A web shell is a lightweight, malicious web-based shell-like interface popular among hackers all around the world.
What appears to be a simple tool, web shell enables its users to access a target web server by way of a web browser that acts like a command-line interface. it allows its users to issue commands, and perform privilege escalation in a target web server.
It also allows users to upload, delete, download, and execute files on a target web server.
Because it allows remote access and control, and allowing the execution of arbitrary commands, web shell is often considered one of the most versatile remote access trojan.
Again, web shell my seem to be a simple app with a simple interface. But in the hands of an experienced hacker, the tool can create a lot of damage.
In other words, web shell can be considered the Swiss Army knife for hackers.
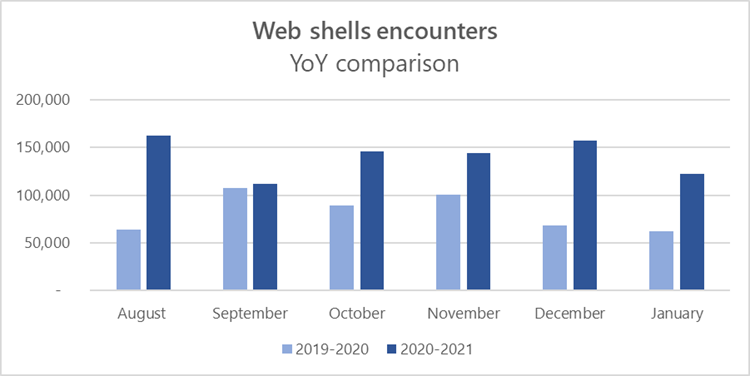
And here, Microsoft said that it is seeing a big increase in the use of web shells.
In a blog post, Microsoft said that:
"The escalating prevalence of web shells may be attributed to how simple and effective they can be for attackers."
What makes web shell particularly dangerous is that, it can be programmed to target any language that the target server supports.
Commonly, web shells are written in PHP, due to the massive popularity of the server-side programming language.
However, web shells can also support Jakarta Server Pages (JSP), Active Server Pages (ASP), ASP.NET, Python, Perl, Ruby, and Unix shell scripts.
And within each supported language, there are several means of executing arbitrary commands, and multiple means for arbitrary attacker input.
Hackers can also hide instructions in the user agent string or any of the parameters that get passed during a web server/client exchange.
Microsoft added:
The growth of web shell usage is a sign of how useful and powerful these seemingly simple programs can be.
In order to defend against web shell attacks, the first thing to do is getting the visibility into internet-facing servers using firewall software and endpoint solutions that use behavior-based blocking and containment capabilities.
"Behavior-based protection also provides post-compromise defense in scenarios where attackers are already operating and running commands on web servers," said Microsoft.
Organizations can also harden their systems against web shell attacks by taking the following preventive steps:
- Identify and remediate vulnerabilities or misconfigurations in web applications and web servers.
- Implement proper segmentation of your perimeter network.
- Enable antivirus protection on web servers.
- Audit and review logs from web servers frequently.
- Utilize firewall solutions, intrusion prevention devices, and network firewall.
- Check perimeter firewall and proxy to restrict unnecessary access to services.
- Practice good credential hygiene, and limit the use of accounts with local or domain admin level privileges.