
Spying on other governments' entities no longer involve sending spies behind enemy lines. Instead, governments can employ hackers.
Or, they can simply use spyware, like one created by Israeli developer NSO Group. Called the Pegasus, the sophisticated malware has been targeting the Apple ecosystem due to its widespread popularity among activists, dissidents, journalists and political opponents.
While others do exist, like the Predator, which originated at a European company called Cytrox, and Reign, which is thought to have been used by both the NSA and GCHQ, the Pegasus is arguably the most widely known of such tools.
After many years hunting high-profile figures around the world, the researchers at Kaspersky’s Global Research and Analysis Team (GReAT) have found a solution.
In a website post, the researchers said that they have developed and released a lightweight method to help Apple iPhone users at risk of being targeted by the Pegasus spyware and other similar malware, by detecting its presence on their devices.
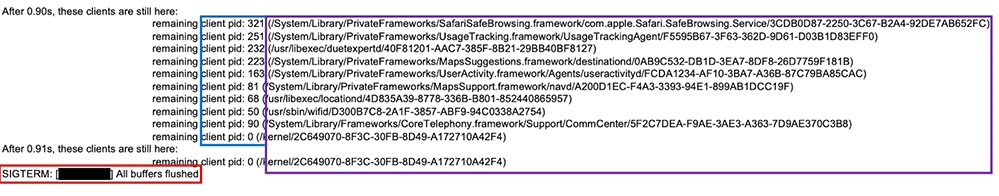
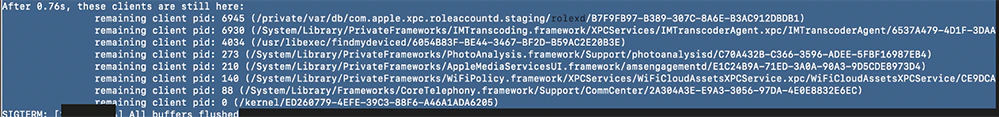
Kaspersky claims its tool is able to reveal the presence of Pegasus through analyzing a previously unexplored forensic artefact called Shutdown.log.
This file is an unexpected system log stored within an iOS device’s sysdiagnose archive, which retains information from each reboot session.
As a result, the GReAT team managed to find anomalies linked to Pegasus become apparent if an infected user reboots the device.
Among the traces found were instances of sticky processes that impeded reboots, and infection traces previously observed by other cybersecurity researchers.
The team also observed a that the Pegasus malware shares a common infection path that mirrored those seen in Predator and Reign infections.
This suggests that the methodology also holds potential for identifying those infections.
"The sysdiag dump analysis proves to be minimally intrusive and resource-light, relying on system-based artefacts to identify potential iPhone infections. Having received the infection indicator in this log and confirmed the infection using Mobile Verification Toolkit (MVT) processing of other iOS artefacts, this log now becomes part of a holistic approach to investigating iOS malware infection," said Kaspersky GReAT lead security researcher Maher Yamout.
"Since we confirmed the consistency of this behaviour with the other Pegasus infections we analysed, we believe it will serve as a reliable forensic artefact to support infection analysis."
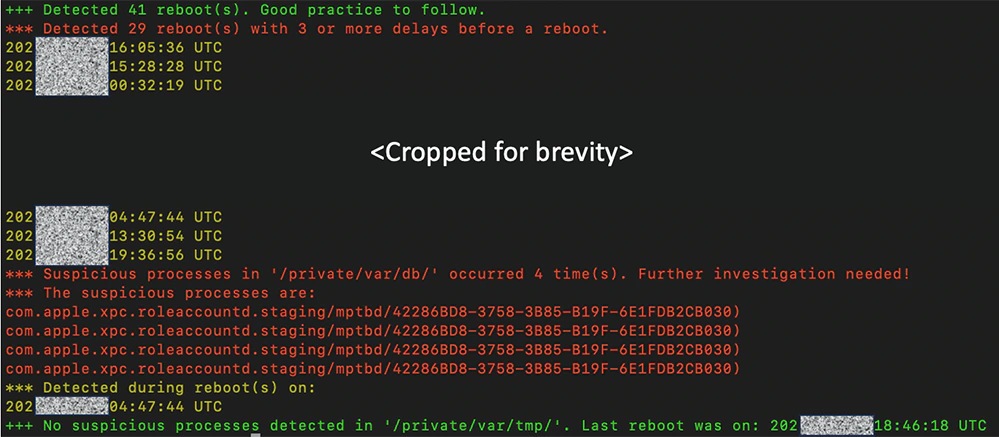
The tool in question is a Python3 script that extracts, analyses and parses the Shutdown.log artefact.
The team has made the tool available to the public on GitHub.
Beside Apple devices, the tool can also run on Windows and Linux.
The team advises users who believe they may be at risk of orchestrated attempts to spy on them through their devices to take a number of additional steps:
- Reboot the device daily, because the zero-day exploits like the Pegasus aren't historically persistence if rebooted.
- Use Apple’s Lockdown Mode.
- Disabling iMessage and Facetime, which are both heavily used as an exploitation vector.
- Upgrade and update the operating system to patching devices quickly whenever Apple releases new security updates.
- Being cautious about online behavior, which include avoiding clicking on links received in messages, for example; and checking backups and sysdiagnose regularly.
Read: People Who Aren't Criminals Have 'Nothing To Be Afraid Of' When Being Surveilled