
Web browsers are literally the gates to the World Wide Web, and because of that, they need to support a variety of formats.
Of the the many, includes the WebP format. This relatively new format is a raster graphics file format developed by Google intended as a replacement for JPEG, PNG, and GIF file formats. It supports both lossy and lossless compression, as well as animation and alpha transparency.
WebP promises a lot of things, especially on the web, where images on websites should be small in size to ensure a speedier website and experience.
This time, a severe bug is found, and it affects all major web browsers.
From Google Chrome, Microsoft Edge, and other Chromium-based web browsers, as well as Mozilla Firefox and Apple’s Safari browser, all those browsers have been impacted by a single zero-day vulnerability.
Once exploited, the flaw, tracked as CVE-2023-4863, could lead to system crashes and arbitrary code execution, where hackers can gain control over an infected device.
First identified by researchers at The Citizen Lab, a research arm of the University of Toronto, the bug resides on the libwebp, the code library used to render WebP images.
The issue resides in a heap buffer overflow in the WebP image format.
The bug allows hackers to send specially crafted data to cause the web browsers to behave in unexpected ways.
The library here, is where the encoding and decoding takes place. The libwebp is essentially the translator that helps web browsers understand how to display a WebP image when told to. Here, the codec has has a heap buffer overflow, which could allow attacker to craft a malicious WebP image that, when viewed, exploits this vulnerability to harm your computer or steal information.
The root of the issue lies within the BuildHuffmanTable function which was first introduced in 2014, the function is used to verify if the data is accurate.
The vulnerability can occur when more memory is allocated if the table isn't sufficiently large for valid data.
WebP is a popular image format used by many sites on the Internet, due to how well it can compress images without losing too much details.
Initially, Google actively promoted WebP though Google Chrome. And because of this, all Chromium-based browsers support the format.
Among all popular web browsers, Apple's Safari was the last one to adopt the format. The web browser only added support for WebP in 2020 with iOS 14 and macOS Big Sur.
Because the format is so popular, the bug could potentially jeopardize the security of billions of internet users.
This is why The Citizen Lab researchers, who subsequently informed Google and Apple of the vulnerability’s existence, received quick response from both companies.
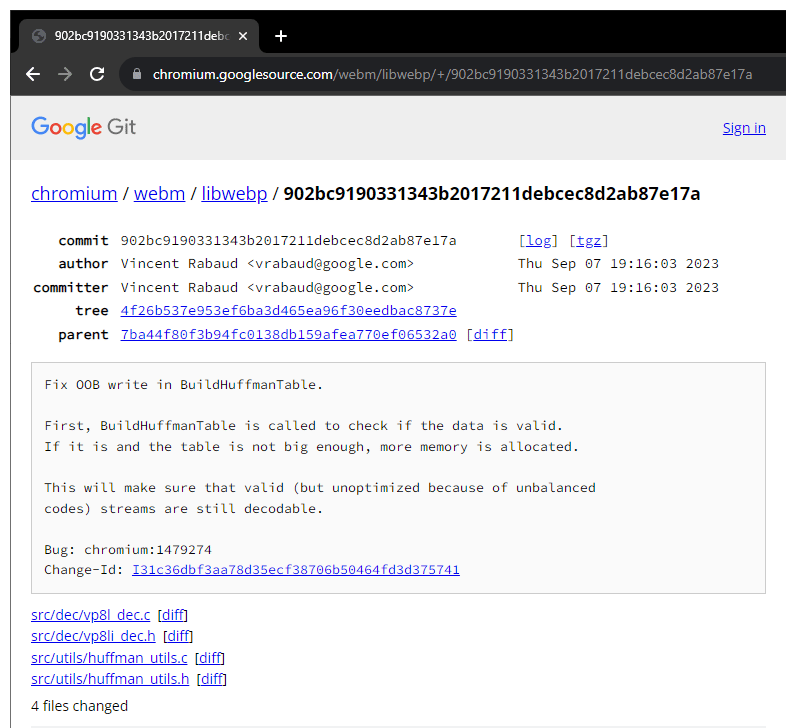
Google was first, and was swift in its response. The company quickly rolled out an update to its Chrome web browser. Apple was also quick, and have also pushed an update to secure its Safari web browser.
Mozilla is not far behind, and has created several updates for several versions of its Firefox browser and Thunderbird email client.
Microsoft came next, and has released an update to its Edge browser, after it was notified by the Chromium team.
Other web browsers, like Opera, Vivaldi, and Brave, have also released their own patch.
It's worth noting that before this, The Citizen Lab also discovered that the Apple vulnerability is being abused by the NSO Group, a controversial company based in Israel, to upload its Pegasus spyware onto iPhones, through an exploit chain dubbed the 'BLASTPASS.'
Read: Apple Fixed 'BLASTPASS' IOS Bug, Which Allowed The Pegasus Malware To Sneak In