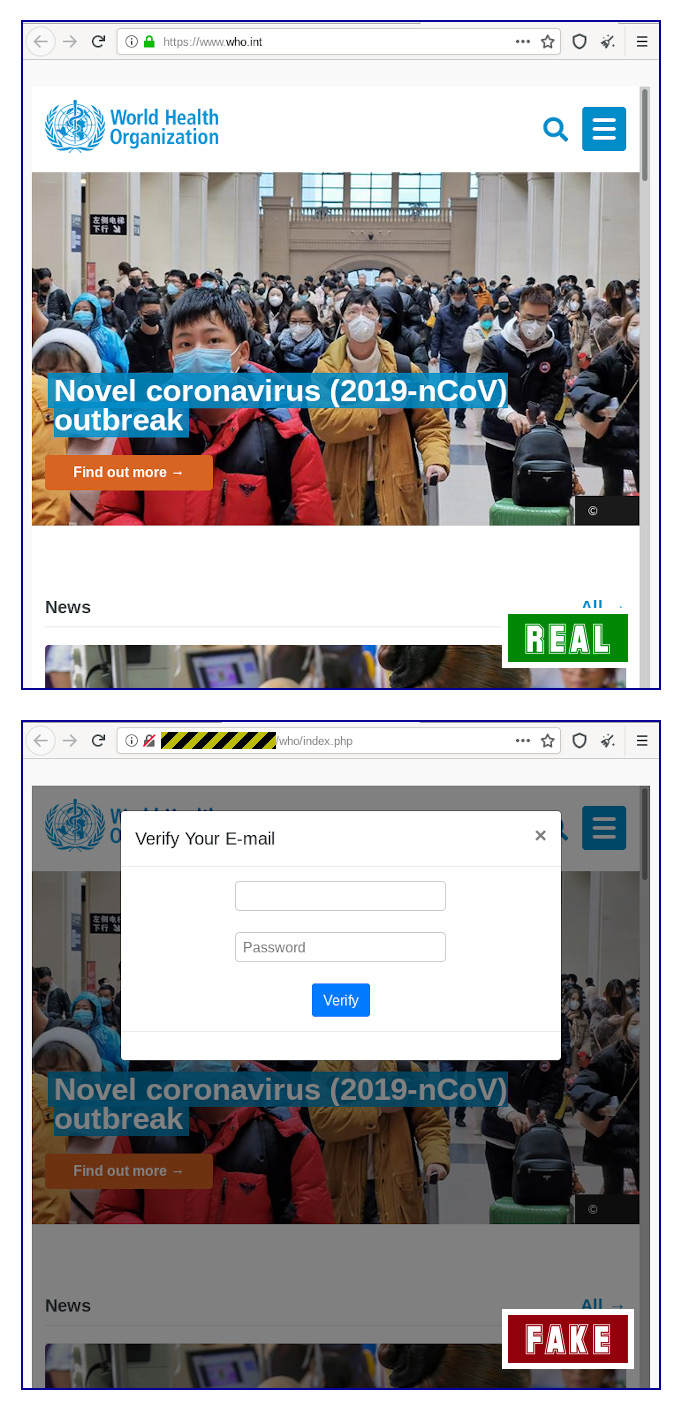
One of the ways hackers manage to launch this campaign, is by sending millions of coronavirus-related phishing emails to unsuspecting people that are under cover of the looming pandemic.
To make their emails legitimate, hackers use the email to direct their victims to the website of the World Health Organization (WHO), where the information was originally published. But as a matter of fact, according to a report from Sophos the website is a rip-off copy of the real WHO website.
At their website, hackers added methods where they can gather users' credentials, by adding a popup email password box on the main page. Using this method, the hackers hope that because their website looked exactly like the real thing, unsuspecting victims would simply enter their email credentials.
The hackers even went as far as localizing their phishing email. Like for example when targeting people in Italy, the email is written in Italian, pretending to quote an Italian official from the WHO, referencing known virus infections in Italy, and urging Italians to read a particular document.
This essentially makes the email appealing and click-worthy.
The email also contains macros, meaning that it has embedded software module capable of being used to spread malware.
According to Sophos, enabling macros would trigger a series of stages that ultimately result in infection by Trickbot, a well-known strain of Windows malware that is commonly used by hackers as a precursor to a full-blown ransomware attack.
Further reading: Hackers Use WHO's Name To Deliver FormBook Malware Through Emails