
WebKit powers Apple's Safari, and Chrome powers Google's Chrome web browser and many more. And bugs made them a security risk to users.
According to a report from cybersecurity firm Confiant, after extensively tracking the group dubbed 'eGobbler', the researchers discovered the group's malvertising campaigns.
Found back in 2018, the campaign leverages flaws found on the two popular browser rendering engines.
The flaw was patched after Google released a Chrome 75 update in June.
But since that time, the group's campaign spread to exploit WebKit's vulnerability in JavaScript to generate successful redirects. Fortunately, Confiant said that the exploit (CVE-2019-8771) has been fixed by Apple in iOS 13 and Safari 13.0.1 after the bug was private disclosed to the company on August 7th.
What makes eGobbler's campaign unique is that, it exploits a JavaScript function that’s executed every time a user presses a key on the keyboard.
"Also noteworthy is that the campaign behind this payload had specifically targeted some web applications with text areas and search forms in order to maximize the chances of hijacking these keypresses."
Putting their malvertising campaign there, the group was able to bombard users with pop-ups when users interact with a site by pressing a key.
The attack was considered insidious because it impacts all users on both mobile and desktop.
The attack was also considered a zero-day vulnerability because it bypassed built-in security protections to show potential victims intrusive pop-up ads, redirect users to malicious sites, all without users' interaction.
This made the campaign to have served a staggering 1.16 billion malware-ridden ads to Chrome and Safari users, between August 1 to September 23.
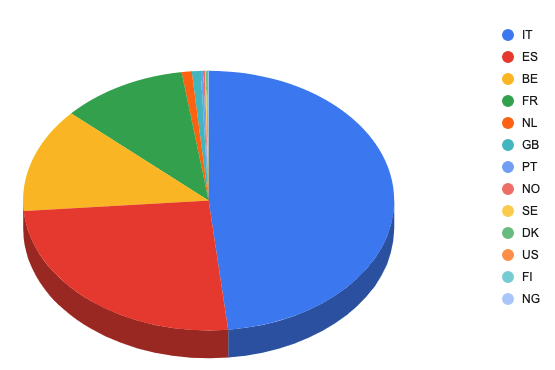
According to the data, the primate targets of the campaign were those from European countries, like France and Italy.
To make the attack efficient, the eGobbler group often use CDNs for payload delivery. Whenever available, the group will leverage subdomains that look innocuous or include familiar brands.
This finding by Confiant wasn't the first time eGobbler has spread issues with malicious ads.
Previously, in April 2019, the group exploited a Chrome for iOS exploit (CVE-2019–5840) to circumvent the browser‘s built-in pop-up blocker to deliver fake ads to 500 million sessions of users from the U.S. and Europe in just under a week time.
While the flaws have been patched, history has proven that more flaws will be discovered in the future.
For this reason, as always, users of the web should protect themselves from malicious campaigns of any type by becoming more vigilant of their browsing activity, and to always keep web browsers updated to their newest versions.